“Windows Defender Security Center” is a scam message that comes from a fake website. This fraud is built on the inexperience and trust of Internet users. Now I will tell you how it works and how not to become a victim of it.
Windows Defender Security Center Scam Overview
“Windows Defender Security Center” is a fake malware alert that appears on various scam websites. Users often land on these pages unintentionally, while browsing other websites. In certain cases, a browser hijacker may be responsible. Such viruses have leading users to sketchy pages as their main target, and scams is just another destination.
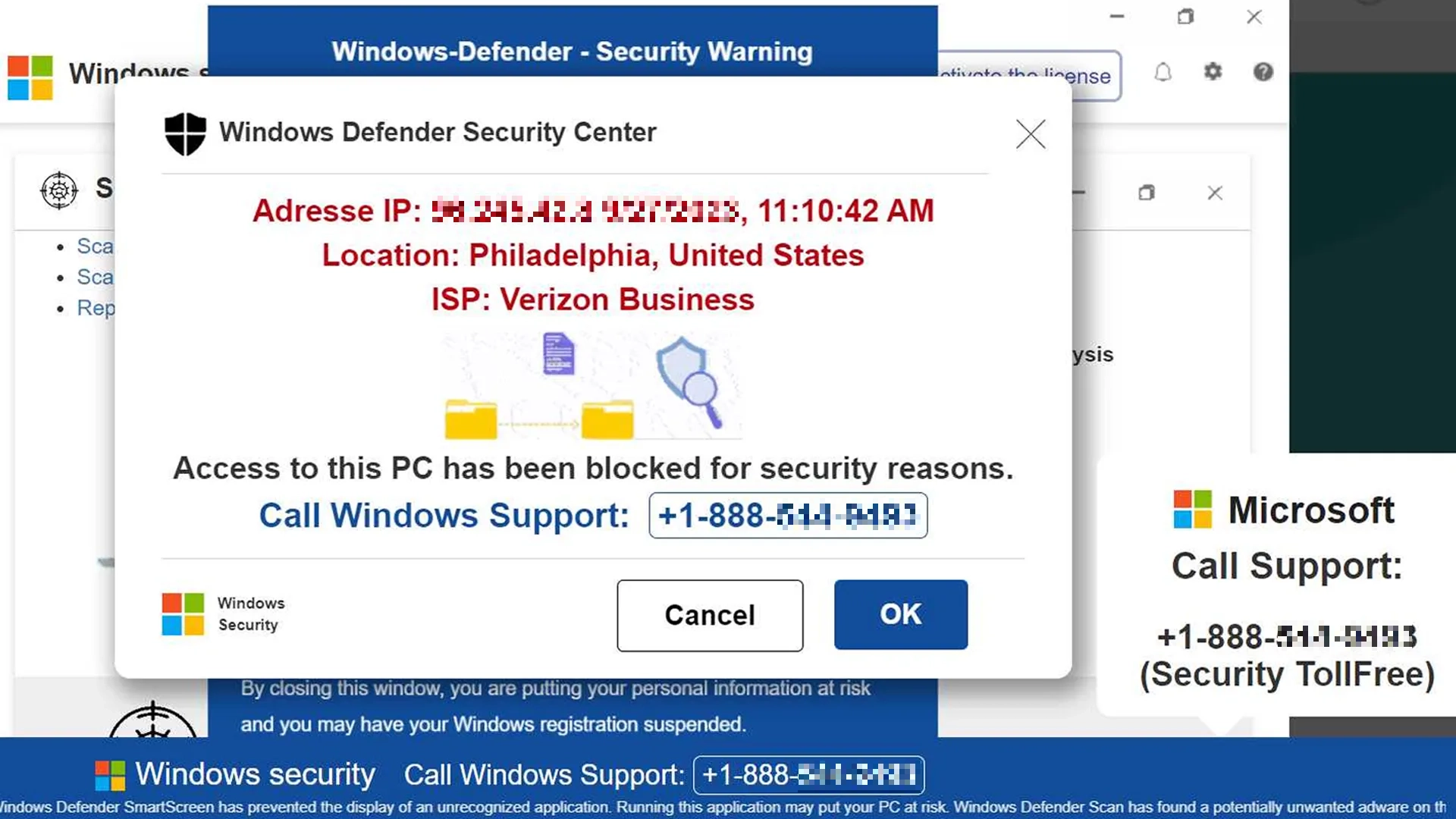
The scheme is simple: the fake alert warns the victim, that its system is infected with multiple viruses. It urges calling a provided number, which typically connects the victim to a call center, usually in another country.
