Modern businesses face cybersecurity threats daily. While most are effectively neutralized, a successful attack can lead to unpleasant consequences. Therefore, it is crucial for organizations to clearly understand their vulnerability to cyber risks and how they can accurately assess this risk. This article will explore the quantitative assessment of cyber threats, their benefits, and how they can help influence key stakeholders.
What is cybersecurity risk?
The digital world is such that hackers constantly explore enterprise networks and supply chains in search of the weakest link. In the event of a successful breach, they can remain undetected for a prolonged period. Moreover, they begin to laterally move to search for valuable information or conduct surveillance for further deployment of malicious payloads. Cyber risk is the sum of vulnerabilities and risks associated with your organization’s digital footprint. Cyber risk is the potential for threats, damages, or losses related to using information technology and digital assets. This includes on-premises and cloud systems, applications, data, networks, and remote devices. Cyber risk encompasses risks related to:
- Cyberattacks
- Cybercrimes
- Data security breaches
- Confidential information leaks
- Personal data breaches
So, cyber risk measurment is essential in today’s information society, and its management and protection are becoming increasingly significant for organizations.
Cyber risk assessment
Ranking risks as high, medium, and low can be interpreted differently. Moreover, knowing which risks to focus on first is difficult, especially when multiple risks are ranked as a medium. However, you can inject accuracy and clarity into your assessments by measuring cyber risk exposure in monetary terms. This helps determine which risks to tackle and where to allocate cybersecurity resources for maximum impact.
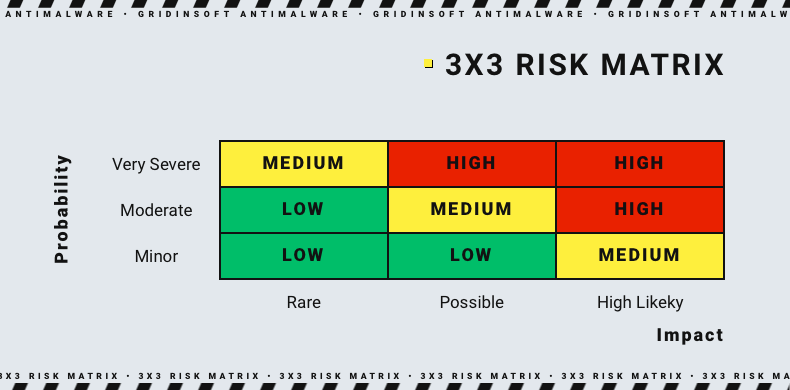
How to manage cybersecurity risk
If you feel that dealing with such a multitude of cyber vulnerabilities will be a challenging task, the truth is, you are right, but it is possible. Managing exposure to cyber risks is an ongoing process that involves continuous identification, prioritization, reporting, and remediation of security issues. It also reduces the risk of vulnerabilities in third-party supply chain links. Understanding the expanding attack surface will allow you to manage your exposure to cyber threats. The following steps will help prioritize vulnerability management and remediation using a combination of people, processes, and technology:
Tools to automatically scan and inventory the attack surface
Automated scanning tools assess and catalog potential vulnerabilities in your digital infrastructure, detecting weaknesses in your network, systems, applications, and devices. They generate reports highlighting identified weaknesses, saving time and ensuring accurate results. These tools are suitable for organizations of all sizes and facilitate continuous monitoring to detect new vulnerabilities as they arise. However, they should be part of a comprehensive cybersecurity strategy that includes regular patching and security awareness training. Having a lot of digital assets can increase the chances of vulnerabilities. In addition, shadow IT can further complicate security. Attack surface scanning can help identify hidden risks and prioritize remediation.
