Experts from the Palo Alto Network analysed the Ransom Cartel hacker group’s ransomware and believe that it is very similar to the REvil malware. Although there is no conclusive evidence of a connection between these groups, researchers believe that former members of REvil could have founded the Ransom Cartel.
Let me remind you that REvil was one of the largest and most famous extortion groups. In particular, REvil is responsible for the high-profile hacking of MSP solutions provider Kaseya in 2021, as well as the attack on the world’s largest meat producer, JBS.
There was even a time when REvil spokesman boasted that hackers have access to ballistic missile launch systems.
The group’s apparent activity ceased in January 2022, after the Russian FSB announced the arrest of 14 people associated with the hack group, and searches were conducted at 25 addresses in Moscow, St. Petersburg and Lipetsk regions. At the same time, it was reported that “the basis for the search activities was the appeal of the competent US authorities.”
Then the Moscow court took into custody eight alleged members of the hack group. All of them were charged with the acquisition and possession of electronic funds intended for the illegal transfer of funds made by an organized group.
Later, Russian media reported that the investigation into the criminal case had almost reached a dead end, as the US authorities refused to further cooperate with Russia due to the Putin’s army invasion in Ukraine, and they could only accuse the suspects of fraud with the bank cards of two Mexicans living in the United States.
In December 2021, a new Ransom Cartel ransomware appeared on the scene, which, as experts already noted, is in many ways similar to the REvil malware. Now the malware has been studied by Palo Alto Network analysts, and they also write about a possible connection between the two groups.
The fact is that the source code of the REvil encryptor has never been “leaked” and has not been distributed openly. That is, in any new project using similar sources, they immediately suspect either a rebranding of REvil, or a new threat, at the origins of which are former REvil members.
When analyzing the Ransom Cartel malware, the researchers found similarities in the malware configuration structure, although the storage locations differ. So, some configuration values are missing in the Ransom Cartel code, and this, according to experts, means that the authors of the malware are either trying to make it more compact, or the old version of the REvil malware is the basis for this ransomware.
The strongest thing about the similarities between the two ransomware is the encryption schemes they use. The Ransom Cartel samples also generate multiple pairs of public and private keys and secrets, almost identical to the complex system used by REvil.
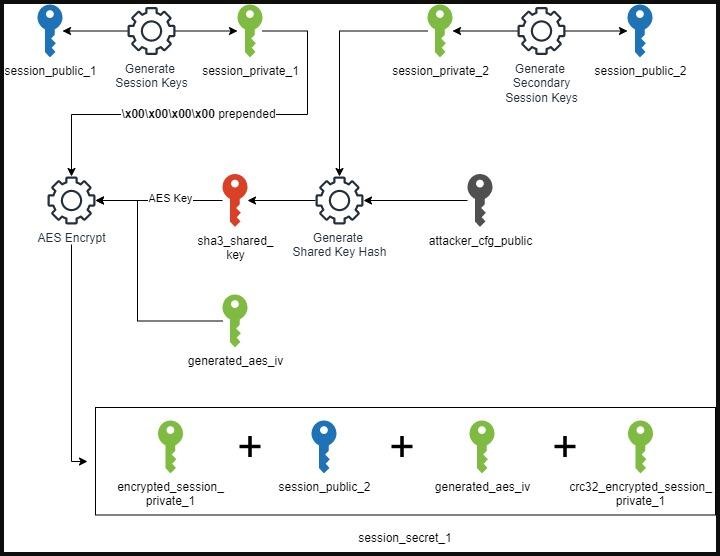
At the same time, the Ransom Cartel samples do not contain such a serious obfuscation that was found in the REvil malware. This may mean that the authors of the new ransomware do not have access to the original REvil obfuscation mechanism.
Another difference is that Ransom Cartel uses Windows Data Protection API (DPAPI) for stealing credentials. For this purpose, the group uses the very rare DonPAPI tool, which is able to search hosts for DPAPI blobs containing Wi-Fi keys, RDP passwords, and credentials stored in browsers, and then download and decrypt them locally on the machine. These credentials are then used to compromise the Linux ESXi servers and authenticate against the vCenter web interfaces.
Interestingly, despite the lack of leaks of REvil source codes, the Ransom Cartel is not the only group that uses REvil developments in their attacks. So, in April 2022, when the REvil Tor sites unexpectedly resumed their work, a new BlogXX encryptor was discovered, not only compiled based on the REvil source code, but also containing a number of changes.
Then information security experts wrote that the authors of BlogXX clearly have the REvil source code. In addition, when REvil’s Tor sites were up and running again, visitors were soon redirected to the BlogXX site. Although this resource was different from the previous REvil sites, the fact that the old sites started redirecting visitors to the BlogXX sites suggested that someone in the new hack group had access to Tor private keys that allowed them to make the necessary changes.




