Azov ransomware, a newcomer to the encryption malware market, appears in view with a rather unusual strategy. This malware seems to be a simple vandal that shifts responsibility to honorable malware analysts. It gives users no chance to decrypt the files, as analysts can’t decrypt nor find the threat actor.
Azov ransomware asks for Ukraine support
This ransomware took the name of a famous Ukrainian battle squadron – Azov. They are known far away from battlefields of the Russo-Ukrainian war, but mostly in a positive case. Meanwhile, Azov ransomware ciphers users’ files, giving no workable instructions to go with. Ciphered files receive .azov extension and cannot be accessed in a traditional way. Moreover, there is no decryptor tool available at the moment.
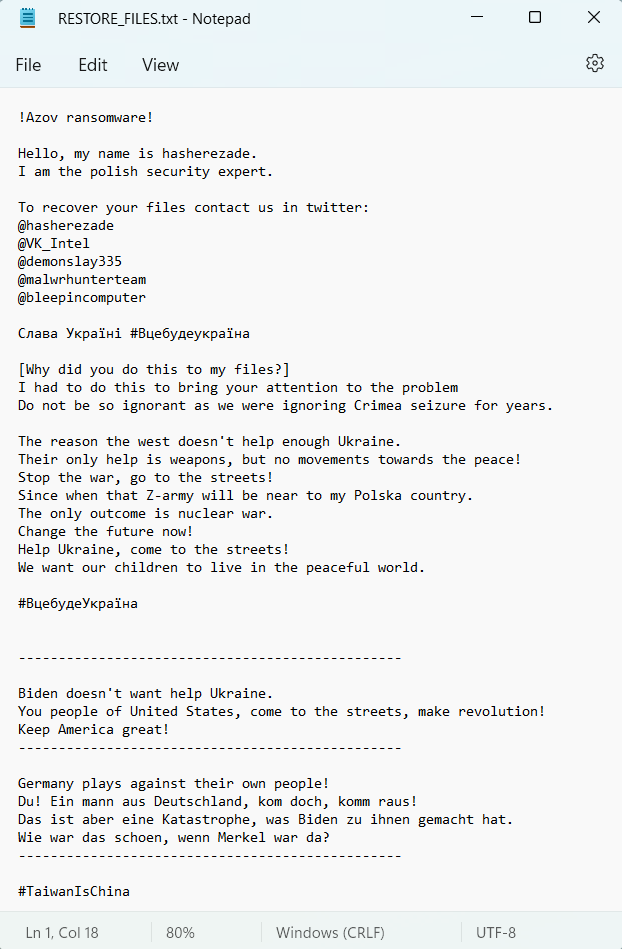
The claims like “contact ransomware analysts” look rather as an attempt to show their relation to this cybercrime. Crooks even signed the ransom note with the nickname of the one – Hasherezade. Others mentioned in the ransom note are Michael Gillespie, Vitaly Kremez, and Lawrence Abrams. However, they are not sorcerers and cannon decipher your files.
The exact malware is delivered through SmokeLoader – the backdoor that is also used to deliver STOP/Djvu ransomware and RedLine stealers. Overall, the distribution of this malware relies heavily on cracked software and keygen applications. Since there is no real way to reach Azov operators, this malware is a destructive wiper rather than ransomware. The attacked users have already begun complaining to different resources, including the analysts mentioned in the ransom note. However, the researchers do not yet know how to help the ransomware victims.
Ransomware gets politically preconceived
There’s nothing new in that some ransomware attacks have a political motivation. Russia-related group Conti was claiming responsibility for cyberattacks on governmental organizations of Western countries. Soon after the Russian war against Ukraine started, a certain number of Ukrainian hackers popped out, spreading ransomware to Russia and its allies. Still, Azov ransomware does not look like being politically biased against Russia. It is contrary to what you may think looking at its name.
Its ransom note gives several signs that its creator is Polish (or it is just an attempt to make us think so). It blames the German and US governments for giving no support to Ukraine in the current war – which is far from reality. Both countries are the biggest supplier of different goods and the biggest monetary donors. The calls to “make revolution” with a reminiscence to the “sweet times” of Merkel’s chancellorship and pre-Biden times (i.e., Trump’s presidency) draw up a clear picture. It is obvious who’s the main beneficiary of any drastic changes in the current governments of European countries and the USA. And that’s not a new trick for Russians to impersonate their rivals to spread turmoil.





