3 Unpopular Malware Spreading Ways in 2023
The modern Internet space is like an endless ocean, where every wave…
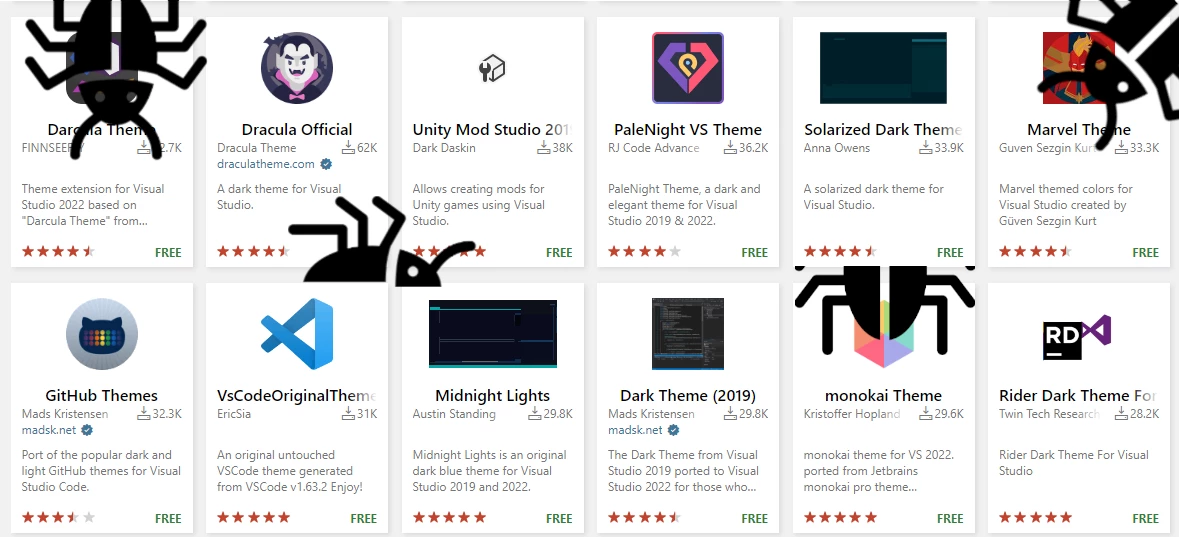
Visual Studio Code Malicious Plugins Steal Personal Data
Some plugins for Visual Studio Code, a popular code editing tool developed…
RedLine Stealer Issues 100,000 Samples – What is Happening?
Throughout the entire early May 2023, GridinSoft analysts team observed an anomalous…
Grand Explorer Software – Remove Malware & Repair System
Grand Explorer app, or, as it is displayed in the list of…
Fake Windows Update in Browser Deliver Aurora Stealer
Fake Windows Update became a malware spreading way once again. Updates are…
LOBSHOT malware steals cryptowallets, exploits Google Ads
LOBSHOT, a recently-detected malware family, appears to be a new strong player…
PaperCut Vulnerability Allows RCE, Exploited in the Wild
PaperCut, a software solution used for print management, appears to be vulnerable…
Capita Hacked, Black Basta Gang Publishes Data
Capita, a London-based international business process outsourcing company, was hacked recently. Users…
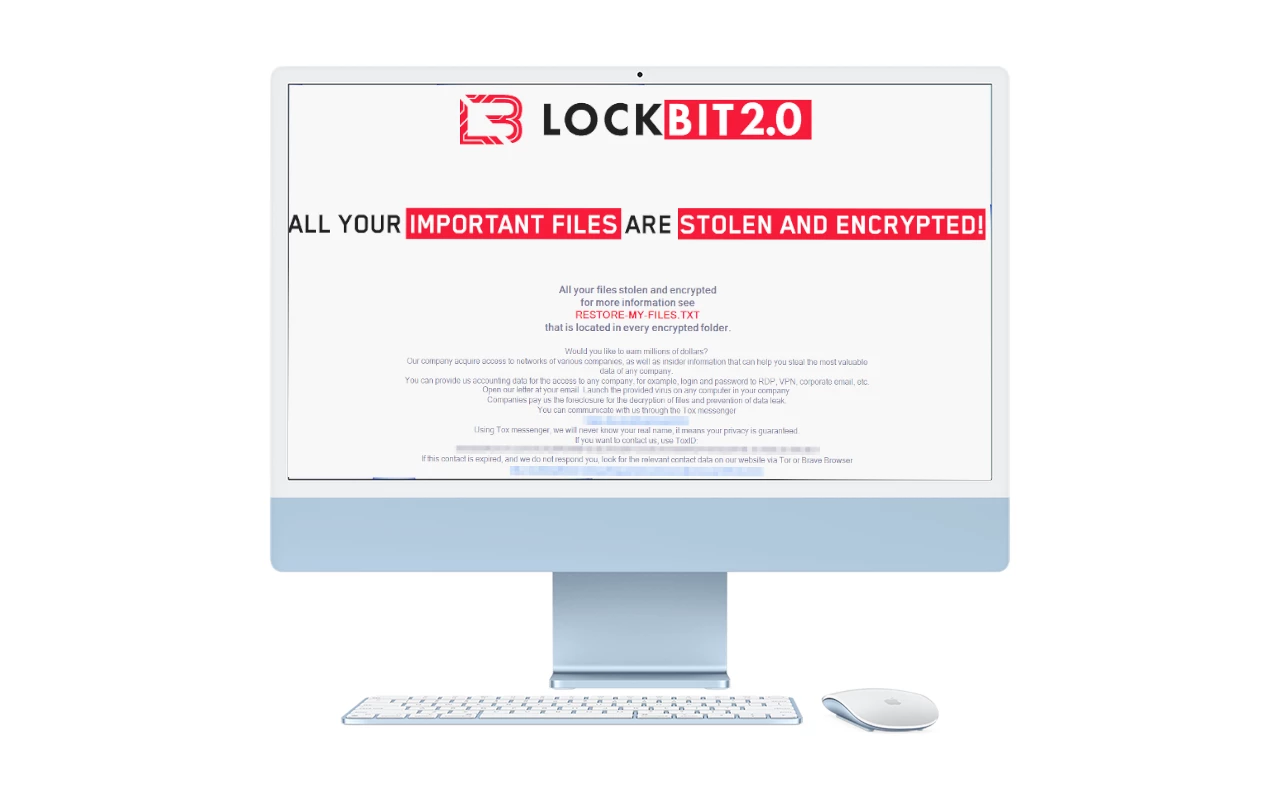
LockBit Releases World’s First macOS Ransomware
LockBit, an infamous ransomware gang that became a major threat actor over…
Domino Backdoor is Lead by FIN7 and Conti Actors
A new Domino Backdoor popped out at the beginning of 2023. Since…
PDF Virus
Among numerous other files, PDFs are considered one of the most convenient…
Genesis Market Seized by FBI
Genesis Market, a Darknet marketplace for stolen information, was reportedly seized by…