Tips & Tricks
Re Captha Version Pop-Ups Virus
Recent user complaints show a new wave of malicious Re Captha Version website pop-ups. Such websites aim to force users…
Taskbarify Unwanted Application
Taskbarify is unwanted software that claims it is a tiny little Windows tweaker. However, it also turns the device into…
Trojan:Win32/Vigorf.A
Trojan:Win32/Vigorf.A is a generic detection of Microsoft Defender. This detection commonly identifies a running loader malware that may deal significant…
Trojan:Win32/Znyonm
Trojan:Win32/Znyonm is a detection often seen during the backdoor malware activity in the background. Such malware can escalate privileges, enable…
Win32/Wacapew.C!ml Detection Analysis & Recommendations
Win32/Wacapew.C!ml detection refers to programs that have suspicious properties. This can be either a false positive or a detection of…
Information Security Threats in Social Media
Social media has become an important aspect of our everyday lives in this age of technology and information. Despite its numerous advantages, social media has raised concerns about protecting personal…
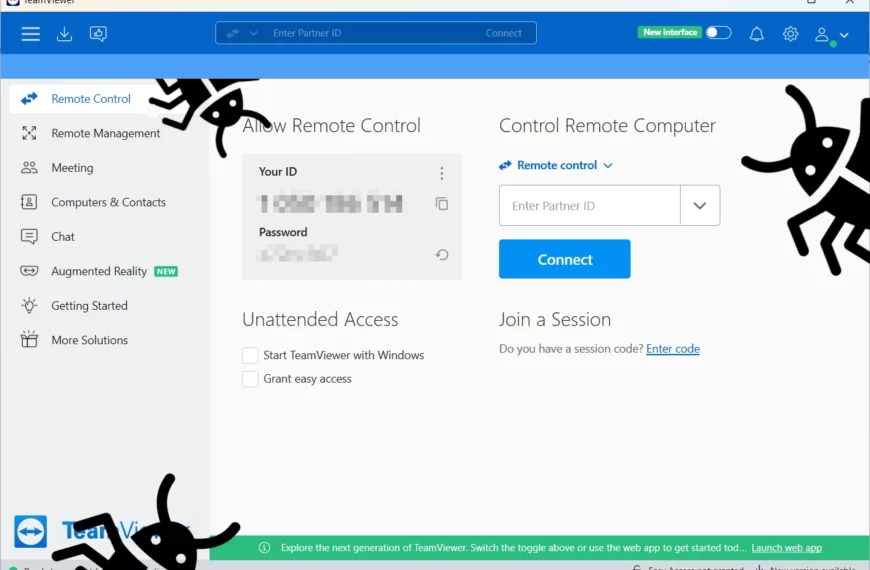
Trojanized TeamViewer Installer Spreads njRAT
Threat actors reportedly started using fake TeamViewer to distribute malware. Their particular favourite for the final payload is the infamous njRAT trojan – an old-timer of the scene. Through the…
Meduza Stealer: What Is It & How Does It Work?
The Malware world evolves constantly, and it would be reckless to ignore newcomers and their potential. Meduza Stealer appears to be a pretty potent stealer variant with its unique features…
Microsoft “nOAuth” is Vulnerable to Simple Email Spoofing
In June, researchers revealed a vulnerability in Azure Active Directory and third-party apps called “nOAuth,” that could result in a complete account takeover. This is just one of the many…
What is Cyber Risk Exposure and How Can You Manage It?
Modern businesses face cybersecurity threats daily. While most are effectively neutralized, a successful attack can lead to unpleasant consequences. Therefore, it is crucial for organizations to clearly understand their vulnerability…
Amazon Prime Day Scams and Fake Amazon Websites
It’s not uncommon for scammers to target online shoppers, often by pretending to be companies like Amazon. However, these phishing attempts tend to increase during major sales events like Black…
Forged Driver Signatures Exploited In The Wild
Hackers actively use driver signature spoofing, which originates from a loophole in Windows kernel-mode drivers handling mechanism. They heavily bear on open-source utilities that were primarily designed for temporal circumvention…
Bed Bath & Beyond Shopping Scams
In late April, 2023, American home goods retailer Bed Bath & Beyond filed for bankruptcy protection under Chapter 11. This event was expected, due to the company’s poor performance over…
How Can Companies Be Secure Against Cyberattacks?
Organizations face an alarming reality in the digital world: data breaches and cyberattacks are becoming more frequent. Cybercriminals find more opportunities to exploit vulnerabilities as reliance on technology grows, and…
Malware Propagation On Darknet Forums
The forums on the dark web are well-known for being a hub of cybercriminal activity, including an auction system. Here, bad actors can trade tips on hacking, share samples of…
Credentials Theft is On The Rise
Email spam has become the prevalent form of phishing and malware spreading for a long time. Among them, credentials theft remains the most common type – even though it is…
How to Protect Your Digital Footprint
The modern business world has been greatly advanced by the internet. Its convenience and numerous benefits have made people from all over the world reliant on the digital world. As…