Email has been a staple in the internet world for over two decades, significantly enhancing communication. It has simplified the exchange of critical information for people within and beyond the business sector, allowing discussions from any global location. This tool has particularly revolutionized the business landscape. However, securing email communications has become crucial with the rise of cybercrime.
Emails are used daily by millions worldwide professionally. Over time, however, this beneficial tool has also become a potential threat. Like anything connected to the internet and technology, email is vulnerable, particularly email attachments seen in most messages. This susceptibility has heightened concerns about email security.
Common Threat Types for Email Security
Before exploring how to protect yourself from the dangers associated with email attachments, it is important to understand the basic types of malicious email threats to which we are all susceptible.
- Ransomware: Ransomware is a prevalent threat typically delivered through email. In such attacks, the perpetrator hacks the victim’s data and demands a ransom for its return.
- Phishing: Phishing involves criminals sending emails that appear trustworthy, containing links or attachments that prompt for login details. These credentials are then used for malicious purposes. Many people inadvertently trust and interact with these deceptive emails.
- Spam: Despite various methods developed to filter out unwanted spam, the issue persists. While some spam is merely bothersome, much of it can carry malware.

Email Safety Tips
The dangers associated with email attachments, as mentioned above, are common challenges faced routinely by users. However, there are numerous ways that your emails could be carrying malware and other threats like ransomware.
To help you stay safe and secure your email communications, we’ve compiled a list of effective email security tactics. These strategies will help you recognize potential dangers and avoid them before they escalate into serious issues. Let’s explore these tips!
1. Check the Sender
Business professionals often receive emails daily from various contacts, necessitating them to open and review each one. However, during a phishing scam, the sender’s name may appear familiar or even if not, the nature of business may compel you to open it regardless. Despite this, there is a precaution you can take: always verify the sender’s email address. Unusual email addresses are a common indicator of scams. Remember, it’s not necessary to open every email. If an email is critical, the sender will likely follow up with a phone call if they don’t receive a response. Trust your instincts; if an email feels suspicious, it’s safer to avoid engaging with it.
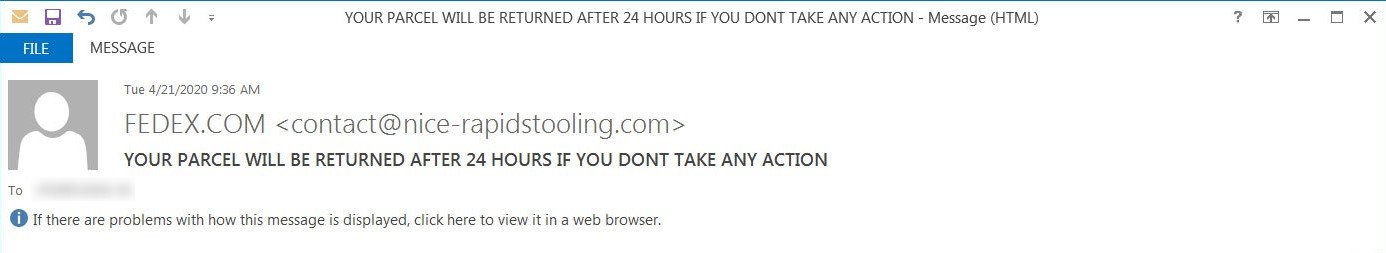
2. The Message Inside the Email
Even when you recognize the sender or are anticipating an email, exercise caution before opening it and engaging with its contents. Before clicking on any attachments, consider the following to ensure the email’s legitimacy:
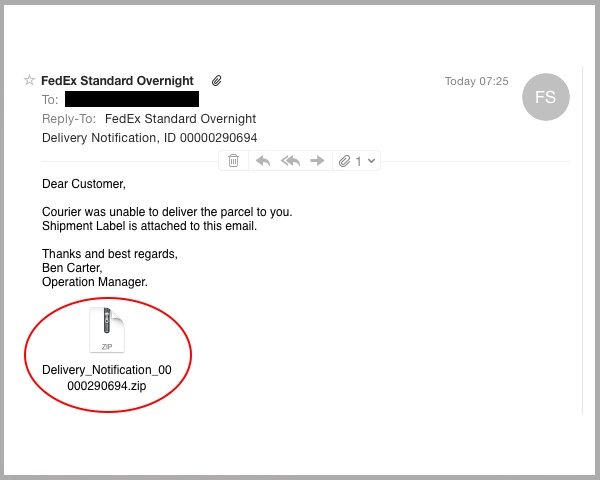
- The subject line of the email is critical. If it lacks a subject line or the subject line is vague, proceed with caution. For example, if the subject mentions an “invoice”, verify your recent purchases. If you haven’t ordered anything that matches the described item, do not open the email and consider marking it as spam.
