The toolkit of cybersecurity specialists in companies does not consist only of security tools. To imitate the intruders, they apply using the tools like IP stressers. These tools create an environment and circumstances similar to the real attack. It is also an evil counterpart of IP stressers – DDoS-booters. But how do they work? Let’s figure that out.
What is an IP Stresser?
IP stresser is a special tool that tests a network or server for stress tolerance. The administrator can run the stress test to check whether the current resources (bandwidth, CPU power, or so) are sufficient to handle the additional load. Testing your network or server is a legitimate use of a stress test. However, running a stress test against someone else’s network or server, resulting in a denial of service to their legitimate users, is illegal in most countries.
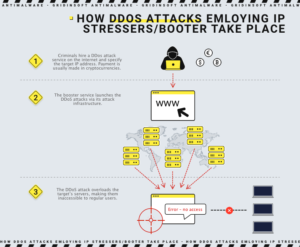
What are booter services?
Booters (also known as bootloaders) are on-demand DDoS (Distributed Denial of Service) attacks that cybercriminals offer to shut down networks and websites. Consequently, booters are illegal uses of IP stressers. Illegal IP stresses often conceal the identity of the attacker’s server by using proxy servers. The proxy redirects the attacker’s connection by masking the attacker’s IP address.
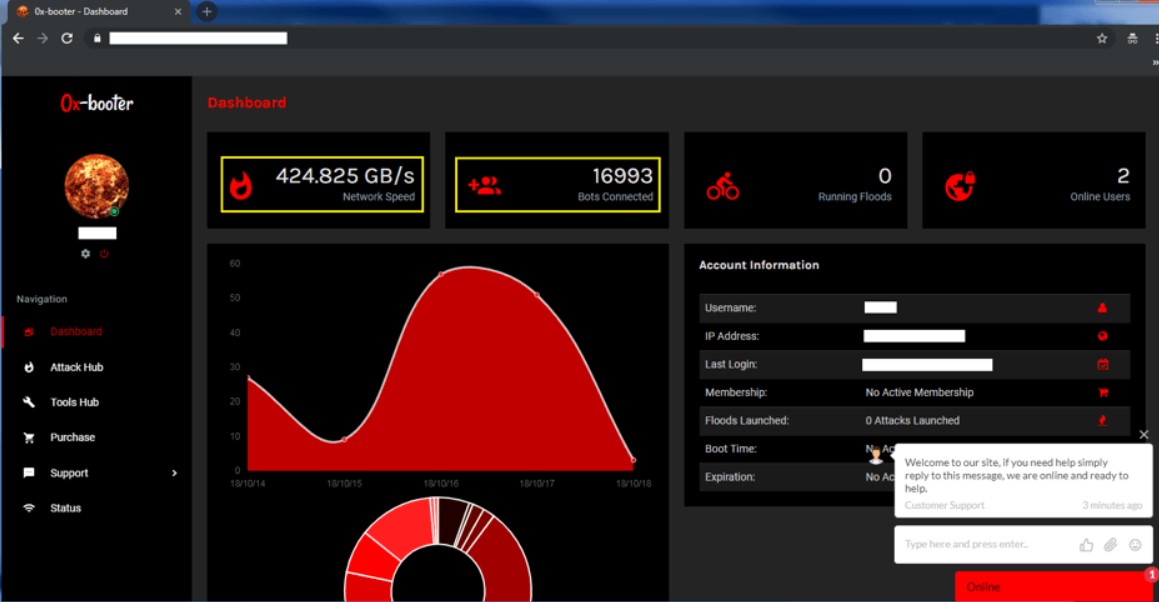
Booters are often available as SaaS (Software-as-a-Service) and are accompanied by email support and YouTube tutorials. Packages can offer one-time service, several attacks over some time, or even “lifetime” access. A basic one-month package costs a tiny sum. Payment methods can include credit cards, Skrill, PayPal, or bitcoins.
The difference between IP Stresser and botnets
In contrast to IP Stresser, the owners of computers that use botnets are unaware that their computers are infected with malware. Thus, they unwittingly become accomplices to Internet attacks. Booters are DDoS services for hire offered by enterprising hackers. Whereas in the past, you had to create your botnet to conduct a large-scale attack, now it is enough to pay a small amount of money.
Motivations DDoS attacks
The motives for such attacks can be varied: espionage1 to sharpen skills, business competition, ideological differences, government-sponsored terrorism, or extortion. The preferred payment method is bitcoins, as it is impossible to uncover the wallet owner. However, it is harder to go in cash when you have your savings in cryptocurrency.
Amplification and reflection attacks
Reflection and amplification attacks use legitimate traffic to overwhelm the targeted network or server. IP spoofing involves the attacker spoofing the victim’s IP address and sending a message to a third party on behalf of the victim. The third party, in turn, cannot distinguish the victim’s IP address from the attacker’s one and replies directly to the victim. The victim, as well as the third-party server, cannot see the real IP address of the attacker. This process is called reflection. For example, take a situation where the attacker orders a dozen pizzas to the victim’s home on behalf of the victim. Now the victim has to pay the pizzeria money for the pizzas, which she didn’t even order.
Traffic amplification occurs when a hacker forces a third-party server to send responses to the victim with as much data as possible. The ratio between the size of the response and the request is the amplification factor. The greater this amplification, the more potential damage is done to the victim. In addition, because of the volume of spoofed requests that the third-party server has to handle, it is also disruptive for it. NTP Amplification is one example of such an attack.
