What is penetration testing?
Penetration testing is a method by which the security of computer systems and networks can be assessed by simulating a hacker’s attack.
It is possible to attempt cracking systems and applications via penetration testing. It allows identifying vulnerabilities in applications’ interfaces, application programming interfaces, or elsewhere in the system. If such vulnerabilities are not fixed on time, they are most likely to be attacked later through code penetration. That justifies penetration testing, which is also called ethical hacking.
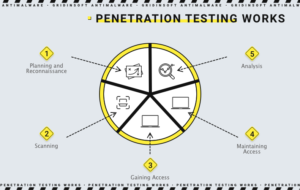
Penetration testing stages
- Planning and reconnaissance
this step includes the following items:- Defining the purpose and scope of testing. The same applies to systems that require solutions, and include testing methods in the process.
- In order to better understand how the target works and its possible vulnerabilities, it is necessary to collect information about the mail service, network domains and other related things.
- Scanning
Scanning will be the next step. This will help to understand how the targeted application reacts to intrusion attempts. It is important to do this by:- Static analysis – this code check helps to determine its behavior during operation. In one pass, these tools can scan the entire code.
- Dynamic analysis – this method is more practical, as it provides the application with real-time performance representation.
- Gaining Access
Intersite scripting, backdoors and SQL injections are used to identify vulnerabilities in this attack on websites. To understand what the underlying damage can be, you should use vulnerabilities, by stealing data, intercepting traffic, increasing privileges and more. - Maintaining access
This phase aims to determine whether vulnerabilities can be used to allow an intruder to be present in the exploited system and to gain full access to the device. The ultimate goal, of course, is to steal confidential data by imitating persistent threats. - Analysis
As a result of Penetration testing, it is possible to obtain:- Specific vulnerability
- Confidential data
- The time during which Penetration testing could go unnoticed.
The whole above described process is analyzed by the security system to decide how to fix the vulnerabilities in the system, configure the WAF (Web Application Firewall) parameters, and recognize similar attacks in the future.
Penetration testing methods
External testing
An act of ethical hacking as it is. Through this method, external tester can access domain names, email servers, company websites, web applications and eventually extract all relevant information from them.
Internal testing
This method is simulated. An hacker imitates an attack that seems to have access to an application behind a firewall. It starts with the fact that the attacker, thanks to a phishing attack, steals the employee’s credentials, and then, thanks to this data, imitates subsequent attacks.
Blind testing
In carrying out this attack, the tester knows only what will be his target company. But there’s an advantage for the security team: they are expecting some sort of attack, and they can watch it in real time.
Double-blind testing
In this case, the security service will not be able to construct a defense before the hack, as it will not have advanced information about the attack.
Targeted testing
This method involves the work of the tester and security personnel together. It is a kind of an exercise wherein the security team receives a feedback from a hacker’s point of view.
Penetration testing and Web Application Firewalls
Penetration testing and WAF can be considered some mutually beneficial security measures. The employer of many testing methods will use just WAF data (use and detection of weaknesses, logs..) But this data is also beneficial for WAF administrators too, considering the right feedback is established. They can update the WAF after completion of the test and thus protect against weaknesses that were detected during the test itself.
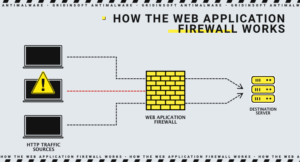
Penetration testing can also be useful for security audit procedures such as SOC 2 and PCI-DSS. In the case of PCI-DSS 6.6, this can only happen when using a certified WAF. But this characteristic does not make Penetration testing less useful and does not reduce all of its above-mentioned abilities and benefits.




