PUA:Win32/SBYinYing is a potentially unwanted application (PUA) that is often bundled with certain cracked games. It may display ads to users or redirect them to potentially harmful websites, which puts it in the same line with adware and browser hijackers. Most often, user get infected with that malware after downloading cracked software.
PUA:Win32/SBYinYing Overview
PUA:Win32/SBYinYing is identified by Microsoft Defender as a potentially unwanted program. This detection is most commonly associated with a file named “EMP.dll”, which is typically found in pirated games. Torrents, especially those offering cracked games, are the main distributors of this malware. This is an ideal distribution method for malicious software because running cracked games often requires disabling antivirus software or adding the game to an exclusion list.
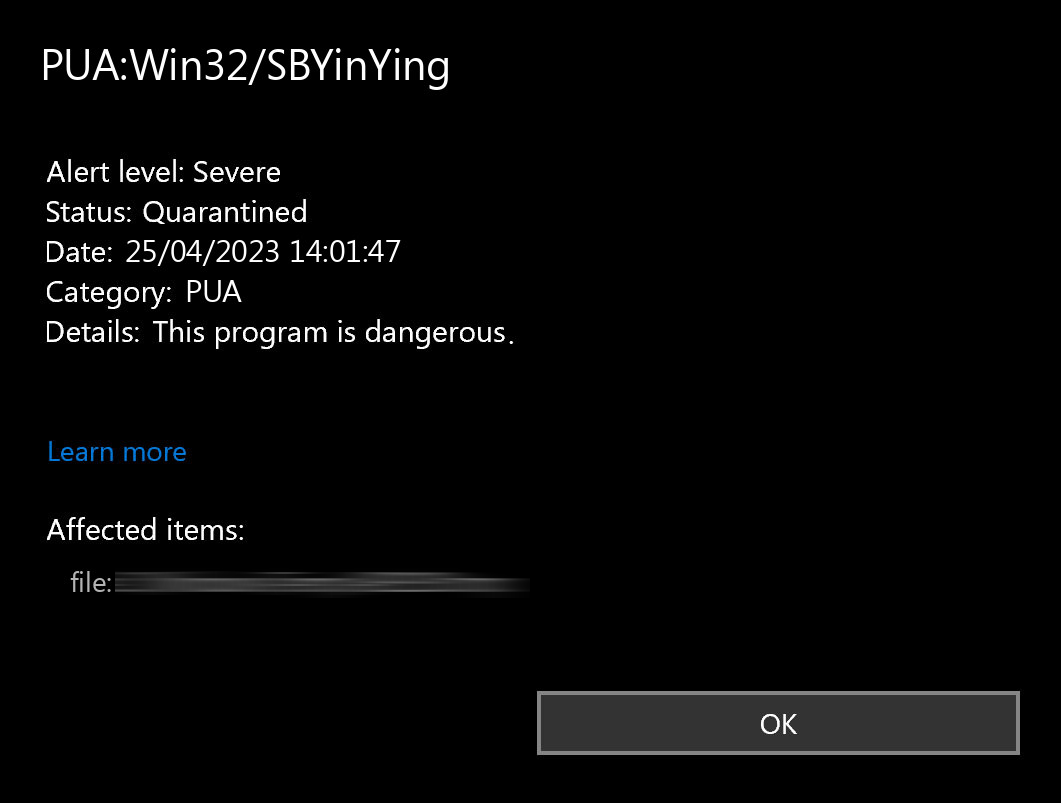
Once this PUA infiltrates a system, it starts doing its nasty job, particularly showing excessive ads and gathering basic information about the user. It is not as severe as regular spyware, but still creates a less than favorable situation for anyone who cares about privacy. And the aforementioned advertising behavior is what adds on top of that risk. Promotions that Win32/SBYinYing shows may contain phishing redirects, downloading links for unwanted programs or sometimes even straight up malware.
Technical Analysis
The previous information about PUA:Win32/SBYinYing provided a general overview, but to fully understand the nature of this threat, a more in-depth analysis is required. Let’s examine how this unwanted app behaves within a system using the “EMP.dll” file from a repackaged game as an example. While some behaviors of this software may be related to bypassing license checks, other actions raise significant concerns.
