Ransomware rarely chooses the sole type of targets for their attacks. They roam from attacks on small coffee shops to strikes on governmental organisations, with the corresponding adaptations to their software. However, all classic handbooks about offensive operations state that it is important to find a vulnerability of a target and exploit it. Such a tactic became an option for Fargo ransomware – or, as it was known earlier, Mallox or TargetCompany1. Crooks opted for Microsoft SQL as a basis for their attacks.
How do hackers use MS-SQL?
Microsoft SQL is a database management system, developed by a technological giant from Redmond. It has a decent market share, which creates a big pool of potential victims for crooks. But what is more important, MS-SQL has a lot of vulnerabilities that allow the crooks to use it as a gateway to the entire network. And as statistics show, they are pretty active with that approach – through the period of August 24 – September 23, there were over a hundred attack cases.
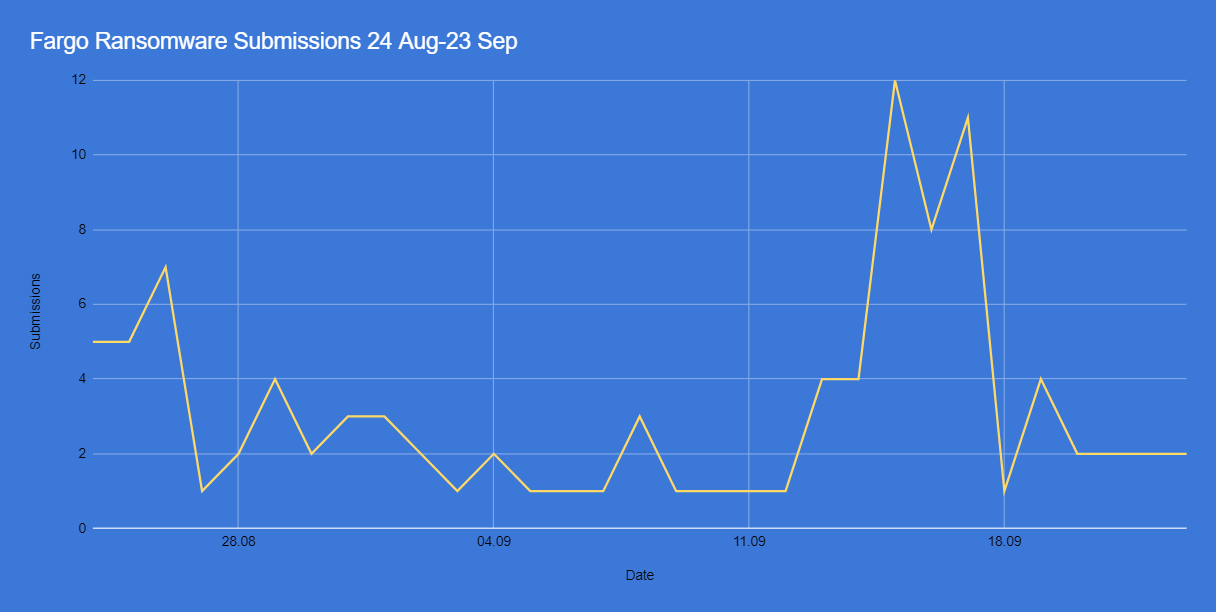
According to the researchers, the infection chain of Fargo ransomware begins with the download of the .NET file by the MS-SQL process using cmd.exe and powershell.exe. The downloaded file loads additional malware then generates and executes a BAT file that disables certain processes and services.
List of the processes disabled by Fargo ransomware:
fdhost.exe
fdlauncher.exe
MsDtsSrvr.exe
msmdsrv.exe
mysql.exentdbsmgr.exe
oracle.exe,
ReportingServecesService.exe,
sqlserv.exe,
sqlservr.exeAfter that, the malware injects itself into AppLaunch.exe and tries to delete the registry key of the Raccine utility, which is used to kill any processes that try to delete shadow copies in Windows using vssadmin.exe. In addition, the malware disables recovery and terminates all processes associated with databases to make their contents available for encryption. It also creates and modifies the following registry entries:
Key created \REGISTRY\USER\S-1-5-21-2513283230-931923277-594887482-1000_CLASSES\tohnichi_auto_file\shell\open\command rundll32.exe
Set value (str) \REGISTRY\USER\S-1-5-21-2513283230-931923277-594887482-1000_CLASSES\tohnichi_auto_file\shell\open\command\ = "%SystemRoot%\\system32\\NOTEPAD.EXE %1" rundll32.exe
Key created \REGISTRY\USER\S-1-5-21-2513283230-931923277-594887482-1000_Classes\Local Settings rundll32.exe
Key created \REGISTRY\USER\S-1-5-21-2513283230-931923277-594887482-1000_CLASSES\Local Settings\Software\Microsoft\Windows\Shell\MuiCache rundll32.exe
Key created \REGISTRY\USER\S-1-5-21-2513283230-931923277-594887482-1000_CLASSES\tohnichi_auto_file rundll32.exe
Key created \REGISTRY\USER\S-1-5-21-2513283230-931923277-594887482-1000_CLASSES\.tohnichi rundll32.exe
Key created \REGISTRY\USER\S-1-5-21-2513283230-931923277-594887482-1000_CLASSES\tohnichi_auto_file\shell rundll32.exe