- Emails that lack detail and use generic greetings like “Hi” are often indicative of phishing attempts. A legitimate email will include specific details about the company and a clear explanation of the email’s purpose. If these elements are missing, it’s best to disregard the email.
3. Digital Signature in Emails
For those engaged in corporate communications, verifying the presence of a digital signature is crucial. Before opening any attachments, check if the email purportedly from a company includes a digital signature at its end. For emails sent through Microsoft Outlook, a digital signature may be indicated by a red ribbon icon within the message, signaling corporate authenticity.
4. Check the Email Links
After confirming the internal contents of the email, including the presence of a digital signature, a relevant subject line, and the company’s logo, you might feel confident about the email’s legitimacy. However, it’s essential to remain vigilant by checking the links as well. Hover your mouse over any link or attachment to preview the destination address. If the address appears suspicious or unrelated to the expected content, it likely indicates a malicious intent such as ransomware or another type of scam. In such cases, it is advisable to delete the email immediately and avoid clicking on any links.
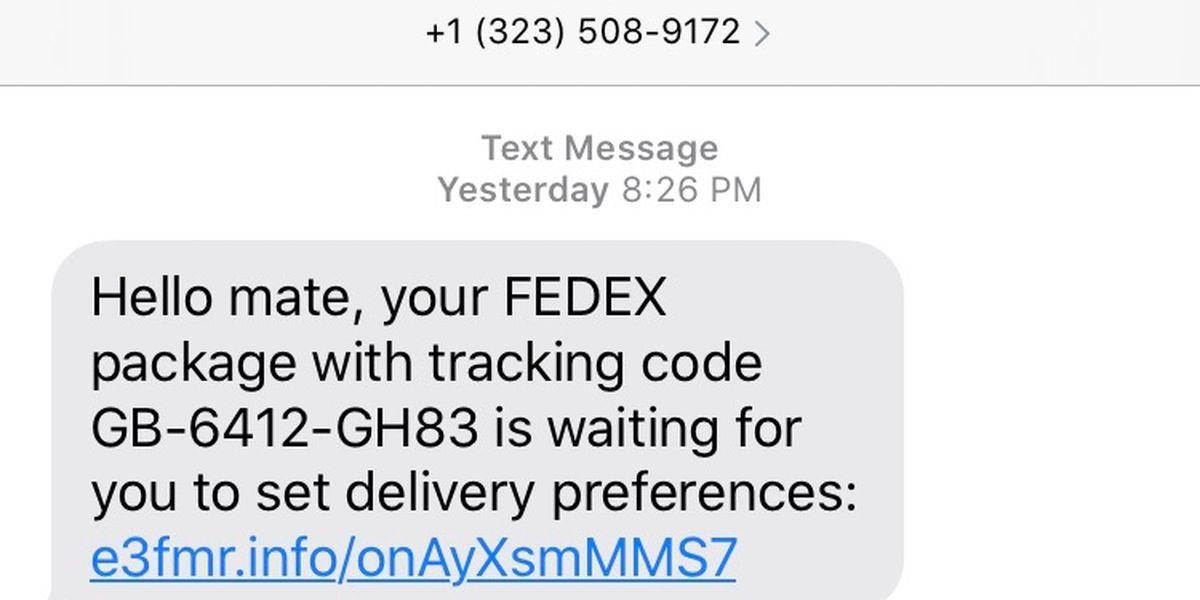
5. Use GridinSoft Anti-Malware for Enhanced Protection
To further secure your email communications from malware and other cyber threats, consider using GridinSoft Anti-Malware. This powerful tool offers robust protection against a wide array of threats, including those commonly disseminated through email, such as ransomware and phishing scams. GridinSoft Anti-Malware provides real-time protection by scanning incoming emails and their attachments for any malicious content before it can harm your system.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

Conclusion
Email has undoubtedly simplified and accelerated communication, revolutionizing business operations and opening countless opportunities. However, as technology has advanced, so too has the susceptibility of email to scams and other security threats. Prioritizing email security is essential for both individuals and businesses. By implementing the straightforward security measures discussed above, you can protect yourself and your business data effectively. Paying attention to the finer details and practicing vigilance can take just a minute or two, but these efforts are crucial in safeguarding against potential dangers.