If you’re seeing Misleading:Win32/Lodi detected by your antivirus, don’t panic. Your computer is showing fake security alerts. Pop-ups are claiming hundreds of viruses. You might see demands for $29.95 to “fix” these fake problems.
This guide will help you remove this scareware completely. Follow these step-by-step instructions to eliminate the threat. We’ll start with manual methods you can try right now.
| Detection Name | Misleading:Win32/Lodi |
| Threat Type | Scareware / Potentially Unwanted Program (PUP) |
| Primary Function | Shows fake alerts to sell fraudulent security software |
| Common Sources | Software bundling, fake downloads, deceptive ads |
| Target Price | $29.95/year – Typical cost for fake “full version” |
| Risk Level | Medium – Financial scam with system performance impact |
What is Misleading:Win32/Lodi?
Misleading:Win32/Lodi is scareware. It tricks you into thinking your computer has serious problems. The program shows fake security alerts. It claims to find hundreds of viruses instantly.
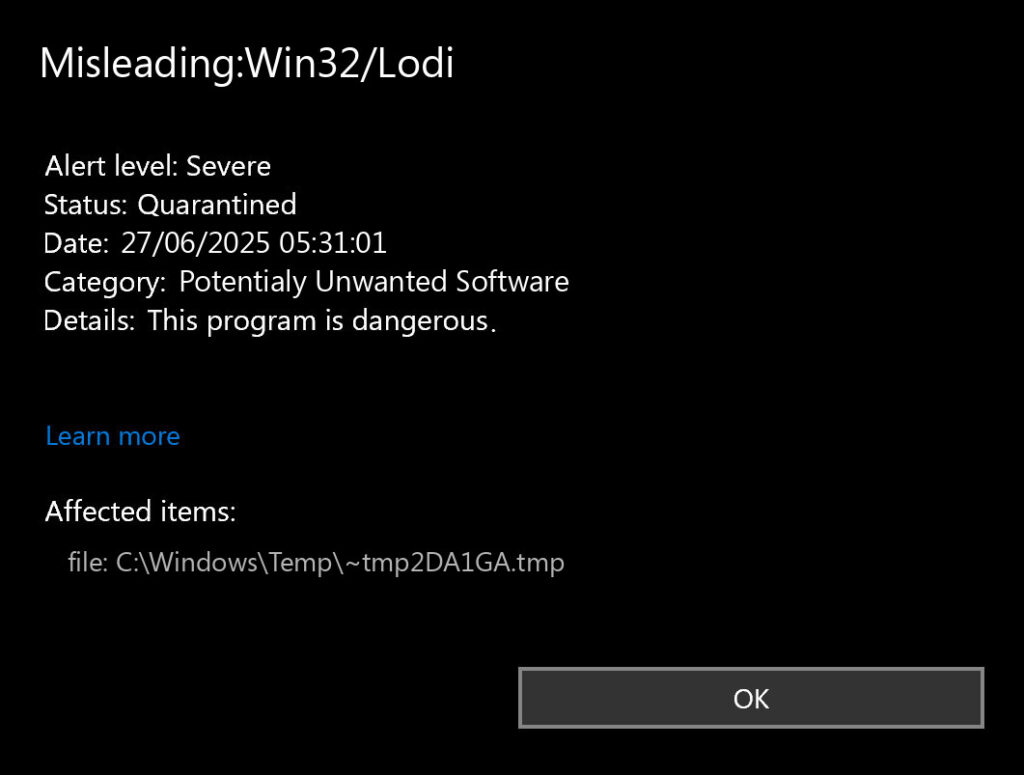
This is not real antivirus software. It’s designed to scare you. The goal is making you pay for fake fixes. The “problems” it finds don’t exist.
How You Know You’re Infected
- Constant fake security alerts popping up
- Claims of hundreds of viruses found immediately
- Demands for $29.95 or similar payment
- Computer running slower than normal
- Program won’t uninstall normally
- Browser settings changed without permission
Real antivirus software doesn’t work this way. Legitimate security programs don’t demand immediate payment. They don’t claim to find hundreds of problems instantly. This behavior is typical of fake virus alerts designed to scam users.
