Spyware is probably one of the oldest but most dangerous types of malware. As the name suggests, spyware is software that spies on you when using your computer or mobile device. To recognize when you’ve been infected and to take steps to remove spyware, it’s essential to be aware of its possible signs. Unfortunately, just because you have malware protection installed doesn’t mean you can ignore those warnings. Undoubtedly the software can protect you, but it is not perfect. Sometimes, a brand-new zero-day malware attack may take time to be detected. However, that is until your protection providers release an update. But what is spyware? How can you see it and protect your devices from it? Read on to learn more about this cyber threat.
What is spyware?
Spyware is any software that collects and transmits information covertly without the user’s consent. It is used to collect target information, usually passwords, credit card and financial information, system files, and sometimes for keylogging or screen captures. There are different types of spyware, and below, we’ll look at the most popular ones. We’ll also look at clear signs that you’re dealing with spyware examples, and give you some security tips.
Red Flags You’re Dealing With Spyware Examples
Unfortunately, it is tough to detect spyware without special tools. This malware type is designed specifically to be stealthy. Visual detection of its activity is an exclusive case, which still does not mean its successful removal. However, some red flags clearly indicate that there is something wrong with your device:
Your System Tools Are Disabled
An attentive user, suspecting the presence of malware, might run the task manager and try to find the culprit of abnormal PC behavior or check the settings with the registry editor. However, suppose you suddenly find that when you try to run these or other system tools, you get a message that your administrator has disabled them. In that case, it may well be an attempt to self-protect the malware on your system.
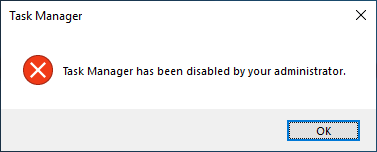
Strange processes in Task Manager
Although spyware works in stealth mode and reads information about the system, the user’s actions, and Internet activity, sometimes it can still show up somewhere or leave a trace in the form of a file. However, even if you find an uninvited guest in your system, you should not expect such a program to have a convenient removal function.
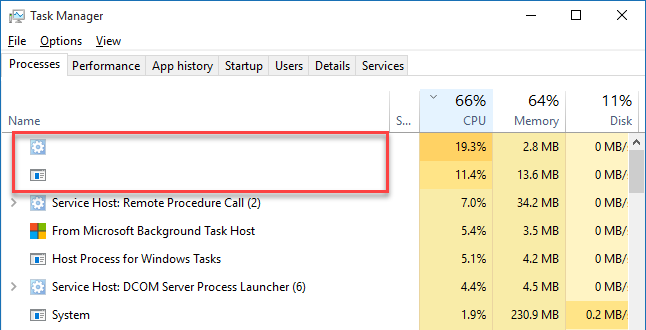
Suspicious network activity
Once the spyware collects enough data, it will send it to the attacker. Depending on the size of that data, your Internet speed may drop because the entire bandwidth will be taken up. In addition, if youhave a limited Internet plan, this can lead to additional costs. Additionally, at the stage of data extraction, you can witness a strange archive somewhere in your file system.
What types of spyware are there?
Although spyware is one category among many types of malware, it can be classified into several other categories. Hackers use different methods to spy on you. Below we will look at the most common ones:
Keyloggers
Keyloggers are probably one of the oldest forms of spyware. They can be either software or hardware. Their purpose is to intercept your keystrokes and transmit them to an intruder. This allows keyloggers to piece together everything you type. However, they are particularly interested in collecting passwords, social security numbers, or anything else that might enable them to impersonate you.
Password stealers
Password stealers are somewhat similar to keyloggers but a bit more sophisticated. Instead of recording all keystrokes, password stealers look for files that can contain a password. Their modus operandi can vary. Some of them are keyloggers at their core, but with the use of complex algorithms to detect certain chains of symbols you type. Others work like Trojan viruses waiting to steal passwords.
Info stealers
Hackers develop info stealers to aim certain data types directly on the victim’s computer. Info stealers often have a form of Trojan viruses. Once a victim activates an info stealer, it collects information from registries and files, including passwords and banking information or even compromising photos or videos. There are also examples of infostealers that aim precisely at a certain file type. Their general application is precise attacks upon a person who has valuable information on its PC.
Browser hijackers
Browser hijackers can modify your browser settings and redirect you to fraudulent websites you did not request. Although this type of malware has more common details with adware, it may also contain spyware components. Browsers hold a lot of personal information about you, thus hackers will likely find something valuable. Cookies, in particular, can give out your login credentials and choices on different sites. All this data is usually sold to third parties, or used for phishing attacks by same threat actors.
Packet sniffer
With a packet sniffer, cybercriminals can connect to a network and obtain all traffic passing through it. A hacker can gain access to login credentials and financial data by tracking Internet usage, including email and instant messages. That’s why sniffers can be dangerous, especially on unsecured Wi-Fi networks. Hackers can sniff unsecured public Wi-Fi networks, intercepting the traffic of anyone using them. Moreover, sniffers are sometimes present in the basic firmware of the network device – a widespread practice among Chinese manufacturers.
Commercial Spyware
Some companies sell spyware that you can intentionally put on your devices. For example, parents can use it to protect their children on the Internet. This type of software is known as parental controls. In addition, some companies use spyware to monitor employees. Although this is not illegal, such software also fits the definition of spyware.
How can I get infected with spyware?
There are different ways to get infected with spyware. Here are some of the most common:
- Clicking on a pop-up window or tooltip without reading what it says
- Opening email attachments from unknown senders
- Downloading pirated movies, music, or games
- Downloading legitimate files bundled with malware
What should I do if my system is infected with spyware?
So, if you think spyware has infiltrated your device, install a powerful antivirus application. Then, manually run an update to ensure that your antivirus contains the latest virus databases and run a full scan. Suppose, for some reason the malware doesn’t allow you to install antivirus software or run a scan. Then you can scan your computer with an aggressive, clean-only tool such as Trojan Killer. Finally, check your defenses once you’ve dealt with the immediate problem. Ensure that your antivirus is fully working and its bases are up to date.





