Bitfiat is a malicious coin miner that exploits your computer’s hardware to mine cryptocurrencies. Such malware takes as much resources as it can, making the system impossible to use. Let’s see what this malware is, and how to remove it.
Bitfiat Overview
The Bitfiat process is related to the activity of a malicious coin miner. Such malware uses your computer’s resources to mine cryptocurrencies, mainly Monero or DarkCoin. An unusual part about Bitfiat is its origins: it is based on its own technology rather than using XMRig code. This, however, is the last part where it is different from other malware miners – its behavior is as unpleasant as in other cases.
As for the symptoms, they are typical: it causes the CPU to run at maximum capacity, often reaching 100%. You may also notice that your computer’s fan runs at full speed even when you are not using any programs. Moreover, this process usually appears in Task Manager and consumes the most resources. Although coin miners usually don’t harm your files, they make your system unusable due to an overloaded CPU.
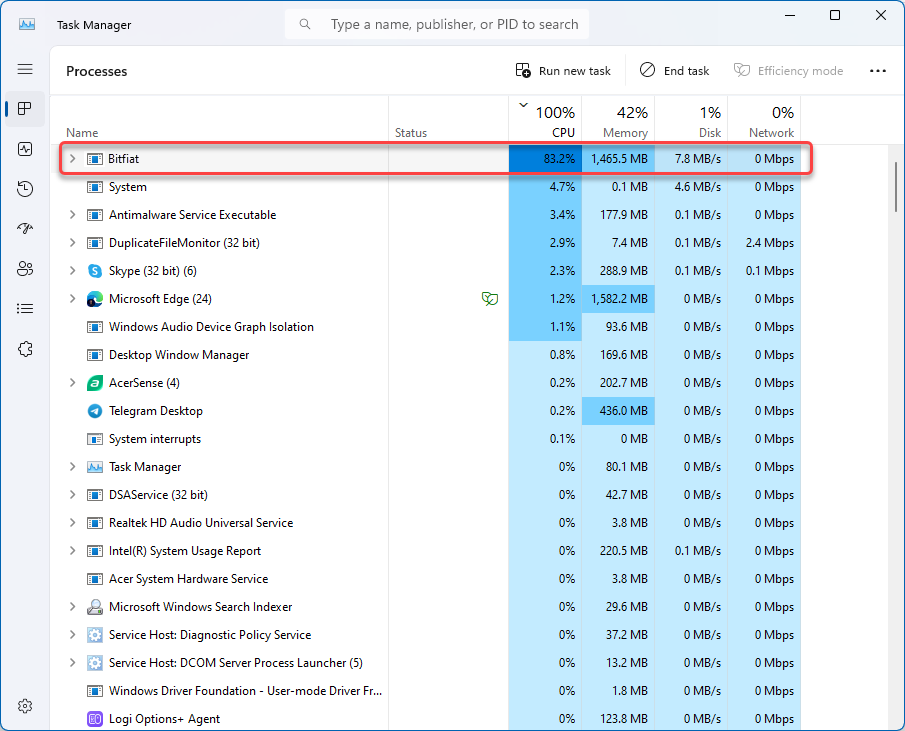
Bitfiat Virus Analysis
Despite having the origins different from the majority of malware miners, the infection chain of Bitfiat is pretty much the same. Let’s start from the very beginning and explore the operations of this malware. Fortunately, there are enough samples to analyze.
Spreading Methods
Bitfiat propagates through various channels, primarily leveraging cracked software and software activators “cracks”. These cracks are often distributed through illicit channels (like torrents) and online forums. It entices users with the promise of unlocking premium software features without needing to purchase. Even though it sounds like fairy tales, unwary users keep downloading such “free” premiums.
Another spreading way is botnets. By paying a coin to the masters of a botnet established with dropper malware, crooks can provide themselves with massive amounts of mining nodes. Thing is, after deploying the malware like a coin miner the entire malware spreading chain will be uncovered, and the dropper will be most likely removed from the machine. To maximize profits, miners are spread along with other “visible” malware, like ransomware or proxyware.
Launch, C2 Connection & Mining
The majority of Bitfiat samples do not have any detection evasion tricks. And, well, how can you evade the detection when your process takes up to 80% of the CPU? Right after launching, the malware performs an IP check, then collects some basic info about the system and connects to the command server.
Command servers used by Bifiat are rather unusual: there is no direct connection to the “main” C2. Instead, malware retrieves the needed instructions from the other infected machine, i.e. they operate like a p2p network. This provides much better stability, up to autonomous existence in the cases when the command server is unresponsive.
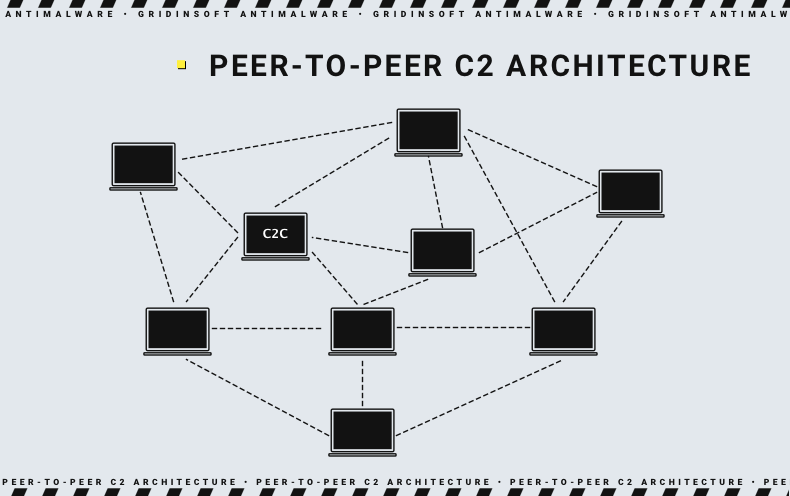
The said instructions in a form of config file contain the info about mining pool and crypto wallet address. After executing a few command prompt lines, it starts the mining process. And this is the point where the most noticeable sign of a malware miner activity appears – overloaded CPU and a strange process in the list of running programs.
How To Remove Bitfiat?
Effective removal of the crypto miner requires a complex approach to neutralize all malware actions. Unlike other types of malware, a miner can overload the system so that the removal tool has no resources left. To avoid these issues, the removal guide should have one more step.
- Download and install GridinSoft Anti-Malware. The first thing to do is to deploy the removal tool, even though it will be used later.
- Switch your Windows to Safe Mode with Networking. By booting into the Safe Mode with Networking, you prevent the Bitfiat process from exerting its influence on the CPU. This will facilitate uninterrupted removal by antivirus software.
- Start the Full Scan. By running a Full Scan, you make the program check every single element of the system. Such a thorough scan is essential to ensure that all the malware present in the system is removed. After the scan, click “Clean Now” to get rid of all the detected items.