How Misleading:Win32/Lodi Spreads
This scareware reaches your computer through several methods:
- Software bundling – Hidden in free program installers
- Fake downloads – Disguised as system updates or drivers
- Malicious ads – Pop-ups claiming your computer needs scanning
- Email attachments – Pretending to be helpful utilities
- Infected websites – Automatic downloads from compromised sites
Similar to other bundled software threats, these programs exploit users who install software without reading carefully.
Manual Removal Steps
You can remove Misleading:Win32/Lodi manually. The process takes time and attention. Follow each step carefully. Skip steps and the program might return.
Step 1: Restart in Safe Mode
Safe Mode prevents the scareware from running. This makes removal easier.
- Press Windows key + I to open Settings
- Go to Update & Security → Recovery
- Under Advanced startup, click Restart now
- Choose Troubleshoot → Advanced options → Startup Settings
- Click Restart and press 4 for Safe Mode
Step 2: Stop Malicious Processes
End the scareware processes before removing files. This prevents the program from restarting itself.
- Press Ctrl + Shift + Esc to open Task Manager
- Click the Processes tab
- Look for suspicious processes:
- Programs using high CPU in temp folders
- Processes with random names like “svchost32.exe”
- Unknown programs running from AppData folders
- Right-click suspicious processes
- Select End task
- Note the file locations for later deletion
Step 3: Uninstall Through Control Panel
Try removing the program through Windows uninstaller first. This doesn’t always work with scareware. But it’s worth trying.
- Press Windows key + R
- Type appwiz.cpl and press Enter
- Look for recently installed suspicious programs:
- Fake antivirus with generic names
- Registry cleaners you didn’t install
- System optimizers with unknown publishers
- Select the suspicious program
- Click Uninstall
- Ignore any fake alerts during uninstallation
Step 4: Delete Malicious Files
Remove the program files manually. Scareware often hides files in multiple locations.
Check these common locations:
C:\Program Files\[Suspicious Program Name]C:\Program Files (x86)\[Suspicious Program Name]%AppData%\[Suspicious Program Name]%LocalAppData%\[Suspicious Program Name]%Temp%– Look for recent executable files
To access these folders:
- Press Windows key + R
- Type the path (like
%AppData%) - Press Enter
- Delete folders related to the scareware
- Empty the Recycle Bin when done
Step 5: Clean Startup Programs
Remove the scareware from Windows startup. This prevents it from running when you boot your computer.
- Press Ctrl + Shift + Esc to open Task Manager
- Click the Startup tab
- Look for suspicious programs:
- Unknown publishers
- Programs you didn’t install
- Generic names like “System Optimizer”
- Right-click suspicious entries
- Select Disable
Step 6: Clean Registry Entries
Remove registry entries created by the scareware. Be careful here. Wrong changes can damage Windows.
- Press Windows key + R
- Type regedit and press Enter
- Navigate to these locations:
Registry keys to check:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunHKEY_CURRENT_USER\Software\[Scareware Name]HKEY_LOCAL_MACHINE\SOFTWARE\[Scareware Name]
Delete entries that match the scareware program names. Don’t delete entries you don’t recognize.
Step 7: Check Scheduled Tasks
Scareware often creates scheduled tasks. These can restart the program automatically.
- Press Windows key + R
- Type taskschd.msc and press Enter
- Look in the Task Scheduler Library
- Check for suspicious tasks:
- Tasks with random names
- Tasks running from temp folders
- Unknown publishers
- Right-click suspicious tasks
- Select Delete
Browser Cleanup
Scareware often changes browser settings. It might install unwanted extensions. Let’s clean your browser completely.
Remove Malicious Browser Extensions
Google Chrome
- Launch the Chrome browser.
- Click on the icon "Configure and Manage Google Chrome" ⇢ Additional Tools ⇢ Extensions.
- Click "Remove" next to the extension.
If you have an extension button on the browser toolbar, right-click it and select Remove from Chrome.
Mozilla Firefox
- Click the menu button, select Add-ons and Themes, and then click Extensions.
- Scroll through the extensions.
- Click on the … (three dots) icon for the extension you want to delete and select Delete.
Microsoft Edge
- Launch the Microsoft Edge browser.
- Click the three dots (…) menu in the top right corner.
