Gridinsoft Security Lab
Spyware vs. Stalkerware: What’s the difference?
Fraudsters develop various methods to penetrate the property of others, so there are different types of attacks and threats. In this article, we will look at what spyware and stalkerware are, their differences, and how to avoid these programs penetrating your device. What is Spyware? Spyware is well known to the public, whereas stalkerware is […]
Why Phishing is Still the Most Common Cyber Attack?
Unfortunately, millions of users worldwide are at risk every single day. Statistics show that a successful phishing attack occurs every 30 seconds, suggesting cybercriminals don’t stand still and evolve as their methods do. However, not only traditional phishing scams can damage a business – targeted phishing and CEO scams are much more devastating. Undoubtedly, IT […]
Most Common Types of Social Engineering Attacks
Intruders are developing more and more methods to get what they want. Social engineering is one of the most common methods through which fraudsters manage to deceive the user, manipulate him, and instill his fear and urgency. Once the victim is emotional, the fraudsters begin to cloud her judgment. Any human error is a vulnerability […]
Fargo Ransomware aims at vulnerable Microsoft SQL servers
Ransomware rarely chooses the sole type of targets for their attacks. They roam from attacks on small coffee shops to strikes on governmental organisations, with the corresponding adaptations to their software. However, all classic handbooks about offensive operations state that it is important to find a vulnerability of a target and exploit it. Such a […]
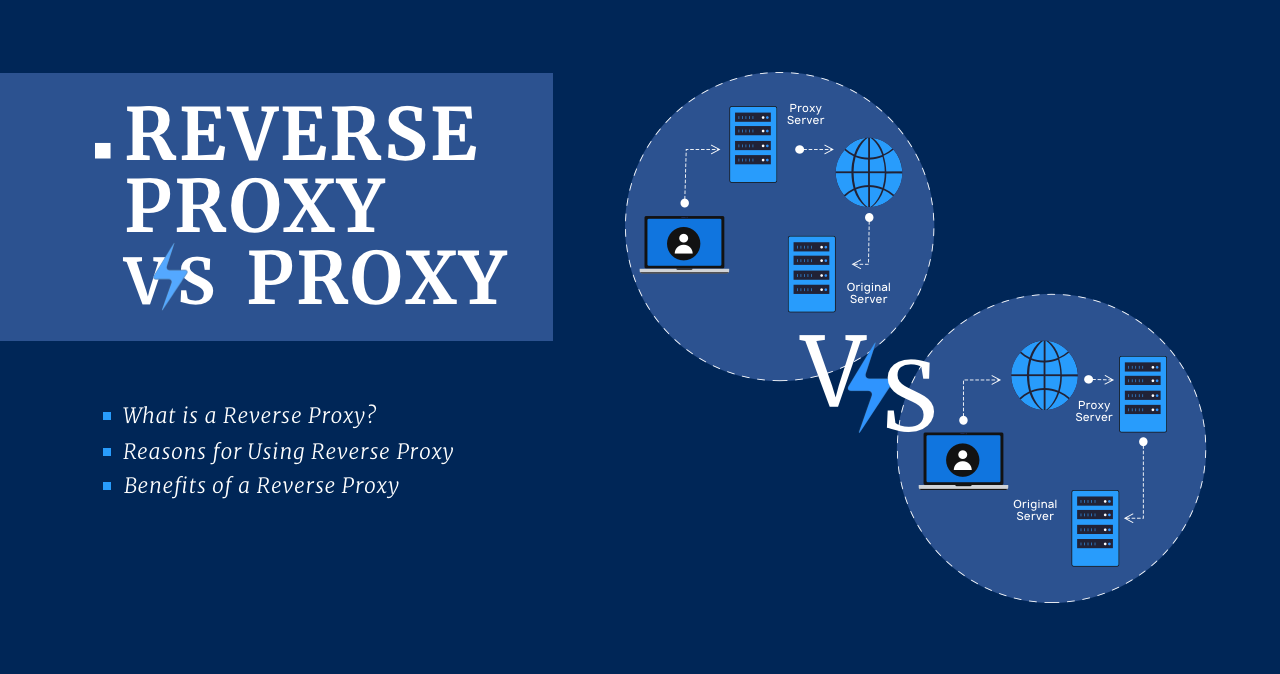
Reverse Proxy vs Proxy
What is a Reverse Proxy? A reverse proxy is the same server but is in front of a web server. Depending on its configuration, it allows or refuses the external connection to reach the endpoint. Reverse proxies are used to improve security, performance, and reliability. To understand how a reverse proxy works and what benefits […]
How to Report a False Positive Detection?
