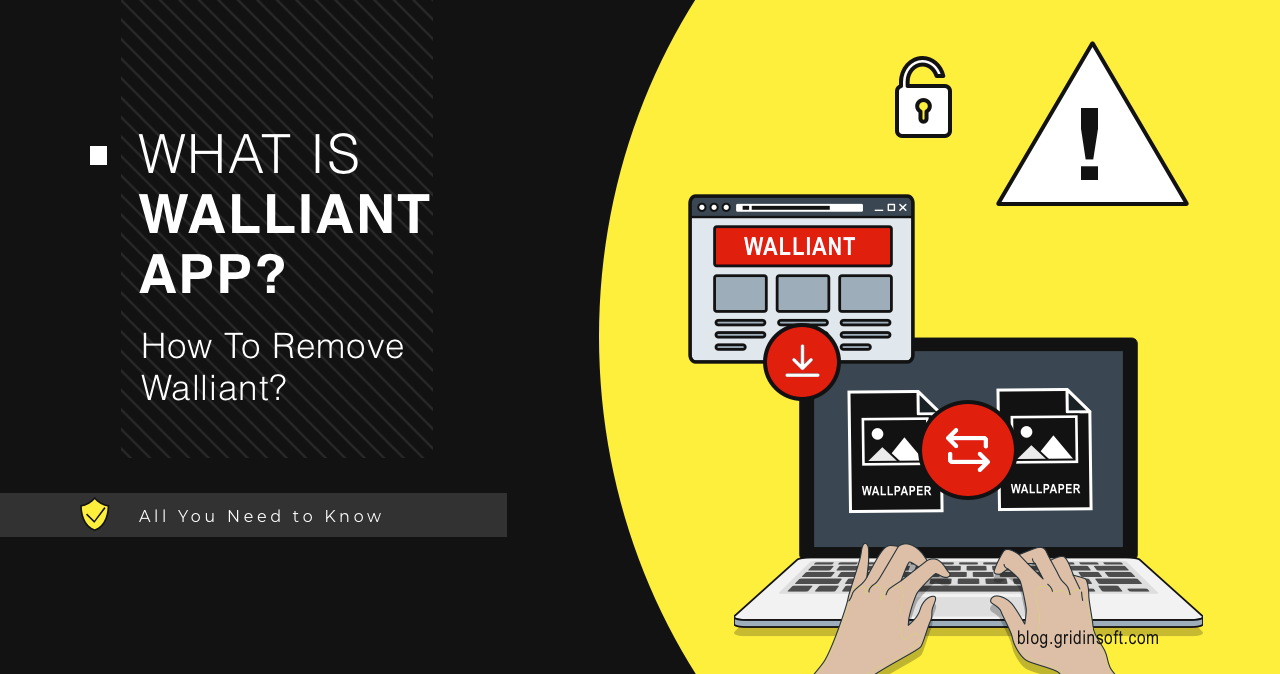
The Walliant application is a Potentially Unwanted Application (PUA). It is promoted as an app that automatically changes desktop wallpapers. Though it in fact has hidden functionality: hijacking your bandwidth, it works as proxyware. This can eventually lead to rather unpleasant consequences.
This unwanted app has a website that allows users to download it. However, in most cases, users do not install it purposefully. This application most commonly arrives as additional software in bundles.
What is Walliant App?
Walliant is a program that automatically changes the wallpaper on your desktop. It belongs to the potentially unwanted applications (PUA) class and has hidden functionality. However, unlike its brethren, which report about non-existent problems or display ads, Walliant falls under the category of proxyware. It turns the system into a proxy node and allows third-party traffic to pass through it.
Like any unwanted software, Walliant gets installed unpredictably, without user confirmation. Although it has an official website, users rarely get this app from that site. The most common way of Walliant distribution is software bundles, a.k.a “recommended software”. Alternatively, users may reach the application’s website unwittingly as well, after numerous redirects and malicious ads.
Is Wallian a Virus?
Wallian is not a virus in the literal sense of the word. It doesn’t steal information or change any system settings. Although it is nominally an automatic wallpaper changer app, it is a potentially unwanted software. Its primary function lies in monetizing through a proxy module.
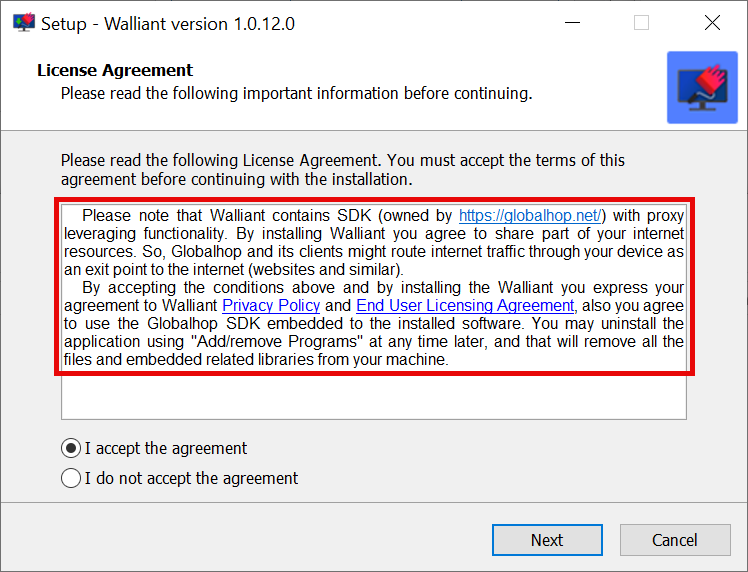
Walliant utilizes the Globalhop SDK for marketing data collection, search results, proper ad placement, and similar operations. However, Globalhop has notoriety and was caught generating illegitimate traffic. This means that the device could be handling unauthorized or even harmful traffic.