- Select Extensions.
- Find the extension you want to remove and click Remove.
- Click Remove again to confirm.
Alternatively, you can type edge://extensions/ in the address bar to access the extensions page directly.
Opera
- Launch the Opera browser.
- Click the Opera menu button in the top left corner.
- Select Extensions ⇢ Manage extensions.
- Find the extension you want to remove and click the X button next to it.
- Click Remove to confirm.
Alternatively, you can type opera://extensions/ in the address bar to access the extensions page directly.
Reset Your Browser
If you suspect the scareware modified your browser settings, reset it completely:
Google Chrome
- Tap on the three verticals … in the top right corner and Choose Settings.
- Choose Reset and Clean up and Restore settings to their original defaults.
- Tap Reset settings.
Mozilla Firefox
- In the upper right corner tap the three-line icon and Choose Help.
- Choose More Troubleshooting Information.
- Choose Refresh Firefox… then Refresh Firefox.
Microsoft Edge
- Tap the three verticals.
- Choose Settings.
- Tap Reset Settings, then Click Restore settings to their default values.
Opera
- Launch the Opera browser.
- Click the Opera menu button in the top left corner and select Settings.
- Scroll down to the Advanced section in the left sidebar and click Reset and clean up.
- Click Restore settings to their original defaults.
- Click Reset settings to confirm.
Alternatively, you can type opera://settings/reset in the address bar to access reset options directly.
Automatic Removal with GridinSoft Anti-Malware
Manual removal can be complex and time-consuming. For a faster, more reliable solution, GridinSoft Anti-Malware offers automatic detection and removal of scareware threats. Professional anti-malware software can find hidden components and registry changes that you might miss.
Scareware like Misleading:Win32/Lodi uses tricks to avoid removal. It hides files in multiple locations. It recreates itself if you miss any pieces. Automatic removal tools bypass these tricks.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

Why Choose Professional Removal
- Complete detection – Finds all scareware components
- Safe removal – Won’t damage important system files
- Anti-removal bypass – Overcomes scareware protection tricks
- Real-time protection – Prevents future infections
- Time saving – Removes threats in minutes, not hours
How to Prevent Future Scareware Infections
Prevention is easier than removal. Understanding how scareware spreads helps you avoid it. Follow these practices to stay safe.
Safe Software Downloading
- Use official sources – Download from developers’ websites only
- Avoid download sites – Third-party sites often bundle unwanted software
- Read installation screens – Uncheck boxes for additional software
- Choose custom installation – Never use “Express” or “Quick” install
- Research before downloading – Check reviews and reputation
Similar to how software bundling operations work, scareware often hides in legitimate-looking installers.
Browser Security
- Enable pop-up blocking – Stop fake security alerts
- Keep browsers updated – Install security patches quickly
- Use ad blockers – Block malicious advertisements
- Avoid suspicious sites – Don’t click unknown links
- Never download from pop-ups – Real software doesn’t advertise this way
Email Safety
- Be skeptical of software offers – Especially “system optimizers”
- Don’t click email links – Especially from unknown senders
- Verify sender identity – Real companies don’t send unsolicited software
- Question urgent claims – Real security issues don’t need immediate payment
Many scareware campaigns use tactics similar to professional hacker email scams to create false urgency.
System Maintenance
- Regular scans – Use Windows Defender weekly
- Monitor installed programs – Check for unknown software monthly
- Keep Windows updated – Install security patches
- Create restore points – Before installing new software
- Watch system performance – Sudden slowdowns may indicate problems
Understanding computer security habits helps you maintain a clean system long-term.
How to Recognize Scareware Tactics
Scareware uses psychological tricks. Learning these helps you spot fake programs immediately.
Common Scareware Signs
- Fake urgency – Claims your computer is “severely infected”
- Impossible numbers – Finding hundreds of problems instantly
- Payment demands – Requiring money to “fix” issues
- Professional appearance – Copying legitimate software designs
- Fear language – Using scary terms about data theft
Legitimate vs Fake Security Software
Real security software:
- Has known companies behind it
- Offers free trials without payment
- Provides detailed threat information
- Uninstalls easily through Windows
- Has positive reviews from trusted sources
Fake security software:
- Appears suddenly without installation
- Demands immediate payment
- Shows vague threat descriptions
- Resists removal attempts
- Has no verifiable company information
Similar patterns appear in fake BSOD scams and other deceptive programs.