Execution
Since “EMP.dll” is not an executable .exe file, it requires another process to run it. In this case, a part of the installer calls for the rundll32.exe, a default process for launching dynamic-link libraries. The execution command looks like this:
C:\Windows\System32\loaddll64.exe loaddll64.exe 'C:\Users\user\Desktop\EMP.dll
The DLL file contains a section that may hold compressed or packed code. Similar to regular malware, PUA:Win32/SBYinYing performs standard checks to detect whether it is running in a virtual environment or a sandbox. It does this by examining certain system parameters, specifically:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Policies\Microsoft\Cryptography\Configuration
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\ComputerName\ActiveComputerName
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\Display
SBYinYing queries various system settings, including information about hardware (disks, volumes) and software (policy settings, cryptographic machine GUIDs, etc.). It will cease further execution shall any of these contain traces of virtualization or sandboxing.
Defense Evasion
The next step involves identifying and evading security solutions. The techniques used here are more typical for malware, than for unwanted programs. File obfuscation, data encryption, attempts to disable or modify security software, injection into legitimate processes – Win32/SBYinYing does all of this. Among other things, the malware checks the following locations:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\SecurityProviders
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\SecurityProviders\SaslProfiles
These places contain information about installed antivirus/anti-malware software. Typically, malicious programs change their behavior depending on which AV-vendor is present.
Privilege Escalation and Persistence
After basic checks, an unwanted program goes for escalating its privileges. It leverages legitimate processes like WerFault.exe and rundll32.exe, making this step relatively straightforward. As mentioned earlier, the malware uses rundll32.exe to execute the DLL library, allowing it to run malicious code embedded within the DLL. Additionally, the malware terminates the wmiadap.exe process with parameters /F /T /R, which appears to be an effort to evade detection or stop system monitoring. Here’s what the commands look like:
C:\Windows\System32\WerFault.exe C:\Windows\system32\WerFault.exe -u -p 1052 -s 460
C:\Windows\System32\WerFault.exe C:\Windows\system32\WerFault.exe -u -p 5188 -s 432
C:\Windows\System32\WerFault.exe C:\Windows\system32\WerFault.exe -u -p 2296 -s 484
WerFault.exe is a legitimate system process used for error reporting in Windows and Windows applications. In addition to leveraging this process, the malware creates scheduled tasks, enabling it to persist by running each time the system starts.
Network Activity
The malware exhibits notable network activity, making several DNS requests to connect to the internet. Some of the observed connections include:
TCP 40.88.32.150:443
TCP 65.9.73.63:443 (firefox.settings.services.mozilla.com)
TCP 54.187.157.95:443 (pipeline-incoming-prod-elb-149169523.us-west-2.elb.amazonaws.com)
10.216.185.205.in-addr.arpa
125.21.88.13.in-addr.arpa
130.155.190.20.in-addr.arpa
There are also numerous internal addresses that may be used to make the analysis harder. These connections suggest that the malware could be communicating with command servers, potentially exfiltrating data or receiving further instructions.
Does PUA:Win32/SBYinYing Steal Data?
While it’s theoretically possible for PUA:Win32/SBYinYing to steal data, in practice, this is unlikely. This unwanted app mostly works as adware, and the information it collects mostly serves for fingerprinting the system. Still, adware can redirect users to potentially dangerous websites, which in turn could be a source of more harmful malware. And that is when user data gets in risk.
This might explain why some users report that their Facebook and Steam accounts were compromised after PUA:Win32/SBYinYing was found on their systems. Another plausible explanation is the general risk associated with using pirated software. Using cracked games or software increases the likelihood that a user will eventually have their personal data stolen or files lost.
How to Remove PUA:Win32/SBYinYing?
To remove PUA:Win32/SBYinYing, it’s advisable to use advanced anti-malware software. Some users encounter difficulties when trying to eliminate this threat with Microsoft Defender. For this reason, I recommend using GridinSoft Anti-Malware as a tool to remove PUA:Win32/SBYinYing. You can follow the step-by-step guide below:

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

Additionally, I strongly recommend refraining from downloading pirated games and software, as this is the most common method of distributing malware. Not only is it dangerous, but it’s also illegal.