LastPass, owned by GoTo (formerly LogMeIn) and with over 30 million users, revealed new details about the cyber incidents that have shaken the company since August 2022, when fragments of source code were reported stolen. In January 2023, the company admitted that the breach was more extensive, involving leaks of accounts, passwords, MFA settings, and licence information.
LastPass breach is much more encompassing
As the investigation discovered, hackers successfully made it into the DevOp engineer’s LastPass home computer as part of a lengthy targeted attack. Deploying malware allowed them to access corporate data on cloud storage resources. The unnamed attacker used the stolen data from the August incident to plan and execute cloud storage reconnaissance and exfiltration efforts between August and October 2022. In doing so, the attackers took advantage of an RCE vulnerability in a third-party multimedia software package by injecting a keylogger on the LastPass employee’s personal computer. After that, they were able to intercept the master password and gain access to the DevOps engineer’s corporate vault.
The attacker then exported all available records and the contents of shared folders. They contained encrypted notes with the access and decryption keys needed to access the production environment, AWS S3 LastPass backups, other cloud storage resources, and some critical databases. LastPass has issued a separate bulletin titled “Security Incident Update and Recommended Actions”, which contains additional information about hacking and stolen data. The company has also developed supporting documents outlining steps customers and business administrators should take to improve account security.
How did the breach go that far?
According to the official note released by the LastPass company, only four of their engineers had access to the aforementioned cloud backup. To grab the password from the S3 bucket, hackers deployed a keylogger using the mentioned CVE-2020-5740 vulnerability in the Plex desktop application. As it turned out in the process of the investigation done by LastPass, Plex was hacked around that period as well. Seems that hackers were either lucky enough to synchronise their efforts with the crooks who broke into the Plex, or they are powerful enough to breach several companies at one time. This or another way, these events are creating a really sick halo around the companies that develop password-keeping solutions.
Currently, LastPass tries to remain transparent on the situation. They claim about “improving [the guilty one] engineer’s home network and personal resources security”, without more precision. Additionally, the company changed all the high-privilege passwords that were allegedly touched by a breach and intends to do the same to the ones with fewer capabilities. How long will it take, and had they located all the compromised elements – this remains an unanswered question.
What’s next?
The list of actions recommended to LastPass users was actually published much earlier, after the first disclosure of the incident in December 2022. That included a notice that customers who used 12-character master passwords (ones that are needed to access the LastPass account) may exhale with relief. Such tough combinations were not exposed in any way. People whose master keys were less strong should change all the passwords they stored within the LastPass. That is likely related to how easy it is to guess these passwords – starting from 12 letters, the smallest complications will render any brute force useless.
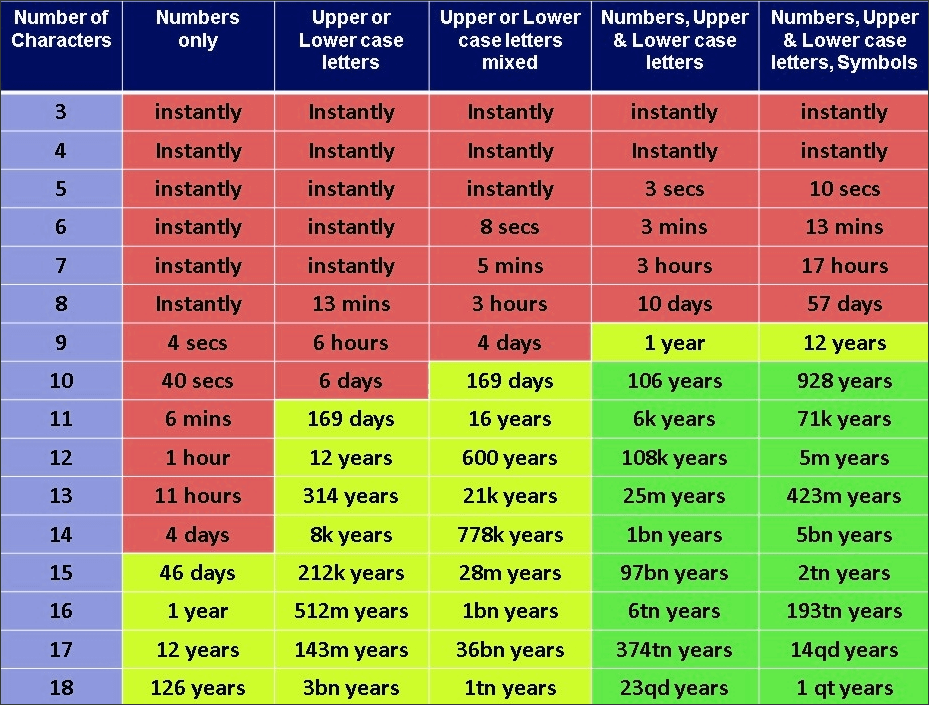
LastPass’ story will be as acknowledged as hacks of Colonial Pipeline, Kaseya, and Twitter. Despite some of the mentioned ends up with ransomware attacks, the data leak outcome is what really unites them all. And while harm from user data leaks or corporate documents exposure does not have a really big potential to expand, leaked passwords do. It may range from having straightforward losing access to accounts as the result of the account hijack to phishing with impersonation – which will most likely harm your image. And what exactly will happen is quite hard to foresee, as hackers usually tend to sell their booty to numerous other scoundrels in the Darknet. For that reason, it is better to have both your social networks and password vault protected with as reliable a password as possible. You can read how to pick a safe password in our article.



