Hackers Published an Exploit for a Dangerous Vulnerability in GoAnywhere MFT
Hackers published on the network an exploit for a zero-day vulnerability that is actively used in the GoAnywhere MFT administration console. Fortra, the company behind the GoAnywhere MFT, was forced…
ESXiArgs Ransomware Launches Massive Attacks on VMware ESXi Servers
Hosting providers and the French CERT warn that more than 3,200 VMware ESXi servers were compromised by the new ESXiArgs ransomware last weekend as part of a massive hacking campaign.…
IceBreaker Backdoor Emerged, Exploiting New Phishing Way
A new player has appeared in cyberspace, with surprisingly new methods. A previously unknown group attacked gambling and online gaming companies using a yet unknown backdoor, named IceBreaker by researchers.…
Dangerous RCE Vulnerability in GTA Online Fixed
Rockstar Games has finally released a patch for a dangerous RCE vulnerability in GTA Online that allowed loss of game progress, theft of game money, a ban and other unpleasant…
Cryptocurrency Scam “Pig Butchering” Penetrated the Apple App Store and Google Play Store
The Pig Butchering scam, a scam operation that specializes in fake investments in allegedly promising cryptocurrency projects, stocks, bonds, futures and options, was found in the Apple and Google app…
Vulnerability in KeePass Allows Stealing All User Passwords in Plain Text
The developers of the open-source password manager KeePass explain that a vulnerability that allows an attacker to steal all user passwords is not so dangerous. The fact is that the…
Change in the IP Address of the Router Caused a Massive Outage of Microsoft Services
Last week, Microsoft 365 services around the world suffered a major outage that lasted about five hours. As the company said now, the problem was caused by a mistake when…
Microsoft Will Block Excel XLL Files Downloaded from the Internet
Microsoft developers are going to block some Excel add-in (.XLL) files for Microsoft 365. The new measures will include automatic blocking of such files downloaded from the Internet. Let me…
Ransomware Revenues Dropped by 40% because Victims Refuse to pay
Ransomware revenue (from ransomware attacks) has fallen from $765.6 million in 2021 to $456.8 million in 2022, according to Chainalysis blockchain analysts. Experts attribute this drop of more than 40%…
Cybersecurity Specialists Advise Players Not to Enter Grand Theft Auto (GTA) Online due to a Dangerous Bug
Players of the PC version of Grand Theft Auto (GTA) Online are alarming as a vulnerability has been discovered in the game that can lead to the loss of game…
Attackers Can Use GitHub Codespaces to Host and Deliver Malware
Trend Micro reports that the GitHub Codespaces cloud development environment, available to the public use since November 2022, can be used to store and deliver malware, as well as malicious…
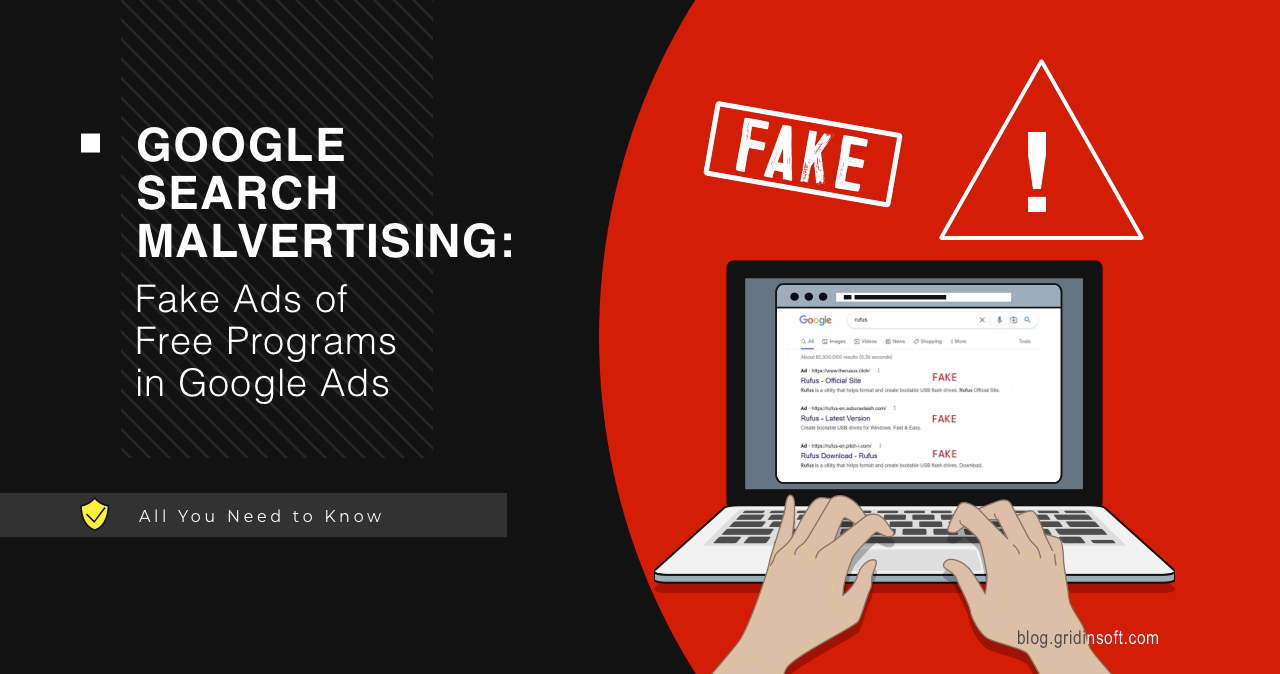
Google Search Malvertising: Fake Ads of Free Programs in Google Ads
Google Search malvertising is an unpleasant phenomenon of malicious advertisements in search engine results. Ads up there are called to make it easier to find users interested in specific queries,…