Software development company Ivanti (formerly MobileIron Core) has patched a zero-day vulnerability that allowed authentication bypass. This vulnerability had a maximum CVSS level and was actively exploited to gain unauthorized access.
What is Ivanti Company?
Ivanti is an IT software company headquartered in Utah, United States. It produces a variety of IT management and security solutions. Many organizations use the company’s products, including businesses, government agencies, and educational institutions. For example, almost all Norwegian ministries use Ivanti Endpoint Manager Mobile except a couple of ones. Having such important clients is always a huge responsibility, and unfortunately not everyone is capable of mitigating all the risks.
Ivanti EPMM 0-day Vulnerability
ACSC has received reports of a vulnerability in Ivanti EPMM (Endpoint manager mobile), also known as MobileIron Core, affecting all versions below 11.8.1.0. In brief, the vulnerability is CVE-2023-35078 and allows remote access to the API without authentication. It has the maximum severity rating of the CVSS scale and is a 10 out of 10 possible. While Ivanti said it received the information from a reliable source, the company did not disclose any further details about the nature of the attacks or the attacker’s identity behind them. Nevertheless, the Norwegian National Security Authority (NSM) confirmed that unknown attackers exploited the vulnerability to attack the State Organization for Security and Services (DSS). Thus, attackers could likely access and steal sensitive data from the compromised platform.
However, on Sunday, the company released a security patch that users can install by upgrading to EPMM 11.8.1.1, 11.9.1.1.1, and 11.10.0.2. However, versions below 11.8.1.0 that are outdated and unsupported have also received the update.
CVE-2023-35078 Details
CVE-2023-35078 is a zero-day authentication bypass vulnerability. It provides remote API access without authentication to specific paths. That is, an attacker can access personally identifiable information such as usernames, phone numbers, and other mobile device information on the vulnerable system. An attacker can also make configuration changes, including creating an EPMM administrator account for additional changes to the vulnerable system. The vulnerability affects all supported versions of EPMM (v11.10, 11.9, and 11.8) and earlier unsupported releases. However, the vulnerability is patched in versions 11.10.0.2, 11.9.1.1, and 11.8.1.1.1. Since CVE-2023-35078 has a maximum CVSS severity level of 10.0 and is easily exploitable, experts strongly recommend updating all devices, even EOL devices. Otherwise, if you cannot update the appliance, it is recommended to switch off.
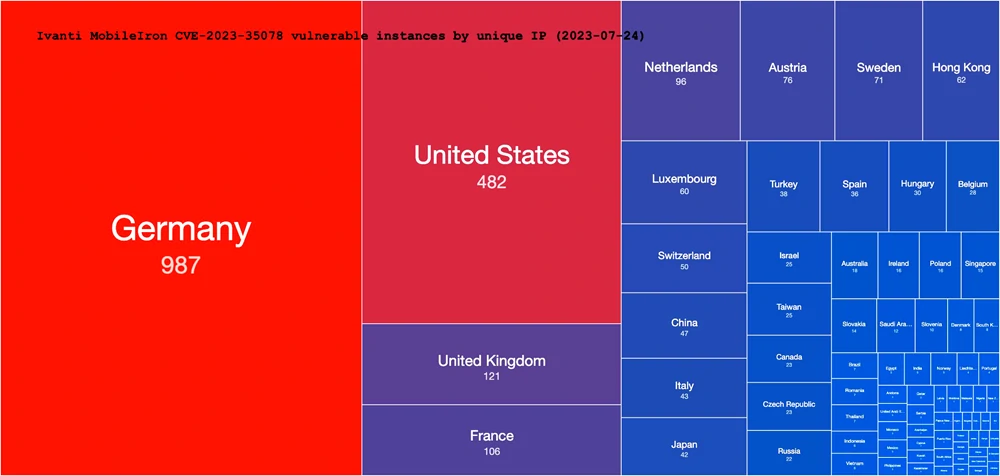
In addition, Ivanti has published a password-protected security advisory. However, only customers with login credentials can access it, which is perplexing. The company also clarified that the vulnerability is not used in a supply chain attack. IoT search engine Shodan found more than 2,900 MobileIron user portals are publicly available on the Internet, mainly in the US and Europe. About 30 of them are associated with local and state governments in the United States. The most vulnerable servers are in the US, Germany, the UK, and Hong Kong. The Norwegian National Cyber Security Center has notified all known system owners in the country that have MobileIron Core available on the Internet of a security update that has been issued.
How to secure against Ivanti 0-day vulnerability?
Well, the Norwegian government is not the only client of Ivanti. Companies from different corners of the world use their software, and appear to have a soft spot at the place no one expected. Here are some steps you can take to secure against the Ivanti 0-day vulnerability.
- Apply the latest security patches. It’s the first action you must take since Ivanti has released a patch to address the vulnerability. So, you should apply the patch as soon as possible to protect your organization.
- Use multi-factor authentication (MFA). It adds a layer of security to your organization’s IT systems. MFA requires users to use two or more pieces of identification to authenticate themselves. This way is making it more difficult for attackers to access your systems.
- Monitor your IT systems for suspicious activity. You should monitor them for suspicious activity, such as unauthorized access attempts or unusual traffic patterns. As we can see, it will help you to identify and respond to attacks.
- Educate your users about security best practices. Users are the first defense against cyberattacks. You should educate your users about safety best practices. For example, they must avoid clicking suspicious links or opening attachments from unknown senders.
By following these steps, you can help to protect your organization against the 0-day vulnerability and other cyberattacks.




