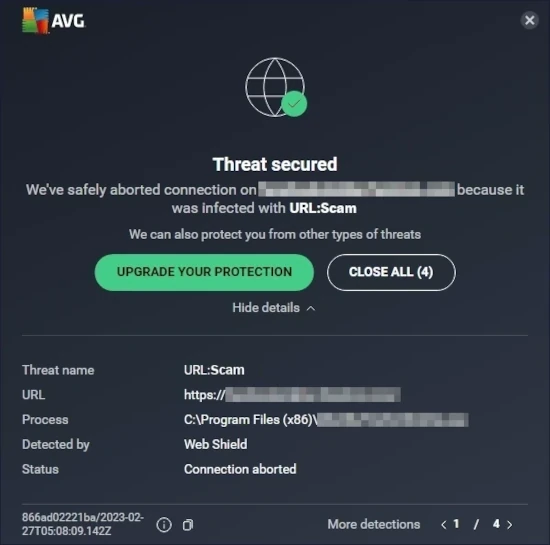
The URL:Scam detection by Avast and AVG is a protective warning that triggers when these security solutions identify a website as potentially fraudulent or malicious. When this alert appears during browsing, it means the antivirus has flagged a web address as a probable scam operation. This protection mechanism helps safeguard users, but understanding when and why it appears is essential for maintaining both security and a smooth browsing experience.
What is URL:Scam Detection? Technical Explanation
URL:Scam is a generic detection identifier used by Avast and AVG security products to flag websites showing signs of fraudulent activities. Unlike specific malware detections, this broader classification helps protect users from various deceptive websites but occasionally flags legitimate sites incorrectly (false positives).
The detection system evaluates multiple factors: domain reputation scoring based on historical behavior, content analysis of page elements and scripts, behavioral heuristics monitoring suspicious activities, machine learning classification comparing against known scams, and community feedback from user reports.
Five Common Types of Websites Flagged with URL:Scam
Based on our research of thousands of sites flagged with URL:Scam detection, here are the most common fraudulent website categories you might encounter:
| Scam Category | How to Identify | Real-World Example |
|---|---|---|
| Credential Phishing | Login pages with subtle URL differences, requesting passwords without proper security indicators | “m1crosoft-secure.com” – A site we analyzed that perfectly mimicked Microsoft’s login page but sent credentials to attackers in Belarus |
| Fake Shopping Sites | New domains offering extreme discounts (70%+) on popular brands with limited payment options | “brandsuperdiscount.store” – Offered $1,200 smartphones for $199, collected payment information, but never shipped products |
| Cryptocurrency Scams | Investment platforms promising guaranteed returns, celebrity endorsements, or requiring wallet connection | “crypto-multiplier.net” – Claimed to double Bitcoin investments in 24 hours, complete with fake testimonials and transaction history |
| Prize Giveaways | Sites claiming you’ve won expensive items but requiring personal information or “processing fees” | “free-iphone-winner.com” – Informed visitors they’d won the latest iPhone but required $50 “shipping insurance” payment via gift cards |
| Fake Job Offerings | Remote positions with minimal qualifications but excellent pay, requesting upfront payments or sensitive documents | “remote-careers-hub.com” – Offered $35/hour data entry jobs but required $200 “training fee” and copies of identity documents |
Case Study: The Anatomy of a Sophisticated Phishing Operation
In January 2024, our security team investigated a phishing campaign that was consistently flagged by Avast’s URL:Scam detection. The operation, which we named “PhishNet24,” demonstrates the sophisticated techniques modern scammers employ:
The attack began with emails appearing to come from Microsoft, alerting users to “unusual sign-in activity” and directing them to “secure-microsoft-verify.com” (a fraudulent domain). Upon clicking the link, users saw an exact replica of Microsoft’s login page, with these hidden technical elements:
1. Real-time validation: The site verified email formats instantly and rejected obviously fake emails to appear legitimate.
2. Geolocation targeting: Users from different countries saw localized versions of the login page with appropriate language and branding.
3. Anti-detection measures: The site checked for virtual machines and security tools, showing benign content to potential investigators.
4. Seamless redirection: After collecting credentials, users were redirected to the actual Microsoft site, making many victims unaware they’d been compromised.
This campaign affected over 12,000 users before the domains were taken down, with an estimated 22% of visitors entering their credentials. The URL:Scam detection successfully blocked access for Avast users, demonstrating the value of this protection layer.
When URL:Scam Gets It Wrong: Understanding False Positives
While generally accurate, URL:Scam detection occasionally flags legitimate websites incorrectly. Based on our analysis of user reports, these false positives typically occur with newly launched legitimate websites that lack established reputation data. Financial technology platforms using unconventional payment processing methods are also frequently affected. Content delivery networks serving legitimate content through technical domains might trigger these alerts, as can sites after major platform updates that change their technical fingerprint. Additionally, regional e-commerce sites with limited global presence often face these false positive detections due to their lower visibility in global reputation databases.
Recent notable false positive cases include the eToro trading platform and several Fandom Wiki pages including DC Universe and League of Legends wikis. These typically occur when sites implement new content delivery systems or undergo significant backend changes.
What To Do When You See a URL:Scam Alert
When you encounter a URL:Scam detection, follow this simple verification process to determine whether the site is truly malicious:
Step 1: Assess Your Familiarity with the Site
First, consider whether you intentionally visited this site and if it’s one you recognize. Be particularly cautious with sites reached through email links, social media messages, or online advertisements, as these are common vectors for scam distribution.
Step 2: Verify the Site’s Reputation
Use additional tools to check if the site is legitimately dangerous:
Step 3: Take Appropriate Action
Based on your verification results:
If the site appears malicious:
- Close the browser immediately
- Run a full system scan with your security software
- If you entered any information, monitor relevant accounts for suspicious activity
- Consider reporting the site to authorities like the FTC or FBI’s IC3
If you believe it’s a false positive:
- Add the site to Avast exceptions (Menu > Settings > Exceptions)
- Report the false positive to Avast through their reporting form
- Consider temporarily disabling Web Shield just for that specific browsing session
Real User Experience: “How URL:Scam Saved My Business Account”
“I received what looked like a legitimate email from Microsoft about suspicious activity on my business Office 365 account. When I clicked the link to ‘secure my account,’ Avast immediately blocked it with a URL:Scam warning. I almost overrode it because I was concerned about my account, but decided to check directly with Microsoft instead by manually typing office.com in my browser.
When I logged in normally, there were no security alerts on my account. The email had been a sophisticated phishing attempt, and the URL:Scam detection prevented what could have been catastrophic access to my business documents and email. What impressed me most was that the scam site was new – created just hours before – yet Avast’s detection was able to identify its malicious nature.”
– Michael K., Small Business Owner
Advanced Protection: Going Beyond URL:Scam Detection
While URL:Scam detection provides valuable protection, implementing a multi-layered security approach ensures more comprehensive defense against online threats:
DNS-level Filtering: Services like CleanBrowsing or Quad9 block malicious domains at the network level, stopping threats before they reach your browser.
Browser Security Extensions: Tools like uBlock Origin add another layer of protection against malicious sites and content.
Email Security Awareness: Since many scam sites are accessed through email links, using email filtering and practicing careful link verification before clicking can prevent exposure to these threats.
When URL:Scam Alerts Indicate System Infection
If you’re experiencing frequent URL:Scam alerts without intentionally visiting suspicious sites, your system may be compromised with adware or a browser hijacker. These malicious programs redirect your browsing traffic to scam sites to generate revenue for attackers.
For comprehensive cleanup, GridinSoft Anti-Malware effectively removes these threats:

