A new version of Phobos ransomware claims to be developed by VX-Underground, a malware info sharing community. Hackers again disguise themselves as information security specialists, ruining their image. How funny or serious is this all?
What is Phobos ransomware?
Phobos ransomware emerged in 2018 as a ransomware-as-a-service (RaaS), an offshoot of the Crysis ransomware family. The RaaS model allows one group of hackers to develop ransomware. At the same time, other attackers act as affiliates, distributing the program and encrypting information on compromised devices. However, the group of virus developers owns the encryption key and is engaged in communications with victims.
Over the past 5 years, Phobos has not become a star in the world of cyber threats with a turnover of millions of dollars. Although it had its “15 minutes of fame”. It is a rare example of ransomware family that targets both users and companies, albeit preferring small ones. According to the ID Ransomware service, in 2023 it will account for 4% of all calls to the service.
Phobos Mocks Up VX-Underground
This week, ransomware hunters discovered a new version of Phobos, which claims to be developed by the VX-Underground community. When encrypting files, the malware adds the string .id[unique_id].[[email protected]].VXUG to the file name. The email is the real address of the community, and the extension “VXUG” is a commonly used abbreviation for VX-Underground.
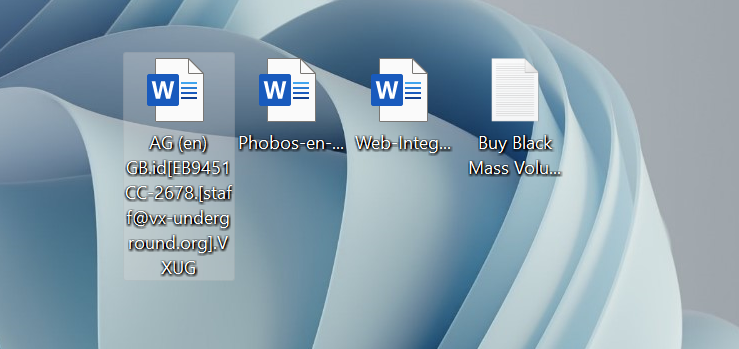
Once encryption is complete, Phobos creates ransom messages on the Windows desktop and other places. One of them is a ransom text message called “Buy Black Mass Volume II.txt“. The latter is the latest book released by the VXUG researchers.
To transcribe them, send an email to this address: [email protected]. If we don’t respond within 48 hours, please send a message to this twitter: @vxunderground and no, the decryption password is not “infected”
Another ransom note is a file named “Buy Black Mass Volume II.hta“, a standard ransom note from Phobos, designed using the VX-Underground logo, name and contact information.
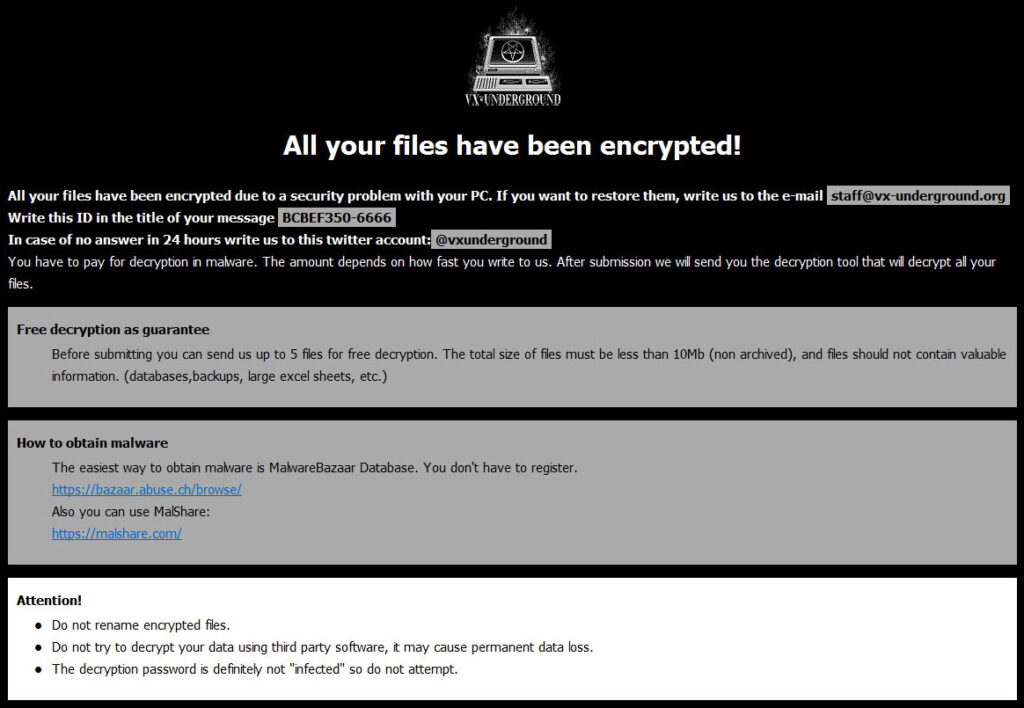
That is, victims are not provided with a real address where they can contact cybercriminals. This once again confirms the futility of any negotiations with hacker groups.
The reaction of VX-Underground, however, turned out to be consistent with the barbs of cybercriminals.
Cybersecurity Specialists Under Attack
While white and black hats practice their wits, let us remind you that threat actors participate in online communities dedicated to information security and even take part in discussions. For example, when REvil’s predecessor, the famous GandCrab malware, was released into the wild, the attackers named their servers after BleepingComputer, Emsisoft, ESET, and NoMoreRansom.
In 2016, the developer of the Apocalypse ransomware began inserting offensive comments about ransomware expert Fabian Vosar into Fabiansomware ransomware.
In 2021, Microsoft Exchange servers were attacked by the KrebsOnSecurity malware. Hackers exploited Proxylogon vulnerabilities on behalf of the famous information security expert Brian Krebs.
In summer 2022, the Azov Ransomware spread widely throughout the world through pirated software. The ransomware claimed to be created by BleepingComputer hacking and malware researchers Michael Gillespie and Vitaly Kremez, and asked victims to contact them to obtain a decryption key. The particular cynicism of cybercriminals was that just recently 36-year-old cybersecurity researcher and ethical hacker Vitaly Kremez died while scuba diving off the coast of Hollywood Beach in Florida. Cybersecurity experts have also warned that hackers sometimes impersonate well-known cybersecurity companies in phishing campaigns in an attempt to gain access to corporate networks.
Phishing emails from these attackers contained links to landing pages where victims’ credentials were stolen, or were “packed” with malicious attachments that were used to install malware if opened. If your goal is the security of information, then you are at risk and often a priority target for hackers. Appreciate information security specialists and their efforts – they are the “thin red line” that protects you from chaos and criminal lawlessness in cyberspace.