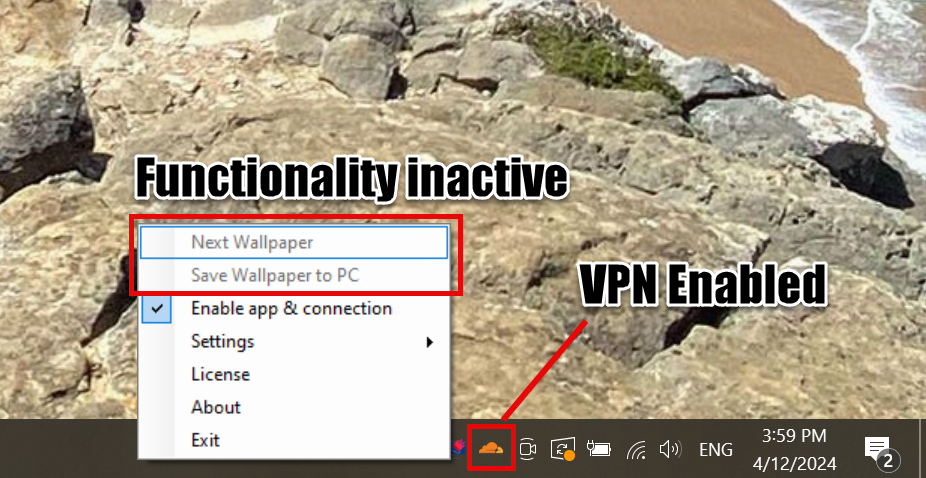
As for its stated functionality, it works correctly only if no VPN or proxy is running on the system. In my example, the program did not start with Cloudflare’s VPN enabled. Thus, the program’s functionality becomes unavailable if you run Walliant and enable the VPN. This indicates that the program does not accept anonymized connections – a rather unpleasant sign.
By the way, the quality of the wallpaper barely reaches HD. Owners of 2K and 4K displays should not expect an acceptable result. And considering that the latest Windows versions have a built-in dynamic wallpaper feature, the need for an app like Walliant becomes even more questionable

Dangers of Walliant
One of the main drawbacks of what Walliant does to the system is the significant reduction in the user’s network bandwidth. This can lead to daily issues downloading files or watching content online. Moreover, using such software could incur additional financial costs due to exceeding data limits if you use a metered Internet connection.
Proxy leveraging also can be used to bypass geo-blocking for legitimate purposes. For example, it allows access to reputable websites like online shopping and news sites. However, bad guys can use it for malicious purposes, such as athering personally identifiable data from high-sensitivity websites like judiciary, governmental, and public services. It allows users to visit malware-spreading web pages and register social media and other online accounts in bulk.
It is important to note that some proxy-leveraging apps claim to allow users to generate “passive income.” However, there are no guarantees that they will be used exclusively for legitimate and harmless reasons. Moreover, regardless of whether proxyware promises a financial benefit, it is still considered a threat to device and user safety. Unfortunately, the user will not receive a cent of the profit in this case. Instead, the application developer will get all the profit.
Technical Analysis
Despite being a “soft” kind of unwanted application, Walliant still has some tricks up its sleeve. For instance, it tries to avoid anti-malware software and performs extensive system data collection. Probably, that is justified by the needs of its proxyware part, but as I’ve already said – it is no good. Let’s have a more detailed pick into my findings.
Anti-Behavioral Analysis
The Walliant employs mechanisms to detect the presence of debugging tools. It checks for timing delays using functions like GetTickCount, which measures system uptime in milliseconds to detect if it is running in a virtual environment or being analyzed by security tools.
Discovery
The malware gathers detailed information about the infected system, including hardware configurations, software installed, network settings, and user accounts. Why would the wallpaper changing thing need all of this? The answer does not please – it is what proxyware module needs to function properly.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Connections
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\MachineGuid
HKEY_CURRENT_USER\Software\Microsoft\SystemCertificates
Networking & Proxyware Functionality
As I said above, Walliant acts as a proxy server. It obtains the information from the registry by reading the keys below. This is needed to arrange the connection to the main server.
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
The program has a whole separate module responsible for the proxy functionality. It executes its own selection of commands to get to work.
"%SAMPLEPATH%\0553c8be8524f6dce3006196186853585d336039c2654b971e6bd6b0c57dba79.exe"
"%SAMPLEPATH%\Walliant.exe"
C:\Windows\System32\wuapihost.exe -Embedding
dw20.exe -x -s 1364
How To Remove Walliant?
Like any bundled software, Walliant removal requires comprehensive measures. The best solution is to use GridinSoft Anti-Malware.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.