There, scammers insist that the computer is severely compromised and offer a «solution». They ask the victim to install a potentially an app, that will resolve the problem. But instead of a solution, users get an unwanted application (PUA). Once installed, this software runs a fake scan, detects non-existent threats, and demands payment for an “activation” that does nothing.
How Windows Defender Security Scam Operates?
First part of the scam takes place on a website that pretends being a Microsoft malware alert notification of some kind. It is quite easy to get one opened in the background tab while browsing sketchy websites with pirated movies or games. The title of the website – Windows Defender Security Center – is what has given the scam campaign the name.
When an unsuspecting user clicks anything on that website, it extends into a fullscreen mode, and starts playing a scary AI-generated voice message. It states something along the lines of “your computer is infected and we locked it to stop the malware, contact our support immediately”. The exact text may change from one scam site to another, but the overall story is always the same.
One trick that this site pulls out is the altered out-from-fullscreen key sequence. F11 or short Esc button pressing do nothing, as con actors who designed that page changed it to long Esc press. And that is a way to get out of that scam with no calls to a “tech support”.
Crooks posing as “Microsoft-certified technicians” instruct victims to grant remote access, pretending to diagnose issues. In reality, they plant additional junkware, modify system settings, and pressure users into paying for unnecessary services.
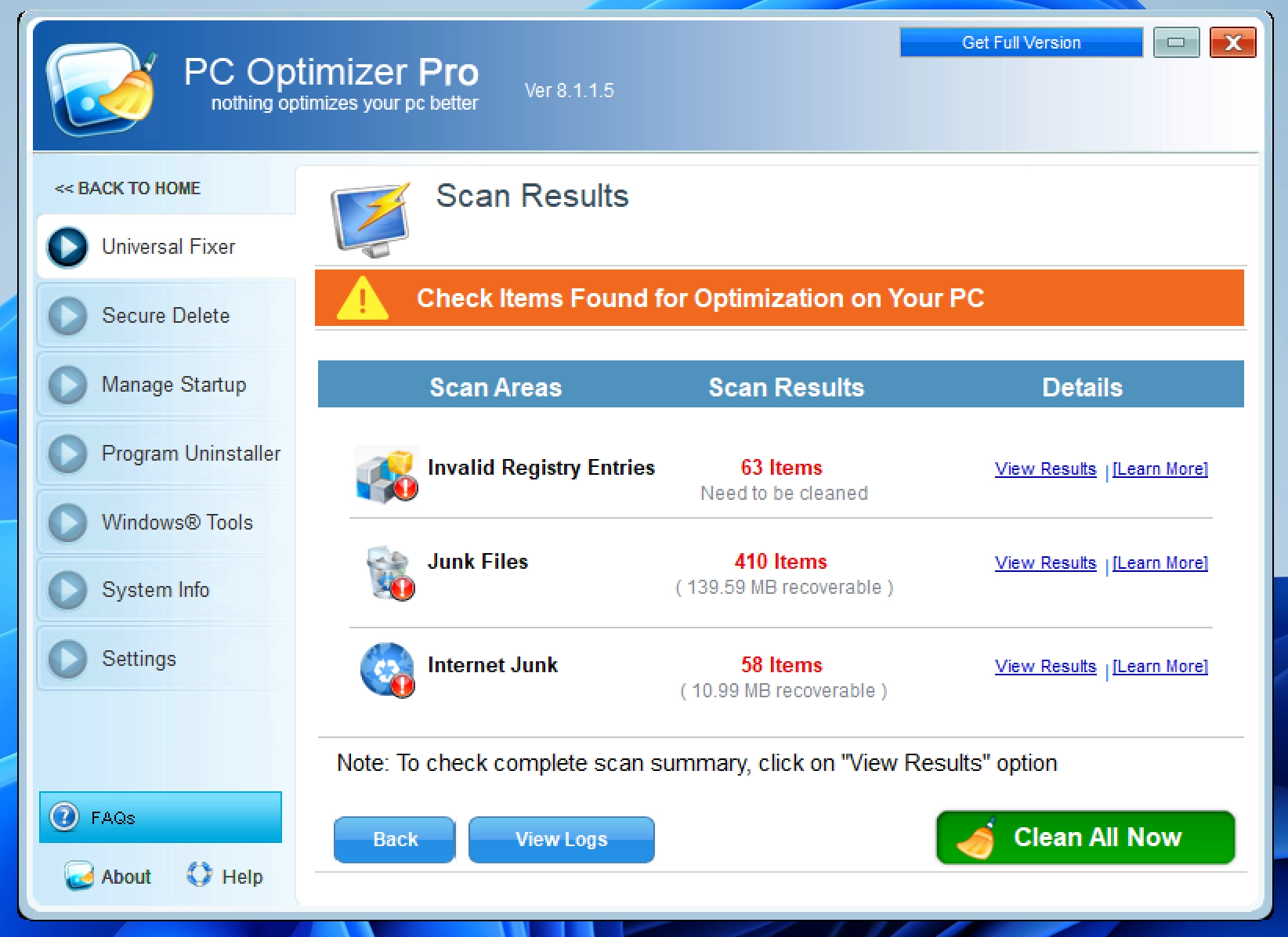
