Tips & Tricks
Stopabit Virus
Stopabit is an unwanted application that has almost no useful functionality. Users can see its promotions as a useful tool…
“Account restrictions are preventing this user from signing in”
When working with Windows, users may sometimes encounter the “Account restrictions are preventing this user from signing in” error. This…
SMApps Virus
SMApps is a malicious program that aims at spreading illegal promotions. It mainly attacks browsers by changing settings and redirecting…
Trojan:Win32/Casdet!rfn
Trojan:Win32/Casdet!rfn is a detection that indicates the possible presence of malware on your system. Users may encounter this detection after…
Virus and Threat Protection Page Not Available
Windows 10 and 11 users may sometimes encounter a “Virus and threat protection page not available” message. Although this message…
What Should You Do When You Get Scammed?
As online scams become not only more widespread, but also more sophisticated, it appears to be rather easy to become a victim of one. But what should you do in…
What is Sextortion? Explanation, Signs & Ways to Avoid
Sextortion is a specific email phishing tactic that was around for quite some time. Over the last few years though its popularity skyrocketed, and some novice technologies make me concerned…
What is Catfishing? Explanation & Ways to Avoid
Catfishing appears to be the new-old approach in online phishing. While having less direct threat to the user, it may sometimes create even bigger problems, and inflict emotional damage. But…
Rude Stealer Targets Data from Gamer Platforms
A newly discovered Java-based stealer named Rude has emerged, encapsulated within a Java Archive (JAR) file. It employs a range of sophisticated functionalities and focuses on stealing sensitive data from…
What is Microsoft Security Warning Scam?
Fraudsteds massively employ Microsoft Azure hosting to start Microsoft Security scam pages. They range from a scary warning that blocks your browser window to a phishing pages, indistinguishable from real.…
How to Disable Windows Defender? Windows 10 & 11 Guide
“Disable Windows Defender” has become a particularly popular advice to the users who want to speed up their computer. Though, not all of them mention the actual way to disable…
Top Maine Lobster Scam on Facebook
Another fraudulent scheme related to the sale of seafood has appeared on Facebook. Fraudsters promise lobster at an excellent price, but the result is little pleasant for the buyer. What…
Halloween Shopping Scams — Ways to Detect & Avoid
2023 Halloween, similarly to other holidays and events of this year, will likely become a topic of a huge number of shopping scams. Con actors create websites that offer purchasing…
“Professional Hacker” Email Scam Revealed & Explained
Among hundreds of different types of scam emails, there is a specific scary one that bothers people around the world. Known as “Professional Hacker” scam email, it claims that an…
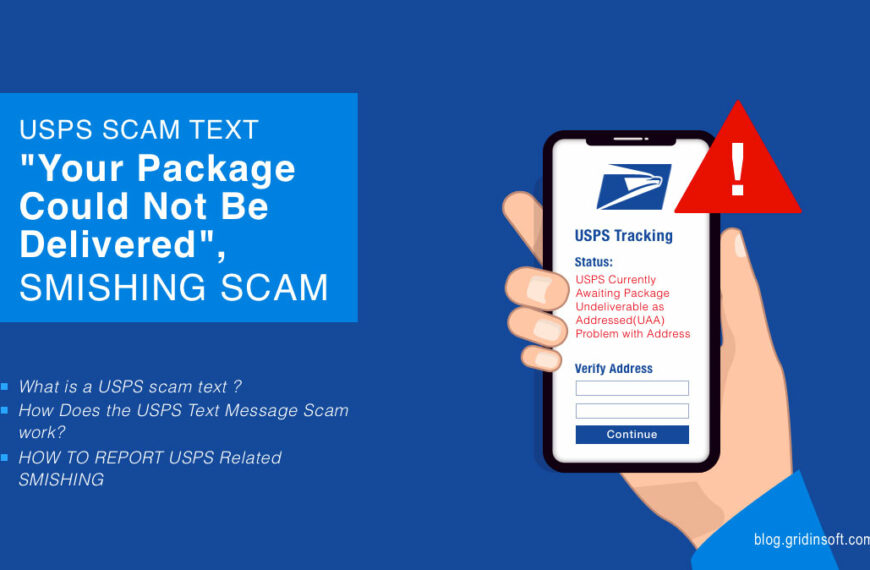
USPS Scam Text 2024: “Your Package Could Not Be Delivered”
To phish, attackers use a text message that forces targeted individuals to take a specific action. This can include downloading malicious programs to the recipient’s phone or disclosing private information.…
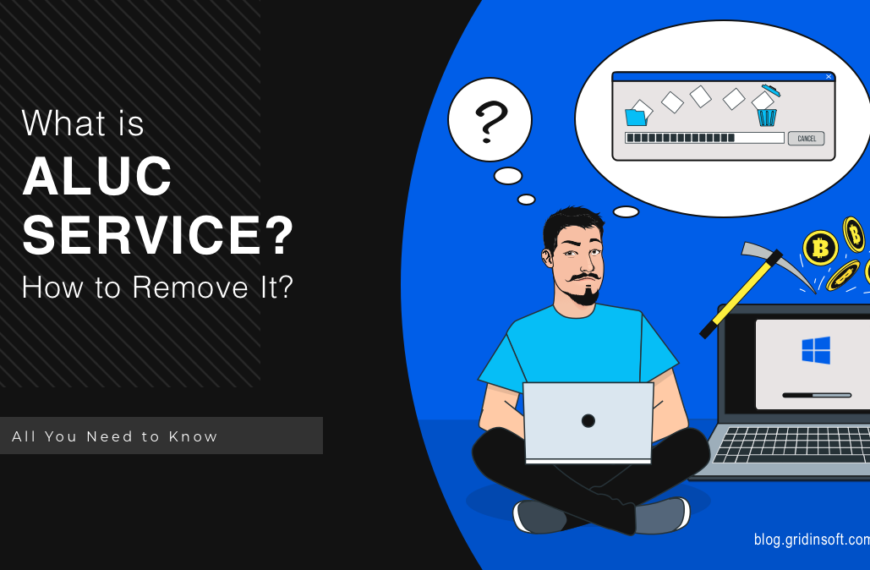
Aluc Service: What Is Aluc App & How to Remove?
Aluc Service is a strange service you can spectate in the Task Manager. It is, in fact, a malware-related process that hides behind a legitimately-looking name. Most commonly, such a…
What are Whaling Phishing Attacks?
Malicious actors know executives and high-level employees, such as public spokespersons, are familiar with common spam tactics. Due to their public profiles, they may have undergone extensive security awareness training,…