Microsoft has raised the alarm about a growing wave of ransomware attacks utilizing malvertising tactics to spread Cactus ransomware. The sophisticated malware campaign hinges on deploying DanaBot as an initial access vector, orchestrated by the ransomware operator Storm-0216, also known as Twisted Spider or UNC2198.
Cactus Ransomware Deployed by DanaBot
Microsoft’s Threat Intelligence team has disclosed an escalating wave of Cactus ransomware attacks. It is orchestrated by the notorious ransomware operator Storm-0216, a.k.a Twisted Spider/UNC2198. The malware campaign employs malvertising techniques, leveraging DanaBot as an entry point for the ransomware onslaught.
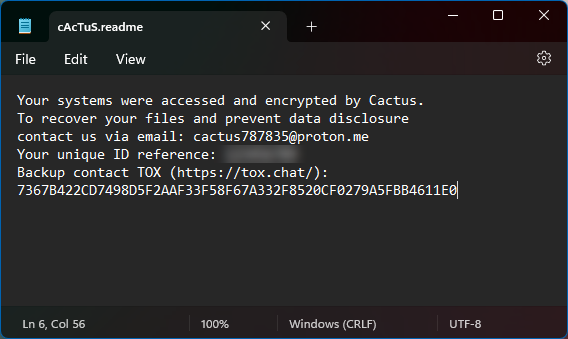
What makes Cactus particularly concerning is its ability to bypass antivirus software and exploit known vulnerabilities in VPN appliances to gain initial access to a network. Also, security experts have discovered that Cactus ransomware attacks exploit vulnerabilities in Qlik Sense, a data analytics platform. It is crucial to regularly update and patch software to protect against evolving ransomware threats.
What is DanaBot Malware?
DanaBot, identified by Microsoft as Storm-1044, stands as a multifaceted threat comparable to infamous counterparts like Emotet, TrickBot, QakBot, and IcedID. This malware operates as both a data stealer and a conduit for subsequent payloads. UNC2198, a threat group associated with DanaBot, has a track record of infecting endpoints with IcedID, a precursor to deploying ransomware families like Maze and Egregor, as previously outlined by Mandiant, a subsidiary of Google.
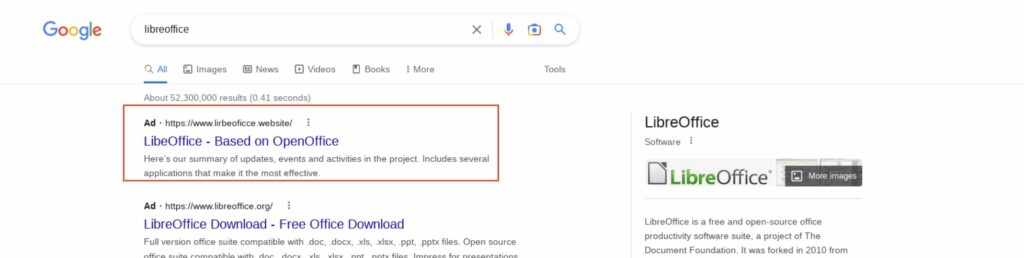
Microsoft’s intelligence suggests a transition from QakBot to DanaBot, likely triggered by a concerted law enforcement operation in August 2023 that dismantled QakBot’s infrastructure. The ongoing DanaBot campaign, observed since November, notably employs a private version of the info-stealing malware, diverging from the conventional malware-as-a-service approach.
Protective Measures
Microsoft’s recommendations include regular software updates and patches, robust security implementations, and comprehensive employee training to fortify defenses against phishing attempts.
- Regularly back up your data offline to protect it. If ransomware attacks your computer, the backup files will not be affected, and you can restore them without paying a ransom.
- It is important to conduct regular cybersecurity awareness training for employees to educate them about ransomware threats and safe online practices.
- Employ network monitoring tools to identify suspicious activities and potential indicators of compromise, allowing for proactive threat detection.