Frequently Asked Questions
What is Misleading:Win32/Lodi and why is it dangerous?
Misleading:Win32/Lodi is scareware that shows fake security alerts. It’s dangerous because it tricks people into paying money for fake fixes. The program also slows down your computer and can steal personal information. It’s not a real security threat itself, but it opens the door to financial fraud.
How did this scareware get on my computer?
Most scareware arrives through software bundling. You download a free program. The installer includes hidden additional software. The scareware installs alongside the main program. It can also come from fake download sites, malicious ads, or email attachments disguised as helpful utilities.
Are the security problems it shows real?
No, the problems are completely fake. Scareware is programmed to always find hundreds of issues. It doesn’t matter if your computer is perfectly clean. The goal is creating panic so you’ll pay for the fake “full version.” Your computer probably has no real problems beyond the scareware itself.
I already paid for the program – what should I do?
Contact your bank immediately. Report the charge as fraudulent. Try to reverse the transaction. Change any passwords you entered, especially banking and email passwords. Remove the scareware completely. Monitor your accounts for unauthorized activity. Consider this a learning experience about online scams.
Can I just ignore the pop-ups instead of removing it?
Ignoring pop-ups isn’t safe long-term. The scareware consumes system resources. It slows down your computer. It might collect personal information. The constant alerts disrupt your work. Some variants download additional malware. Complete removal is the only safe solution.
Why won’t this program uninstall normally?
Scareware is designed to resist removal. It uses several tricks including disabling the Windows uninstaller, showing fake error messages during removal, hiding files in multiple locations, and creating registry entries that regenerate the program. This is why manual removal is complex and automatic tools are often necessary.
How can I tell if similar programs are legitimate?
Real security software has verifiable companies behind it. It offers free trials without requiring payment upfront. It provides detailed information about threats. It uninstalls easily through Windows settings. Fake programs appear without installation, demand immediate payment, show vague descriptions, and resist removal attempts.
Will removing this affect my computer’s real security?
Removing scareware improves your security. These programs provide no real protection. They often interfere with legitimate security software. After removal, make sure you have proper antivirus protection. Windows Defender is built into Windows 10/11 and provides good basic protection. Your computer will be safer without the scareware.
How can I prevent this from happening again?
Download software only from trusted sources. Read installation screens carefully. Uncheck boxes for additional software. Choose custom installation instead of express options. Keep your browser and operating system updated. Use ad blockers to prevent malicious advertisements. Be skeptical of urgent security claims that demand immediate payment.
Similar Threats to Watch For
Misleading:Win32/Lodi is part of a larger category of deceptive software. Understanding related threats helps you stay protected.
Other common scareware includes PUA:Win32/Vigua.A and PUA:Win32/Packunwan detections. These programs use similar tactics to trick users.
Beyond scareware, be aware of trojan malware that can cause real damage to your system. Information-stealing malware like modern infostealers poses serious privacy risks.
Email-based threats like fake hacker emails often work alongside scareware campaigns to create multiple pressure points for fraud.
Remove Misleading:Win32/Lodi Successfully
Misleading:Win32/Lodi is scareware designed to trick you into paying for fake security fixes. The threats it shows are completely fabricated. Don’t panic when you see these alerts. Don’t pay for any “full version” or “premium protection.”
- The security problems shown are fake – don’t panic
- Manual removal is possible but requires patience and care
- Professional removal tools are safer and more effective
- Prevention through safe downloading practices is best
- Real security software doesn’t use fear tactics or demand immediate payment
Manual removal works if you follow the steps carefully. Miss any components and the scareware returns. Automatic removal with professional tools is faster and more reliable.
Most importantly, learn from this experience. Understanding how scareware operates helps you avoid future infections. Download software only from trusted sources. Read installation screens carefully. Question urgent security claims that demand money.
Your computer’s security depends on using legitimate security software and following safe browsing practices. For users dealing with persistent infections or wanting comprehensive protection, professional anti-malware solutions provide the most reliable defense.





