The Security Blog From Gridinsoft
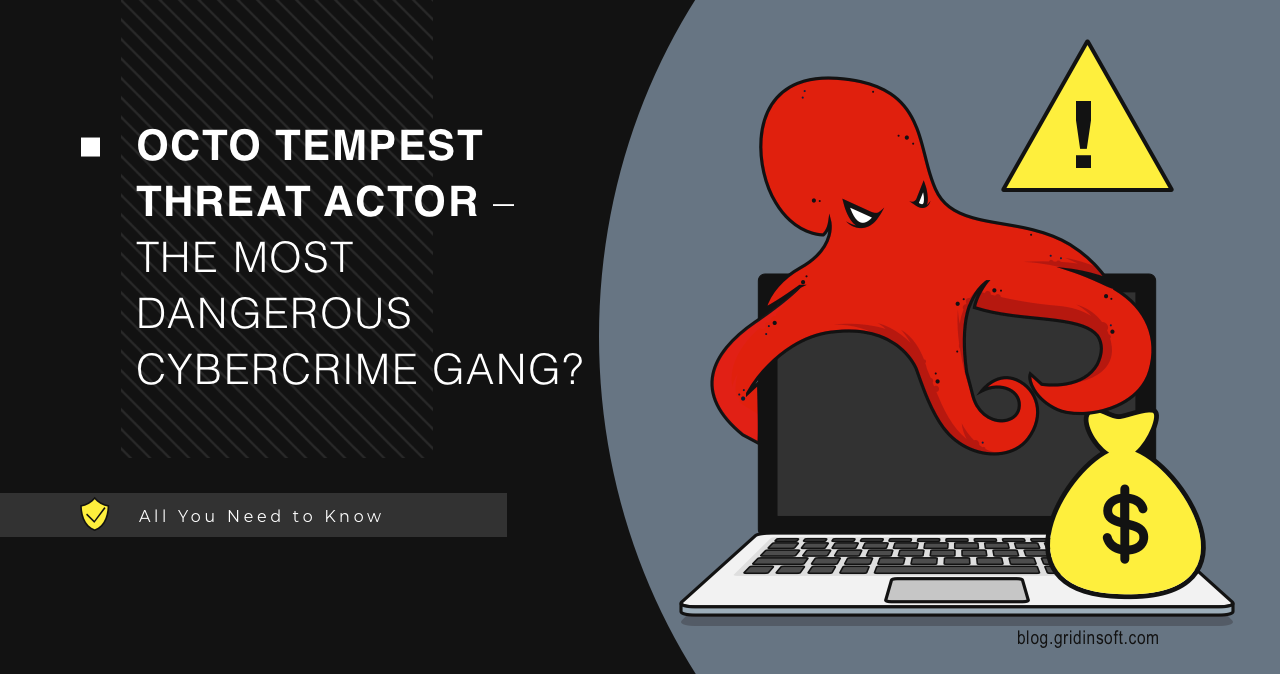
Octo Tempest Threat Actor – The Most Dangerous Cybercrime Gang?
Octo Tempest, a financially-motivated hacking group, has been labeled “one of the most dangerous financial criminal groups” by Microsoft. Known…
IoT Malware Attacks Grow by 400% in 2023
IoT malware has been a major concern over the last decade. However, trends show that things are turning even worse…
WinRAR Vulnerability Allows Arbitrary Code Execution
Over the past few weeks, Google’s Threat Analysis Group (TAG) has reported a worrying trend. Experts have observed government-sponsored actors…
VMware Releases Patch for Critical vCenter Server RCE Vulnerability
VMware has released a patch for a critical vulnerability in the vCenter Server with a high CVSS score. This vulnerability…
1Password Hacked Following the Okta Hack
Recent security breach in the 2FA provider Okta appears to affect some of its clients. Among others, a password management…
Fraudsters arrested for years running fake site to order assassinations
Romanian police have arrested five men behind the dark web’s…
Hack group Lapsus$ returned from “vacation” and announced the hacking of Globant
The Lapsus$ extortionist group has returned from a “vacation” despite…
Russian Aviation agency switched to paper documents due to a hacker attack
The media, citing their own sources, report that at the…
Management of Okta admitted they didn’t immediately disclose details about the Lapsus$ attack in vain
Last week it became known that back in January this…
British police announced the arrest of several members of the Lapsus$ group
Recently, the hack group Lapsus$ mentioned that several of its…
Hackers attack hackers by spreading malware on underground forums
Information security specialists have discovered new evidence that hackers often…
Lapsus$ hack group stole the source codes of Microsoft products
The Lapsus$ hack group has released the source codes for…
Anonymous claims they hacked dozens of CCTV cameras in Russia
Anonymous hacktivists claimed on Twitter that they had hacked and…
The popular node-ipc npm package removes files on systems of developers from Russia and Belarus
The developer of the popular npm package node-ipc has released…
DuckDuckGo downgraded Russian state media in search results
The founder and head of DuckDuckGo, Gabriel Weinberg, said that…
About 30% of critical vulnerabilities in WordPress plugins remain unpatched
Patchstack analysts have released a report on security and critical…
Akamai Researchers Say DDoS Attacks Amplification for 4 Billion Times
This week, Akamai experts discovered a unique DDoS amplification vector…