The “InfectedSlurs Botnet,” a sophisticated cyber threat, has been uncovered by the Akamai SIRT in a recent development. This malware campaign utilizes zero-day exploits to propagate the notorious Mirai malware, posing a significant risk to vulnerable devices worldwide.
InfectedSlurs Helps Mirai Botnet to Resurface
The InfectedSlurs Botnet has strong ties to the infamous Mirai malware, specifically the older JenX Mirai variant. Mirai gained notoriety for recruiting Internet of Things (IoT) devices through unconventional methods, including the use of games like Grand Theft Auto. The Mirai code’s unchanged nature, evident in a side-by-side comparison of the April 2023 variant and the October 2023 campaign, suggests a lack of significant modifications.
Why are InfectedSlurs Attacks Unique?
The Akamai SIRT, utilizing its global network of honeypots, detected a surge in activity. It was targeting a seldom-used TCP port in late October 2023. Intriguingly, the attack began with a low frequency, escalating to a peak of 20 attempts per day before tapering off to an average of two to three attempts. The initial targets remained unidentified until November 9, 2023.
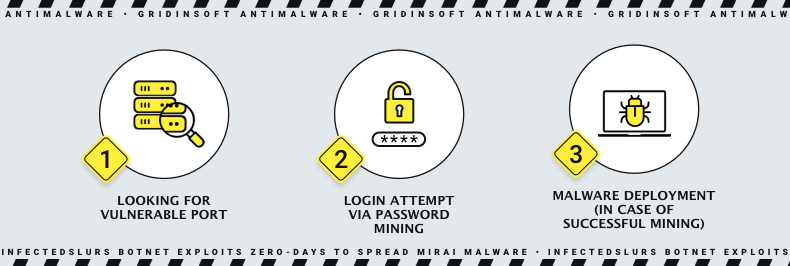
The attackers employed a unique approach, initiating an authentication attempt via a POST request. They followed by a command injection exploitation upon success. Through meticulous investigation, a specific HTTP exploit path and targeted port were identified. Initial confusion arose from an internet slang-rooted Server header in the HTTP response, initially leading to suspicions of a honeypot or prank.
Botnet Targets
Further analysis revealed that the exploited devices belonged to a specific niche: real-time streaming protocol (RTSP) enabled devices, particularly CCTV/NVR/DVR/security cameras. The attack exploited a zero-day vulnerability in NVR devices manufactured by a yet-unnamed company. Remarkably, default administrative credentials, commonly documented by the manufacturer, were utilized in the attack.
Simultaneously, a second zero-day exploit surfaced, affecting outlet-based wireless LAN routers designed for hotel and residential applications. The vendor, also unnamed, plans to release details in December 2023. With both vendors working on patches, the community is urged to remain vigilant.
Reacting to activity
The InfectedSlurs Botnet underscores the significance of proactive cybersecurity measures. The deployment of honeypots, as demonstrated by the Akamai SIRT, offers crucial insights into evolving threats.
- Organizations are reminded of the importance of changing default passwords and staying informed about emerging cyber threats to bolster their defenses against sophisticated attacks.
- We recommend that SOAR and SIEM systems be used to detect, stop, and block any further cyberattack attempts within the entire environment.
- Policies such as zero-trust can prevent exploitation by identifying and blocking attacks that use even well-known and trusted software.
- Installing patches regularly is crucial in ensuring your system’s security, as it contains fixes for known vulnerabilities. Neglecting this step renders any further advice ineffective.