Key created \REGISTRY\USER\S-1-5-21-2513283230-931923277-594887482-1000_CLASSES\tohnichi_auto_file\shell\edit\command rundll32.exe
Set value (str) \REGISTRY\USER\S-1-5-21-2513283230-931923277-594887482-1000_CLASSES\.tohnichi\ = "tohnichi_auto_file" rundll32.exe
Key created \REGISTRY\USER\S-1-5-21-2513283230-931923277-594887482-1000_CLASSES\tohnichi_auto_file\shell\edit rundll32.exe
Key created \REGISTRY\USER\S-1-5-21-2513283230-931923277-594887482-1000_Classes\Local Settings rundll32.exe
Set value (str) \REGISTRY\USER\S-1-5-21-2513283230-931923277-594887482-1000_CLASSES\tohnichi_auto_file\ rundll32.exe
Set value (str) \REGISTRY\USER\S-1-5-21-2513283230-931923277-594887482-1000_CLASSES\tohnichi_auto_file\shell\edit\command\ = "%SystemRoot%\\system32\\NOTEPAD.EXE %1" rundll32.exe
Key created \REGISTRY\USER\S-1-5-21-2513283230-931923277-594887482-1000_CLASSES\tohnichi_auto_file\shell\open rundll32.exe
Still, malware is designed to ignore certain parts of a system – in order to keep it usable and provide the victims access to the ransom note. They generally aim at ciphering databases, MS Office/OpenOffice documents, text files, pictures, videos and image files. After the successful encryption, files receive the .Fargo3 extension. Malware uses a mix of ChaCha20, Curve25519 and AES-128 encryption algorithms, which makes it impossible to decrypt with available decryption tools. The plain text file named RECOVERY FILES.txt shows up the following instructions:
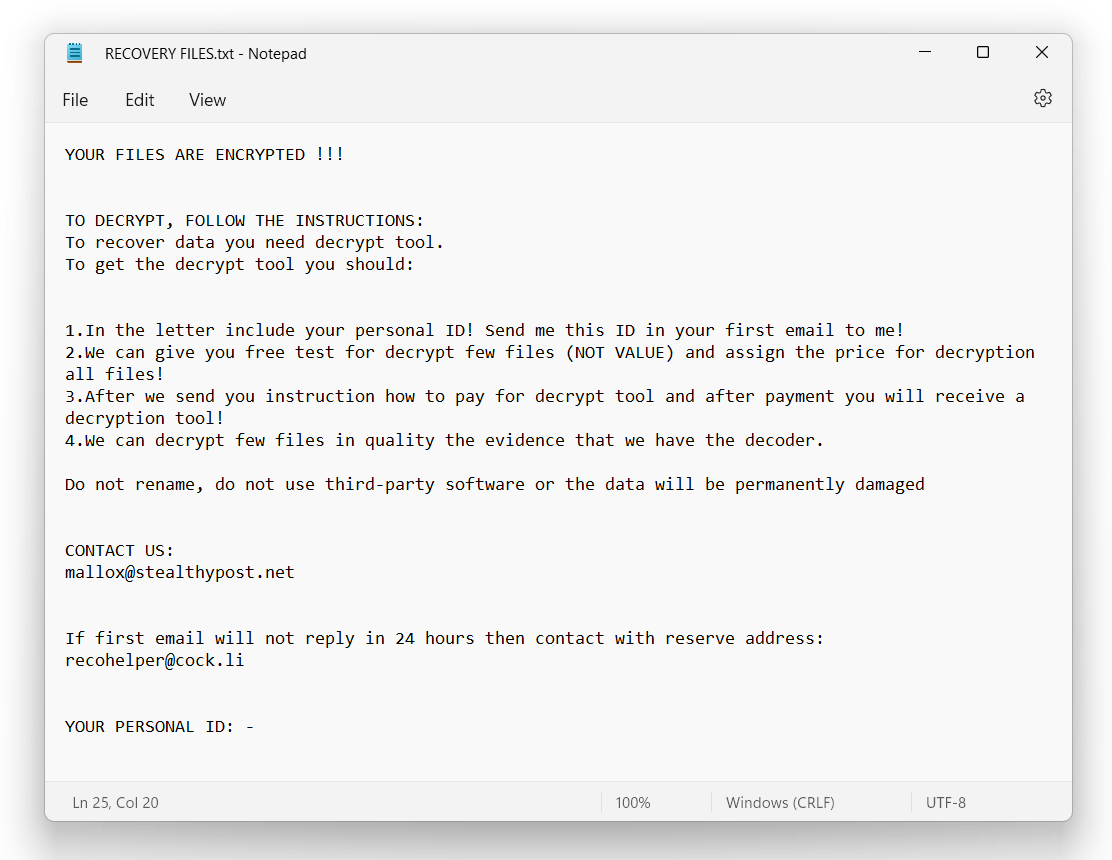
Ransom demands
Victims are threatened with the dumping of stolen files on the Telegram channel of ransomware operators if they do not pay a ransom. Experts warn that databases are most often compromised by dictionary and brute-force attacks, i.e. accounts with weak passwords are at risk. In addition, attackers exploit known vulnerabilities that may not be patched. Therefore, an obvious advice for MS-SQL server administrators is to install all the latest security updates for MS-SQL and change passwords to stronger ones. It is also recommended to keep all other software updated since protecting from these crooks does not guarantee protection from many others.
The ransom size may vary, depending on the amount of files ciphered and the time passed after the encryption. The often practise among different ransomware groups is rejecting any cooperation regarding decryption if the company was waiting too long. Moreover, some of them start publishing the leaked data in the Surface Web – even sensitive details may become available to everyone. Contacting the officials can also make crooks angry and lead to sly actions, for example – publishing the details of how they get into the network.
- Earlier notes about this group under a different name.




