Backdoor and Reverse Shell are very similar, which may lead you to believe they are the same thing. But take your time with conclusions on this point; we have given you the below guidance on the difference between the two mechanisms.
What is Backdoor?
Backdoors are methods of bypassing a computer’s security measures that aren’t noticeable. For instance, a Trojan backdoor could provide access to a computer, network, or software by an unauthorized user. Unlike other viruses, backdoors penetrate the OS under the guise of a driver or the other program that runs on a deficient level. According to the hierarchical ring system, backdoors reside on Ring 2 and run at the same priority as the OS core. Anything running on Ring 2 can control all the processes on Ring 3 and 4. From this, we see that integration at such a deep level allows an attacker to access the entire system.
How does Backdoor work?
Botnet computers often become “zombies” when infected with a backdoor. Machines controlled by the botnet continue to operate normally until they receive a command from the control server. Once a backdoor opens, lightweight variants of the backdoors often emerge to help expand the botnet. Machines masquerading as their genuine owners launch DDoS attacks and spam to achieve anonymity. When this happens, you may be banned from sites you’ve never visited. But this is just one way how backdoors work. But most often, it sends spam with itself in an attached file or link via an infected PC.
Because of the programs they can install with a computer, cybercriminals often use active backdoors to introduce additional malware into victims’ systems. This doesn’t always lead to new virus injections; however, it’s possible every time someone uses a backdoor.
What is Reverse Shell?
Attackers take control of a system that has been compromised by gaining access to the operating system’s command prompt with arbitrary commands for execution. They then use this access to obtain increased privileges and completely take over the operating system. Reverse shells allow crooks to connect to a remote computer through a firewall when conventional methods are impossible. However, most firewalls and remote shell connections are difficult to bypass.
How does Reverse Shell work?
To set up a typical remote shell, an attacker-controlled computer connects to a remote network host and requests a shell session — this is called a bind shell. But what if the remote host cannot be accessed directly, for example, because it doesn’t have a public IP or is protected by a firewall? In this case, a reverse shell can be used, where the target computer initiates an outbound connection to a listening network host and establishes a shell session.
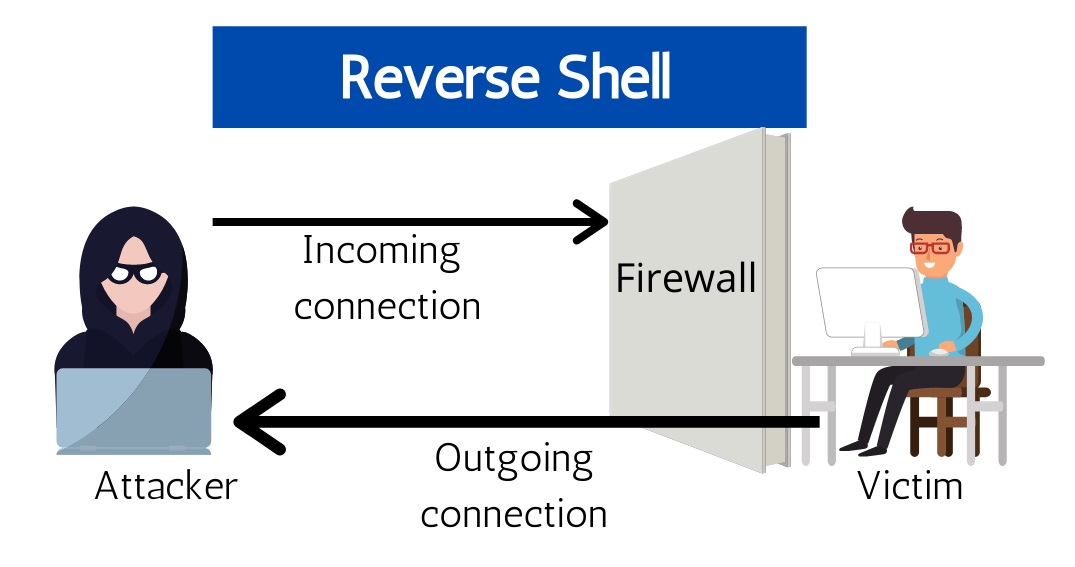
Reverse shells are often the only way to manage hosts behind a NAT remotely, so they have legitimate administrative purposes. However, cybercriminals can also use them to execute operating system commands on hosts protected by incoming connections from firewalls or other network security systems. For example, the malware installed on local workstations via phishing emails or malicious websites can initiate outbound connections to command servers and provide hackers with reverse shell capabilities. However, firewalls filter inbound traffic, so outbound connections to listening servers are usually successful.
What are the Differences between Backdoor and Reverse Shell?
Backdoor is a more general term. For example, the ability to log into a system with a default password is a backdoor. Still, it only gives you unauthorized access to the system, not actual remote code execution or remote shell (unless the system provides such a capability). Special code that leaks secret data from the target system is also a backdoor but doesn’t allow you to run commands on the target system.
A reverse shell runs a command remotely, and a backdoor is a shellcode or exploits you plant on your device to make a reverse shell possible. Backdoor also gives access, but in another way. It also is used as a full-fledged malware, which can add to the infection or modify the system as needed. And the reverse shell no longer gives access to the infected system on the network. It is one of the mechanisms that hackers use.