These programs frequently display fake security warnings, convincing users that urgent action is necessary. After running a sham system scan, the software presents a long list of supposed infections. However, the “free” version conveniently cannot remove them. Apps push the victims to purchase the full version, which merely clears the list — without providing any real protection or optimization.
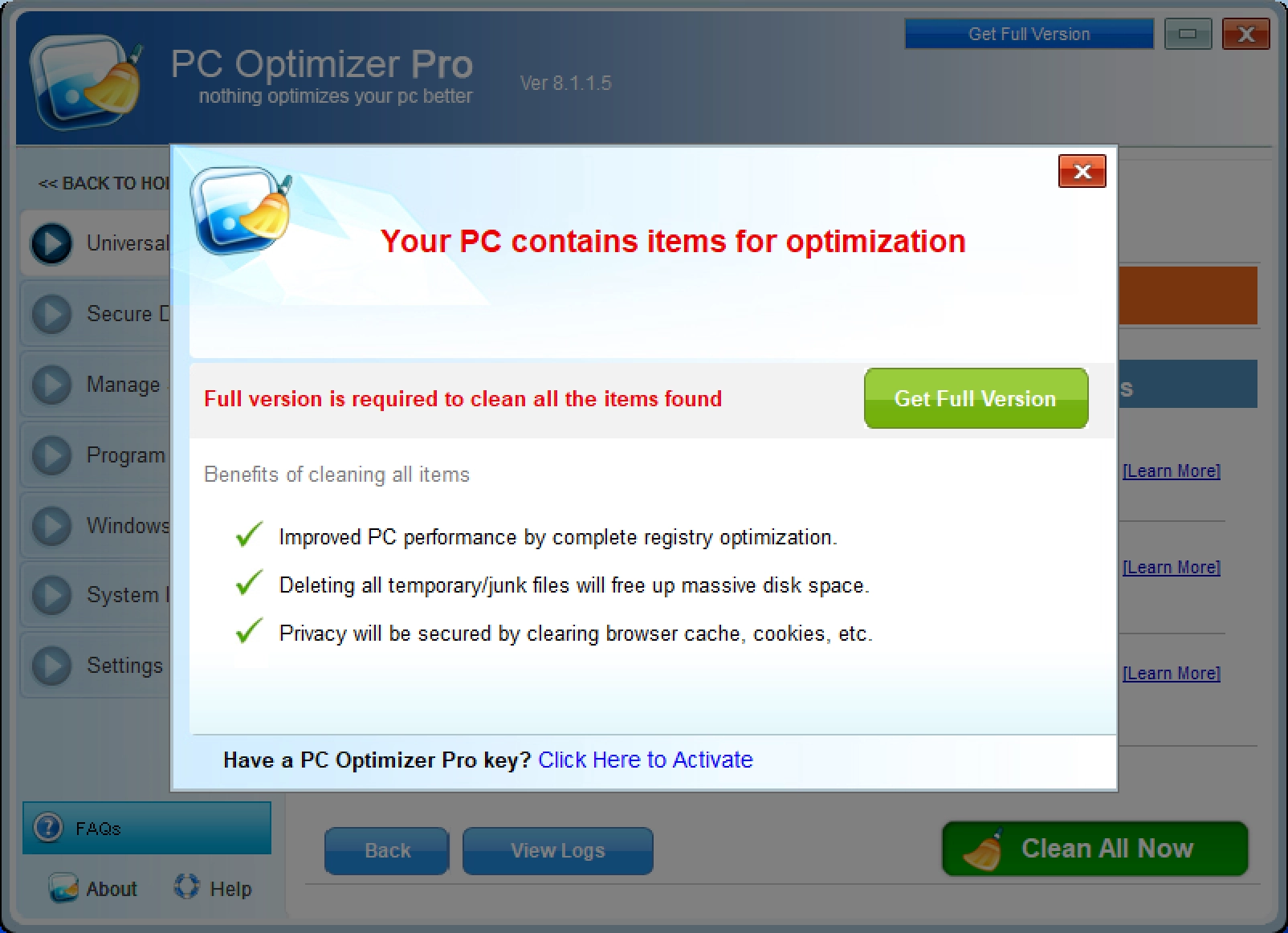
To make matters worse, scam websites often employ browser-locking scripts, preventing users from closing the page. PUPs also are notorious for injecting aggressive advertisements – pop-ups, banners, and in-text ads – disrupting the browsing experience and sometimes covering legitimate website content. These ads can lead to malware-laden pages or execute drive-by downloads, silently installing additional threats. Even a single misclick can result in severe infections.
Another critical concern is data tracking. Many PUPs harvest user information, including IP addresses, search history, visited websites, and in some cases even keystrokes. However, the last one characterizes the threat of the other type – spyware. In any case, this data is sold to third parties, potentially leading to privacy breaches, targeted phishing attacks, or even identity theft. Some PUPs go further by mining cryptocurrency or running background processes, significantly degrading system performance.
How Do PUPs Infiltrate the System?
Many PUPs get into the computer without explicit user consent, often bundled with freeware or delivered via misleading ads. While some PUPs have official websites, most spread through deceptive methods. Developers rely on “bundling” — hiding unwanted programs inside installation packages of legitimate software.
Since many users rush through installations without reviewing options, they unknowingly allow PUPs onto their systems. These unwanted programs are often concealed within “Custom” or “Advanced” installation settings, which many users overlook. Intrusive ads also play a role, redirecting users to sites offering fake downloads or deceptive prompts, leading to unintentional PUP installations.