Amplification and reflection IP Stresser explained
The most effective types of bootstrap attacks use both amplification and reflection. First, the attacker spoofs the target address, then sends a message to a third party. The receiver sends the response to the target’s address, which appears in a packet as the sender’s address. The response is much larger than the original message, which amplifies the attack’s size. The role of a single bot in such an attack is about the same as if a teenage attacker called a restaurant, ordered the entire menu, and asked for a callback to confirm each dish. But the number for the callback belongs to the victim. As a result, the victim gets a call from the restaurant about orders it didn’t make and has to hold a line for a long time.
The categories of denial-of-service attacks
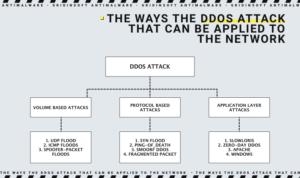
There are dozens of possible variations of DDoS attacks, and some of them have multiple subspecies. Depending on the hackers’ targets and skills, the attack may simultaneously belong to several types. Let’s review each of them one by one.
Application-layer attacks target web applications and often use the most sophisticated techniques. These attacks exploit a vulnerability in the Layer 7 protocol stack. They connect to a target and drain server resources by monopolizing processes and transactions. Because of this, they are challenging to detect and mitigate. A typical example is the HTTP Flood attack.
Protocol-based attacks exploit weaknesses at layers 3 or 4 of the protocol stack. Such attacks consume the victim’s processing power or other essential resources (such as the firewall). This results in a service disruption. Examples of such attacks are Syn Flood and Ping of Death.
Volumetric Attacks send large volumes of traffic to fill the entire bandwidth of the victim. Attackers generate bulk attacks using simple amplification methods. This attack is the most common — for example, UDP Flood, TCP Flood, NTP Amplification, and DNS Amplification.
Common denial-of-service attacks
The goal of DoS or DDoS attacks is to consume as many server or network resources as possible so that the system stops responding to legitimate requests:
- SYN Flood: A sequence of SYN requests is sent to the target system in an attempt to overload it. This attack exploits vulnerabilities in TCP connection sequences, also known as three-way handshakes.
- HTTP Flood: an attack in which HTTP GET or POST requests are used to attack a web server.
- UDP Flood: A kind of attack in which random target ports are flooded with IP packets containing UDP datagrams.
- Ping of Death: Attacks involve sending IP packets more significantly than the IP protocol allows. TCP/IP fragmentation works with large packets by breaking them into smaller ones. Legacy servers often fail if the full packets exceed the 65,536 bytes allowed. This has been fixed mainly in newer systems. However, Ping flooding is the modern incarnation of this attack.
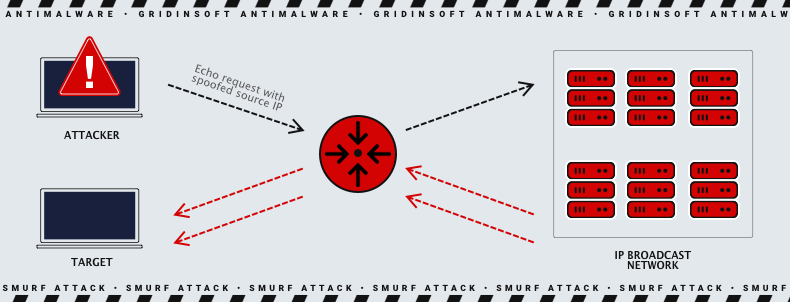
- ICMP Protocol Attacks: Attacks on the ICMP protocol are based on the fact that the server must process each request before a response is sent back. The Smurf attack, ICMP flooding, and ping flooding exploit this by flooding the server with ICMP requests without waiting for a response.
- Slowloris: this is an attack invented by Robert “RSnake” Hansen. It tries to keep multiple connections to the target web server open as long as possible. Thus, additional connection attempts from clients will be rejected.
- DNS Flood: An intruder fills the DNS servers of a certain domain to disrupt DNS resolution for that domain.
- Smurf Attack: This attack uses malware called smurf. Using a broadcast IP address, large numbers of Internet Control Message Protocol (ICMP) packets are sent to the computer network with a fake IP address of the victim.
- SNMP reflection: An attacker spoofs the victim’s IP address and sends multiple SNMP requests to the devices. The volume of responses can overwhelm the victim.
- DNS amplification: this reflection-based attack turns legitimate requests to DNS (domain name system) servers into much larger ones, thus consuming server resources.
Less popular DDOS methods
- NTP Reinforcement: A high volume reflection-based DDoS attack in which the attacker exploits the Network Time Protocol (NTP) server functionality to overload the target network or server with increased UDP traffic.
- SSDP: SSDP (Simple Service Discovery Protocol) attack is a reflection-based DDoS attack. It uses Universal Plug and Play (UPnP) network protocols to send an amplified traffic volume to the target victim.
- Teardrop Attack: An attack consists of sending fragmented packets to the target device. An error in TCP/IP prevents the server from reassembling such packets, resulting from which the packets overlapping each other, thus incapacitating the target device.
- Fraggle attack: the attack is similar to smurf, except that it uses UDP rather than ICMP.
What to do in case of a DDoS attack?
- Inform your data center and ISP immediately;
- Do not consider ransom – payment often results in escalating ransom demands;
- Notify law enforcement authorities;
- Monitor network traffic.
How to mitigate attacks?
- Install firewalls on the servers;
- Keep security patches up to date;
- Run antivirus software on a schedule;
- Monitor system logs regularly;
- Prevent SMTP traffic from being distributed by unknown mail servers;
- Causes of difficulty tracking the booter service.
Since the person buying these criminal services uses an external site to pay and receive instructions, the connection to the backend initiating the attack cannot be identified. Therefore, criminal intent can be challenging to prove. However, one way to identify criminal organizations is to track payment traces.





