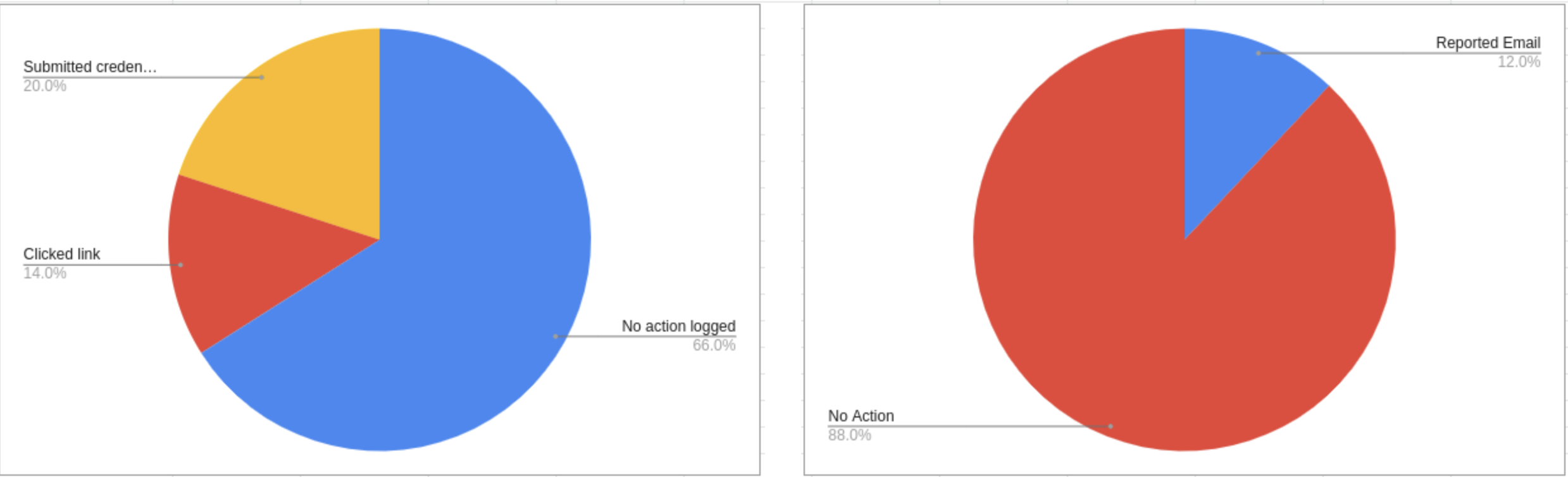
Recently, the GitLab platform conducted a security audit, analyzing if working from home employees are resistant to phishing attacks. As it turned out, every fifth got on phishing in GitLab: 20% of employees agreed to enter their credentials on a fake login page.
A training attack conducted by the GitLab Red Team simulated a real phishing campaign, the purpose of which was to find out the credentials of GitLab employees. For this purpose, information security specialists registered the gitlab.company domain name and configured it to send phishing emails using the open source GoPhish and GSuite from Google. Phishing emails were designed in order to simulate real notifications from the IT department, allegedly informing about the need to update the laptop.
“The target users were asked to click on the link, supposedly in order to agree to the update, but in fact this link led to a fake login page on GitLab.com located on the gitlab.company domain”, — say in GitLab.
During the audit were sent 50 such emails. As a result, 17 (34%) of recipients clicked on the link in the message, going to a special phishing site. Of these, another 10 people (59% of those who went to the site, and 20% of the total tested group) continued to work and entered their credentials on a fake page. However, only 6 out of 50 recipients of phishing messages (12%) reported a phishing attempt to GitLab security staff.
It is worth saying that, according to Verizon’s report, 22% of the total number of incidents related to data disclosure usually related to phishing, and about 90% of incidents are related to social interaction. The report also states that on average, the frequency of clicks on phishing links should be much lower – 3.4% against 20% shown by GitLab employees.
Another information security company, Rapid7, wrote that the frequency of clicks on links in phishing emails varies from 7 to 45%. Another 2018 report, compiled by KnowBe4, states that the average percentage of workers vulnerable to phishing attacks in various industries is 27%.
According to the Vade Secure report, during the pandemic, the number of phishing attacks using Facebook increased by 358.8%, and using Whatsapp messenger – by 13467%.
GitLab’s vice president of security, Jonathan Hunt, told The Register that he’s generally happy with the results of the audit and is pleased to see that GitLab’s results are better than average in the enterprise.
“Initially, the [Red Team] suggested that more people would fall for this phishing bait, but this assumption turned out to be wrong. Some vendors claim that the average success rate of phishing attacks is about 30-40%, so it’s nice to see that we are staying below this level”
Considering that popularity of phishing does not think to wane, Hunt emphasizes that companies are required to train their employees in information security, regardless of whether they work remotely or not:
“This means that companies, regardless of whether they work remotely or not, must train their employees so that they maintain the proper level of vigilance when dealing with e-mail. As organizations move more and more to remote work and, potentially, can more frequently use cloud services, user identity management and multi-factor authentication become critical factors. ”
Let me remind you that Github also recently warned employees and users about the increased danger of phishing attacks.