How to Prevent PUP Infections?
To minimize the risk of PUP infections, users must adopt cautious browsing habits. This is especially important when visiting streaming, gambling, or adult content websites. Downloading software should be done exclusively from official sources, as third-party downloaders often distribute bundled PUPs. When installing software, reviewing the “Custom” or “Advanced” settings is crucial to opting out of any hidden programs. If a browser starts redirecting unexpectedly, users should inspect and remove suspicious extensions or applications that may have been installed without their knowledge.
As I said above, scammers rely on social engineering to manipulate users into falling for their schemes. Fraudulent pop-ups often feature spelling mistakes and poor design, making them appear unprofessional. They also employ urgency tactics, such as countdown timers, to pressure users into taking immediate action.
Claims that users have won a prize, despite never entering a contest, are another red flag. Additionally, pop-ups that appear to scan a device for viruses are always fraudulent, as webpages cannot perform such actions. Finally, any pop-up offering an exclusive financial opportunity only for the user is a clear scam attempt.
While most pop-ups do not directly install malware, they can still lead to financial loss or identity theft. Sometimes they can prevent to close web browser. If this happens, the one way to terminate the browser is to use Task Manager or restart the system by physical button on pc/laptop. Upon reopening the browser, avoid restoring the previous session to prevent reloading the malicious page.