After running a full system scan, you’ll see detected threats categorized by severity. Remove all threats using the “Clean Now” button:

The cleanup process handles browser hijackers, adware, and other potentially unwanted applications that might trigger URL:Scam alerts:

Related URL Detection Types: Understanding the Full Ecosystem
URL:Scam is part of a family of web protection mechanisms. Understanding how these relate helps contextualize the warnings you see:
| Detection Type | What It Means | When You’ll See It |
|---|---|---|
| URL:Blacklist | Site is on a confirmed malicious domain list | When visiting known malicious sites with established threat history |
| URL:Phishing | Site specifically designed to steal credentials | When accessing pages mimicking login forms for banks, email, etc. |
| URL:Malware | Site distributes malicious software | When visiting pages attempting to download unwanted programs |
| URL:PUP | Site offers potentially unwanted programs | When accessing software bundlers or adware distributors |
Conclusion: Balancing Security and Usability
URL:Scam detection provides valuable protection against online fraud, but requires informed judgment to balance security with accessibility. By understanding what triggers these alerts and how to verify potential threats, you can maintain both safety and functionality in your online activities.
Remember that online threats constantly evolve, making a multi-layered approach to security essential. Combining automated protections like URL:Scam detection with informed browsing habits and regular system maintenance provides the most effective defense against the sophisticated landscape of online fraud.
If you’re experiencing persistent security issues, explore our guides on removing browser redirect viruses and resetting browser settings for additional assistance.