Gridinsoft is an antivirus software company that provides powerful solutions for detecting and removing malware from computers. However, sometimes our software may generate false positive detections, which can frustrate users. If you believe we have wrongly detected a legitimate file as malware, you can report the false positive detection to us. Here are the steps […]
Types of Computer Virus
Computer viruses can steal and facilitate the dissemination of your confidential information, and reduce your computer performance and any other threats. To understand what viruses are and how to get rid of them, we gave you a little insight into this topic. What is a computer virus? The computer virus is a piece of code […]
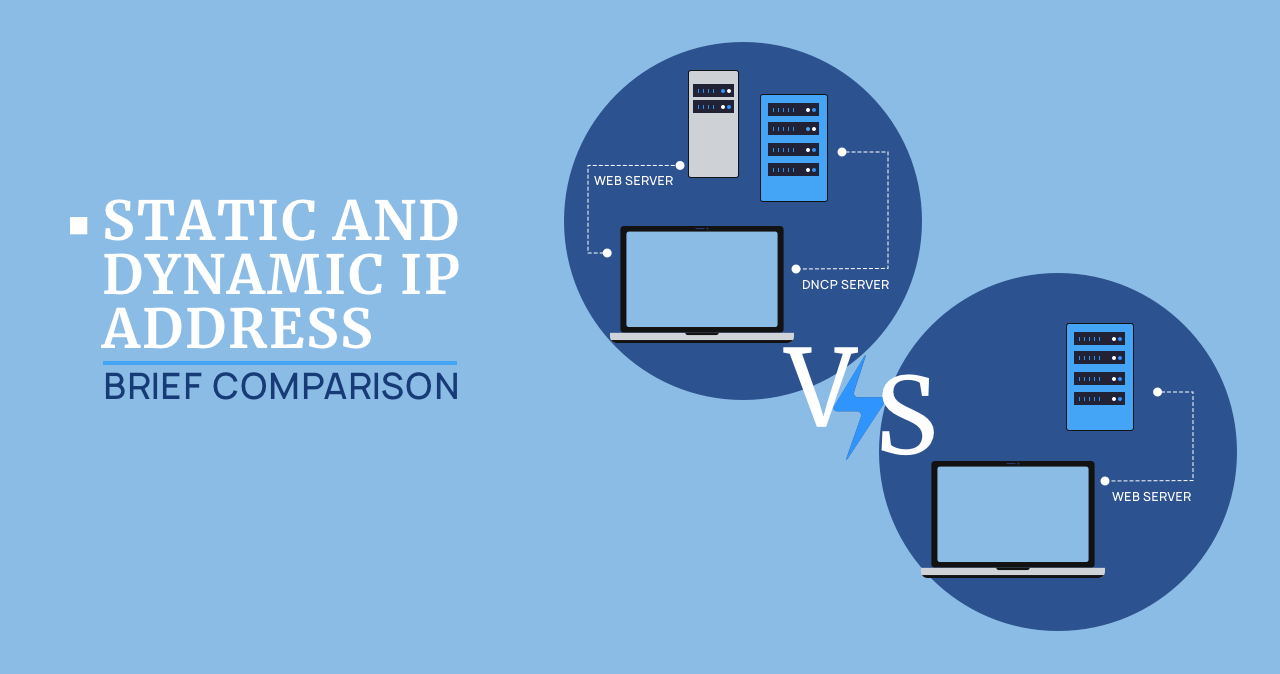
Static And Dynamic Ip Address: Brief Comparison
The Internet is built on IP addresses. They are divided into dynamic and static. Today we will look at the features of static and dynamic IP addresses and find out which type of IP address is more suitable for which tasks. What is an IP address? An IP address is a unique number that is […]
Penetration Testing: Stages and Methods
What is penetration testing? Penetration testing is a method by which the security of computer systems and networks can be assessed by simulating a hacker’s attack. It is possible to attempt cracking systems and applications via penetration testing. It allows identifying vulnerabilities in applications’ interfaces, application programming interfaces, or elsewhere in the system. If such […]
