The Security Blog From Gridinsoft
Kyivstar, Ukraine’s Biggest Cell Carrier, Hacked
On Tuesday, December 12, 2023, Ukraine’s largest cellular operator Kyivstar got its network infrastructure ruined. This is a result of…
New Apache Struts 2 Vulnerability Allows for RCE
A newly discovered critical security flaw in Apache Struts 2, a widely used open-source web application framework, has spurred an…
Malicious Loan Apps in Play Store Decieved 12M Users
Eighteen malicious loan apps on the Google Play Store, posing as legitimate financial services, have scammed users. They offer high-interest-rate…
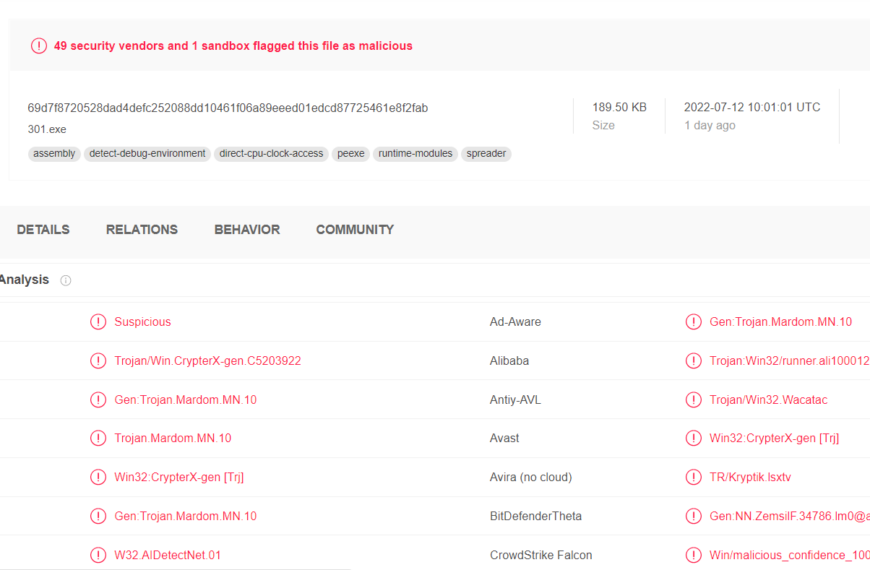
PoolParty Injection Techniques Circumvent EDR Solutions
A set of process injection techniques, named PoolParty, was presented at the Black Hat Europe 2023 conference. A set of…
WordPress Critical Vulnerability Fixed in Patch 6.4.2
WordPress has rolled out version 6.4.2, addressing a critical remote code execution (RCE) vulnerability. Discovered by the project’s security team,…
Candiru Malware Uses 0-day Vulnerability In Chrome
Following Microsoft, Google and Citizen Lab, another revelation came from…
Fraudsters Are Running a Malicious Advertising Campaign through Google Search
Malwarebytes, an information security company, has discovered a large malicious…
Fake DDoS App Targets Pro-Ukrainian Hacktivists
Google Threat Analysis Group (TAG) specialists reported that the Russian-speaking…
CloudMensis Malware Attacks MacOS Users
ESET experts have discovered the CloudMensis malware, which is used…
Cybersecurity Researchers Discovered a New Phishing Kit targeting PayPal Users
Akamai has identified a new phishing kit that is being…
Microsoft Releases PoC Exploit to Escape MacOS Sandbox
Microsoft has detailed a recently patched vulnerability affecting Apple operating…
U2K Ransomware Strikes, Thousands Of Victims
U2K ransomware, probably the rising star on the ransomware arena,…
Emsisoft Released a Free Tool to Decrypt Data Corrupted by AstraLocker and Yashma
Emsisoft has released a free decryption tool for files affected…
TrickBot Hack Group Systematically Attacks Ukraine
IBM Security X-Force experts noticed that from the very beginning…
Bandai Namco Hacked, ALPHV Group Claims
On Monday, June 11, 2022, the information about the cyberattack…
Conti’s blockchain plans: an ominous prospect
Earlier this year, on February 22, Conti’s gang became popular…
Russian Organizations Under Attack By Chinese APTs
Unveiling a recent cyber saga, the experts at SentinelLabs have…