LG reports fixing four critical vulnerabilities discovered in many of its TVs. These vulnerabilities were found back in 2023, and could allow malicious actors to gain control of affected LG TVs. Good news – the attacker should connect to the same network to exploit the flaw. Bad news – they can continue using the device afterwards from anywhere.
LG TV Critical Vulnerabilities Uncovered
LG reports addressing 4 critical vulnerabilities discovered in many of its TVs. The company released patches to different versions of their operating system to fix the issue in the way it interacts with LG ThinQ app. These vulnerabilities were uncovered late last year and could affect four specific LG TV models. Among them, CVE-2023-6317 is particularly emphasized on as it effectively opens the device to further exploitation.
The main tricky part about this vulnerability is that it requires being connected to the very same network as the TV does. This drastically complicates the exploitation, potentially making the flaw much less critical. However, a check through the Shodan search engine reveals that there are at least 91,000 devices exposed to the global network, i.e. they can be exploited remotely. Every single one of them is a perfect target for botnets like Mirai or InfectedSlurs.
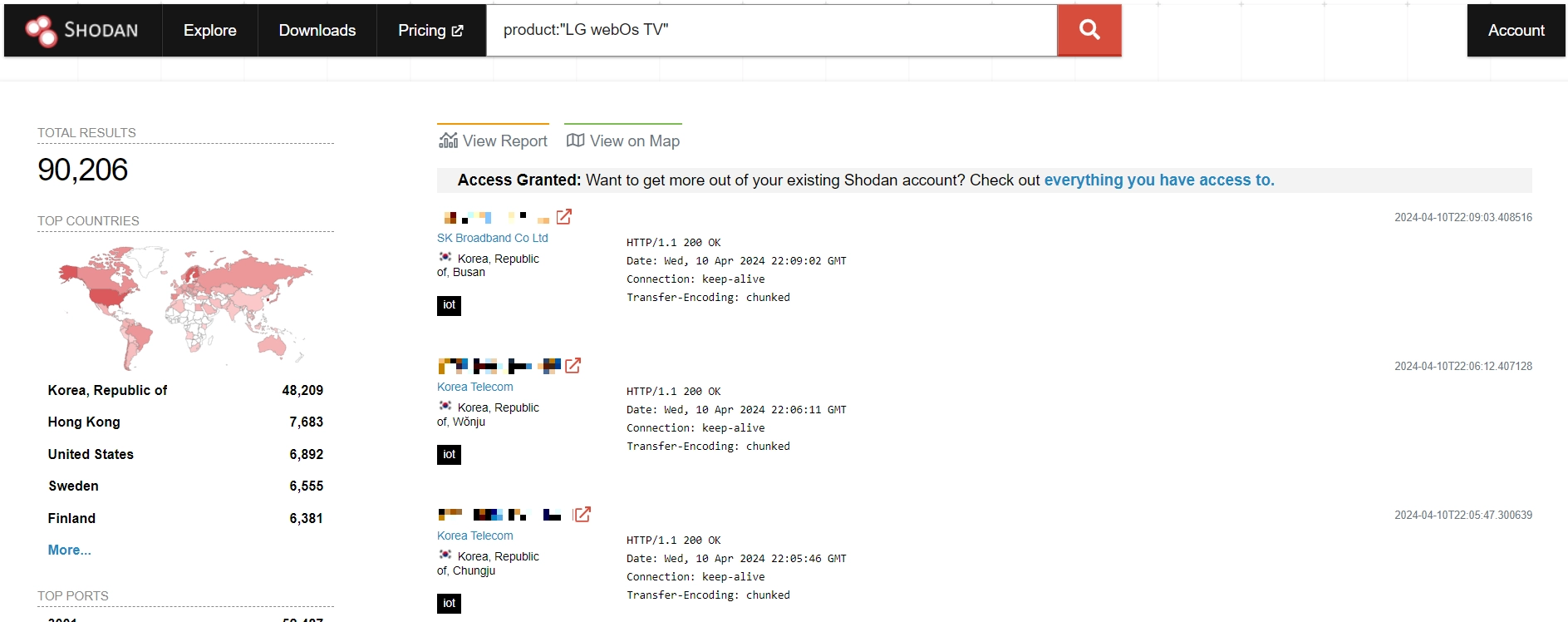
By exploiting these security flaws, malicious actors can attain root access to the devices, allowing them to execute commands at the operating system level. The vulnerabilities stem from internal services that control TVs using LG’s ThinkQ smartphone app within the same local network. Analysis done by BitDefender researchers describes all the flaws in details – here are some of the most interesting facts.
Technical Insights
Further analysis shows that these vulnerabilities have intricate workings. By exploiting errors in account handling mechanisms, attackers can circumvent PIN verification and create privileged user profiles. Subsequent attacks involve injecting OS commands and granting unauthorized access and control over the affected devices.
The procedure of CVE-2023-6317 exploitation is particularly simple, though involves some tinkering with the variables sent during the authentication process. First, the adversary should create an unprivileged account in the ThinQ app, which does not require entering a PIN on the TV. Second, they attempt creating the privileged account, while specifying the companion-client-key of the just created unprivileged account. Due to the lack of key source verification, creating a privileged account will be successful, opening gates for exploiting other 3 flaws.
Key Vulnerabilities
CVE-2023-6317 has CVSS 7.2 and allows the bypass of the second screen.gateway service running on webOS versions 4 through 7. An attacker can create a privileged account without asking the user for the security PIN. This vulnerability affects webOS 4.9.7, 5.5.0, 6.3.3-442, and 7.3.1-43.
CVE-2023-6318 (CVSS 9.1) is a command injection vulnerability in the processAnalyticsReport method from the com.webos.service.cloudupload service on webOS versions 5 through 7. Specially crafted requests can lead to command execution as the root user. An attacker can make authenticated requests to trigger this vulnerability in webOS 5.5.0, 6.3.3-442, and 7.3.1-43.
CVE-2023-6319 (CVSS 9.1) is the OS command injection vulnerability in the getAudioMetadata method from the com.webos.service.attachedstoragemanager service. The vulnerability affects webOS versions 4.9.7, 5.5.0, 6.3.3-442, and 7.3.1-43. It could allow authenticated command injection due to the lack of proper sanitization of the fullPath parameter.
CVE-2023-6320 (also CVSS 9.1) affects webOS 5.5.0 and 6.3.3-442. It allows authenticated command injection in the com.webos.service.connectionmanager/tv/setVlanStaticAddress endpoint can execute commands on the device as dbus, with permissions similar to those of the root user.
LG Releases Urgent TV OS Updates
As mentioned above, LG has released an update that fixes these vulnerabilities. The repercussions of these vulnerabilities are grave, as unauthorized access could lead to the exploitation of personal data, unauthorized app installations, or even the enlistment of devices into botnets. So, it’s imperative for LG TV owners to apply the available security updates as soon as possible.
While LG TVs are typically set to receive updates automatically, users are advised to verify that their devices are manually running the latest firmware version. By navigating through the settings menu, users can check for updates and ensure their TVs are fortified against potential threats. Also, for minimizing similar risks in future, users should close the access to the device from outside the network. The requirement to be in the same network diminishes any possibility for using the exploit in cyberattacks, making it just about mischieving someone.