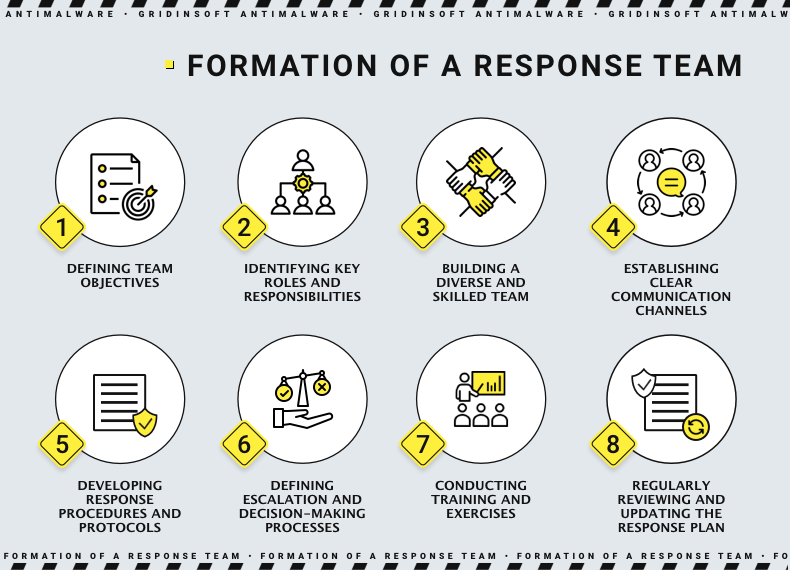
Formation of a response team
Forming a cyber exposure response team is essential to respond to cyber threats and incidents effectively. It includes defining team objectives, identifying key roles and responsibilities, building a diverse and skilled team, establishing clear communication channels, developing response procedures and protocols, defining escalation and decision-making processes, conducting training and exercises, and regularly reviewing and updating the response plan. As we can see, dealing with cyber threats is a team effort that involves different departments.
Organizations can better detect and respond to cyber threats and exposures with a dedicated team. For example, SOC teams handle the immediate threat, while legal and risk management teams manage data and regulatory issues. Communication and customer success teams work on communicating with stakeholders, and HR managers handle employee questions. Regular drills and incident response processes keep the team prepared.
Continuous monitoring
Continuous monitoring for cyber risk exposure involves regularly assessing and evaluating systems, networks, and digital assets to identify potential threats and vulnerabilities. You can do that through automated monitoring tools, real-time threat intelligence, regular vulnerability assessments, patch and update management. Other useful options are log and event monitoring, user behavior analytics, and training for incident response readiness and security awareness. By proactively monitoring cyber risks, organizations can mitigate potential threats and enhance their overall security posture.
Assess risk from third parties
Remember to assess your third-party vendors for cyber risk thoroughly. Many network intrusions and disruptions come from them. Regular security audits and monitoring with risk assessment tools can help you stay proactive and prevent supply chain attacks. Use technology to quickly identify red flags, track security changes, and detect emerging vulnerabilities. Assessing third-party risk is crucial for effective cyber risk management.
- сonduct thorough due diligence
- establish clear contractual agreements
- develop a formal vendor risk assessment process
- implement continuous monitoring
- collaborate on incident response planning
- implement strong data protection measures
- evaluate business continuity and disaster recovery plans
- ensure compliance with relevant regulations
By doing so, organizations can identify potential vulnerabilities, implement appropriate measures to protect sensitive data and minimize overall cyber risk associated with third-party relationships.
Data Security
To protect valuable information from cyber threats, implement robust encryption for data at rest and in transit, enforce strong access controls with MFA, and regularly back up and test data recovery procedures. Periodically review and update security practices to stay ahead of evolving threats. Data integration strengthens data security by consolidating disparate sources into a single platform. This unified approach reduces the risk of data breaches and unauthorized access, ultimately minimizing cyber exposure. CISOs can enhance their company’s reputation for security by being proactive and using innovative approaches to strengthen security. Integrations provide additional capabilities for rich partner data and insights via secondary data points relating to vulnerabilities and security scores for each asset.
Implementing a data integration strategy enhances security, improves quality, and streamlines workflows. In addition, it ensures compliance and gains insights for B2B companies in a data-driven world.