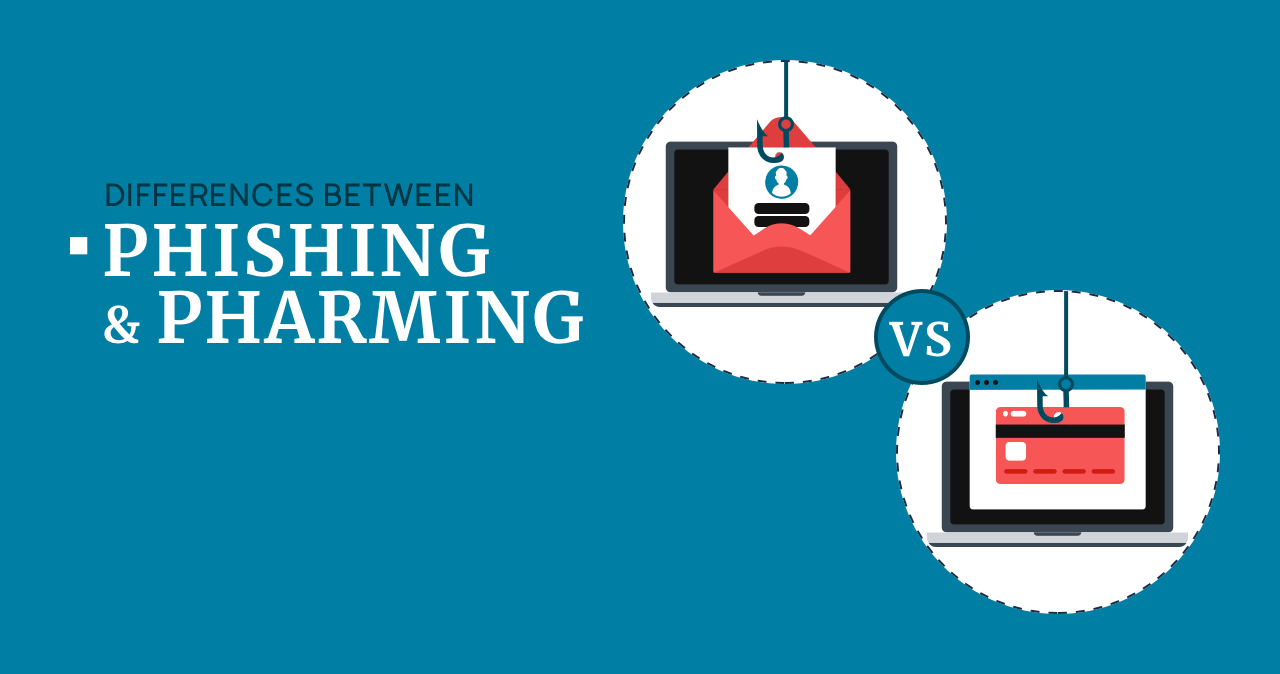
Difference Between Phishing and Pharming
Intruders try to keep up with the development in the digital world. The technology seeks to provide users with more effective resources, but the attackers in turn try to come up with even more sophisticated methods of cyberattacks. The two types of attack are Phishing and Pharming. Here we consider their characteristics and the difference […]
Smishing And Vishing: Differences To Know About Phishing Attacks
You can say it has become much easier for various criminals to get to their victims and target them with different schemes. And all because of the ubiquitous internet these days. You’ve probably heard the word ‘phishing‘. Today not only specialists from the cybersecurity field are actively talking about it but also ordinary users often […]
IPv4 vs IPv6: What’s the Difference?
What is IPv4 and IPv6? IP addresses allow computers and devices to communicate over the Internet. Without them, no one would know who is saying what and to whom. But there are two types of IP addresses, and the differences between IPv4 and IPv6 are significant. So keep reading to understand IPv4 and IPv6 and […]