Polymorphic and Metamorphic Malware: the Comparison
In this article, we consider two types of pests: polymorphic and metamorphic viruses, which were designed to destroy the integrity of the operating system and harm the user. Before we find out what is the difference between polymorphic and metamorphic viruses, let’s figure out what is virus in general and where it originates.
What is a Polymorphic Virus?
To understand a polymorphic virus, let’s consider a persistent threat that constantly evades anti-malware. This threat creates similar viruses, seemingly regenerating itself. Its main target is the user’s device and data, adapting as much as needed to achieve its goal. In summary:
A polymorphic virus is a complex virus encrypted with a variable key, making each copy of the virus different from the others. The virus aims to evade anti-malware or scanners. While typical malware can be detected by anti-malware software, a polymorphic virus is designed to change its encryption keys. For example, if one user downloads a file from a website and another user downloads the same file, the two files will appear different to security programs.
Normally, a scanner or anti-malware could detect a virus through identical keys in different files. However, a polymorphic virus complicates this by using different encryption keys for different files. To detect polymorphic viruses, there are two primary methods: general description technology and an algorithm at the entry point. The general description technology runs the file on a protected virtual computer, while the entry point algorithm verifies machine code at each file’s entry point, employing software virus detection.
What is a Metamorphic Virus?
Let’s explore a metamorphic virus. This type of virus reprograms itself to evade detection. What does this mean? The virus transmits its own code and creates a temporary representation to outmaneuver antivirus software. Once it bypasses security, it rewrites itself into the normal code. Each copy of this virus is always different, making it difficult for anti-malware to detect.
A metamorphic virus transforms by editing, rewriting, and translating its own code. Its goal is to damage the computer while remaining unnoticed by anti-malware. Unlike polymorphic viruses, metamorphic viruses do not use encryption keys to alter their copies. Instead, the virus converts its existing instructions into functionally equivalent instructions when creating a copy. This transformation prevents the virus from returning to its original form, complicating the work of anti-malware programs. Two methods to detect metamorphic viruses are: using emulators to track them and geometric detection.
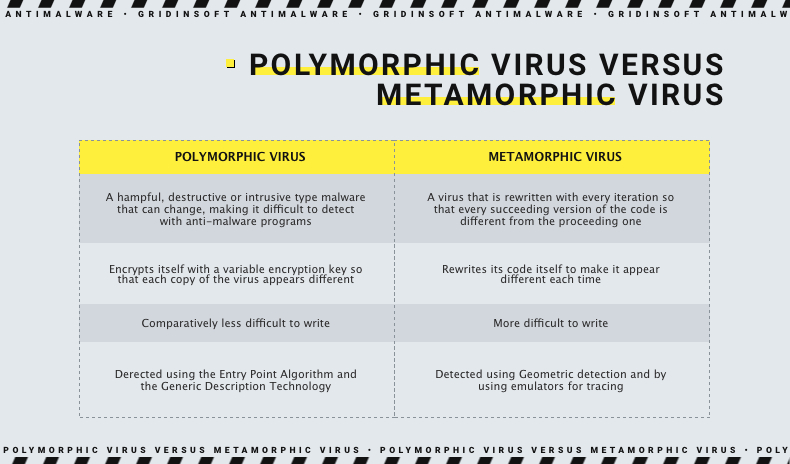
Difference Between Polymorphic and Metamorphic Virus
While these viruses are generally similar in that they attempt to circumvent the security system by altering their own codes, there is still a difference between them.
- Polymorphic virus involves changing each copy of its code to bypass anti-malware protection, while Metamorphic Virus with each iteration rewrites its own code.
- The polymorphic virus uses the encryption key to change its code, while Metamorphic Virus itself rewrites its code.
- Writing Metamorphic Virus is much more difficult for a programmer than creating a Polymorphic one, because you need to use several methods of conversion.
- Methods for detecting these two viruses are different. In the case of polymorphic viruses, we need such methods: general description technology and input point algorithms. And in the case of Metamorphic Virus, you need to use the following methods: the use of emulators for tracking and geometric detection.
How to remove Polymorphic or Metamorphic Virus?
In order to reduce the risks of infection and prevent threats, install an effective antivirus tool on your PC. Our Anti-malware is a great choice. Do not neglect your safety. Gridinsoft Anti-Malware is proper and reliable protection that will be your best line of defense.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.