News, Tips, Security Lab
Phobos Ransomware Mimics VX-Underground Researchers
A new version of Phobos ransomware claims to be developed by VX-Underground, a malware info sharing community. Hackers again disguise…
Welltok Data Breach Exposes More Than 8 million Patients
Welltok, a healthcare Software as a Service (SaaS) provider, has reported unauthorized access to its MOVEit Transfer server, impacting the…
LitterDrifter – Russia’s USB Worm Targeting Ukrainian Entities
LitterDrifter USB worm, intricately linked to the notorious Gamaredon group and originating from Russia. It has set its sights on…
Apache ActiveMQ Vulnerability Exploited In The Wild
Recent Apache ActiveMQ vulnerability, that allows for remote code execution, is reportedly exploited in real-world attacks. Analysts noticed several exploitation…
Zimbra Vulnerability Exploited in the Wild
Google TAG’s recent discovery reveals a 0-day exploit, CVE-2023-37580, targeting Zimbra Collaboration. This is a Cross-Site Scripting (XSS) vulnerability exploited…
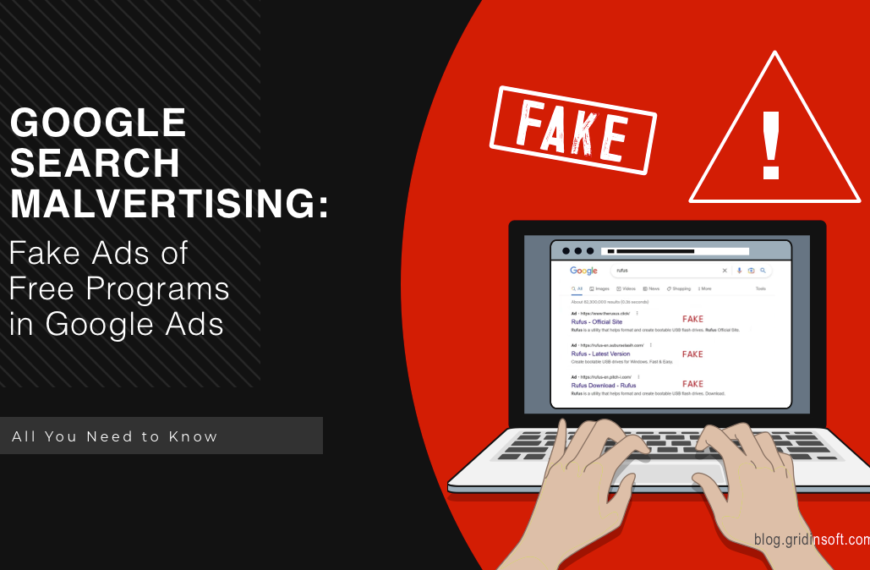
Google Search Malvertising: Fake Ads of Free Programs in Google Ads
Google Search malvertising is an unpleasant phenomenon of malicious advertisements in search engine results. Ads up there are called to make it easier to find users interested in specific queries,…
Russian Cybercriminals Seek Access to OpenAI ChatGPT
Check Point analysts have noticed that Russian-speaking hacker forums are actively discussing access to bypass geo-blocking, due to which the OpenAI ChatGPT language model is not available in Russia. We…
Goose Goose Duck Game Servers Are DDoS-Attacked Every Day
The free social detective Goose Goose Duck, which recently broke the Among Us record for the number of users simultaneously in the game, is constantly under DDoS attacks. The developers…
Exploits for Vulnerabilities in Three Popular WordPress Plugins Appeared on the Network
Three popular WordPress plugins, with tens of thousands of active installations, at once turned out to have critical SQL injection vulnerabilities. In addition, PoC exploits for these bugs are now…
Microsoft’s VALL-E AI Is Able to Imitate a Human Voice in a Three-Second Pattern
Microsoft engineers have introduced an AI (artificial intelligence) model for text-to-speech called VALL-E. It is able to imitate a human voice, relying only on a three-second sound sample. The developers…
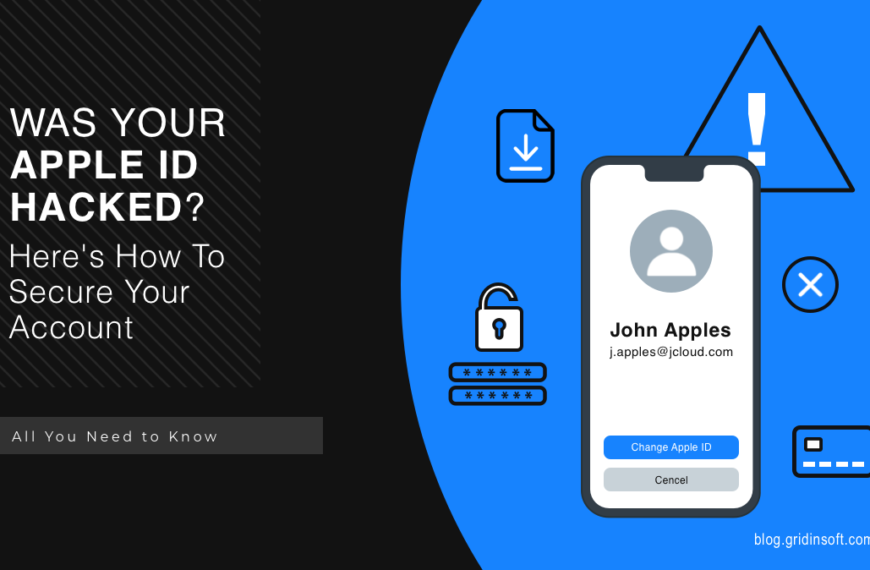
Was Your Apple ID Hacked? Here’s How To Secure Your Account
Apple’s services and products are only accessible through their walled garden. Users can only access the company’s products and services with an Apple ID. If someone figures out your Apple…
Hackers Bypass CAPTCHA on GitHub to Automate Account Creation
The South African hack group Automated Libra is looking for new approaches to use the resources of cloud platforms for cryptocurrency mining: hackers bypass CAPTCHA on GitHub. Let me remind…
Hackers compromised Slack private GitHub repositories
On December 31, while everyone was celebrating the New Year, Salesforce, the company behind the development of the corporate Slack messenger, published a message about the incident of compromising Slack…
Windows 7 Extended Security Update Program cancelled
On January 8, 2023, Microsoft announced the cancellation of the ESU program for Windows 7. The OS version released back in 2009 now lost all the support from its developer.…
Web Application Firewall: Difference Blocklist and Allowlist WAFs
You may have come across a Web Application Firewall (WAF) concept but have yet to give it much thought. However, it is essential to understand what a WAF is to…
Dangerous Virus & Malware Threats in 2023
Virus and malware threats are constantly evolving and become more sophisticated and more dangerous over time; this makes it extremely difficult to maintain your data’s security. Unless you’re adequately protected,…
Security Breach
A security breach is an unauthorized access to a device, network, program, or data. Security breaches result from the network or device security protocols being violated or circumvented. Let’s see…