Experts from the Leiden Institute for Advanced Computer Science have discovered thousands of GitHub repositories with fake PoC exploits for various vulnerabilities that spread malware.
It turned out that the probability of infection with malware when downloading PoC can reach 10.3%, even if outright fakes are excluded.
Let me remind you that we also reported that GitHub removed ProxyLogon exploit and has been criticized, and also that Hackers Use CircleCI Fake Notifications to Access GitHub Accounts.
Experts write that GitHub is one of the largest platforms for hosting code, and researchers from all over the world use it to publish PoC exploits so that other members of the information security community can test patches, determine the impact and scale of bugs.
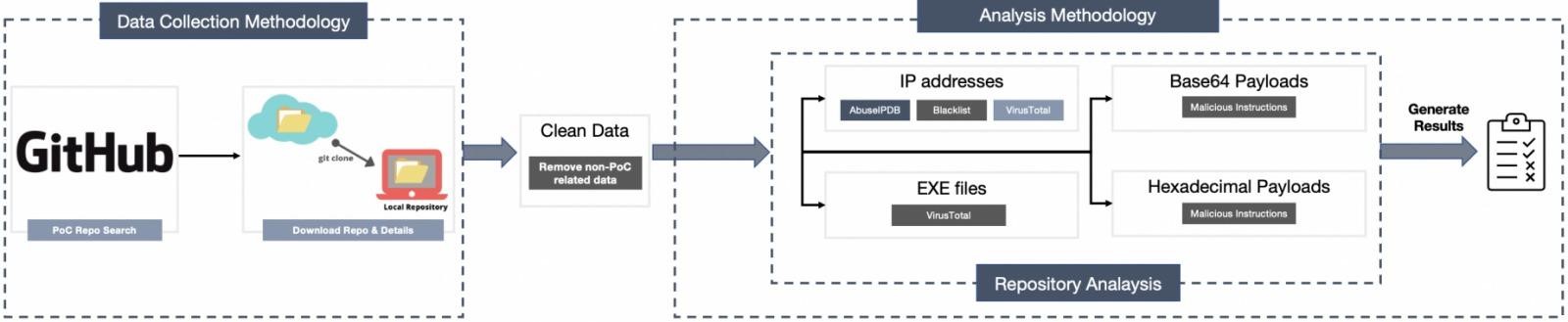
For their study, the experts analyzed more than 47,300 repositories offering exploits for various vulnerabilities discovered between 2017 and 2021. The following methods were used for the analysis.
- Analysis of IP addresses. Comparison of the IP address of the PoC author with public blacklists, as well as Virus Total and AbuseIPDB.
- Binary analysis. Checking provided executable files and their hashes via VirusTotal.
- Hexadecimal and Base64 parsing. Converting obfuscated files before performing binary and IP checks.
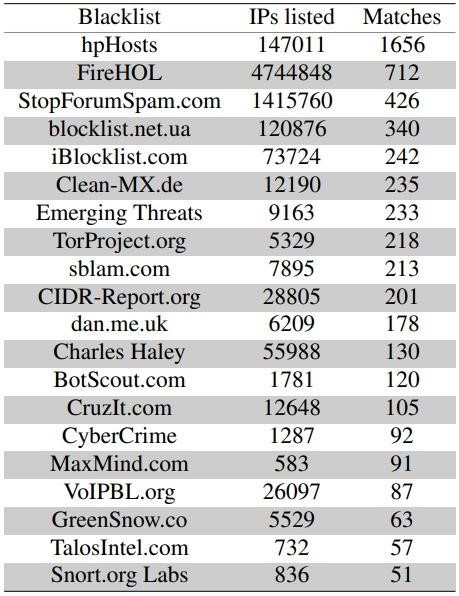
As a result, out of 150,734 unique IP addresses, 2864 were blacklisted (1522 were identified as malicious by Virus Total, and another 1069 were present in the AbuseIPDB database).
During binary analysis, a set of 6160 executable files was examined, and 2164 malicious samples were found among them, located in 1398 repositories.
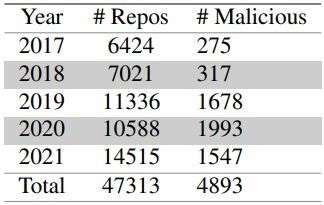
In total, 4,893 out of 47,313 repositories tested were found to be malicious in this review, with most of the dangerous PoCs found to be associated with 2020 vulnerabilities.
After examining some of these bogus exploits, the researchers found many different malware and malicious scripts, ranging from remote access Trojans to Cobalt Strike.
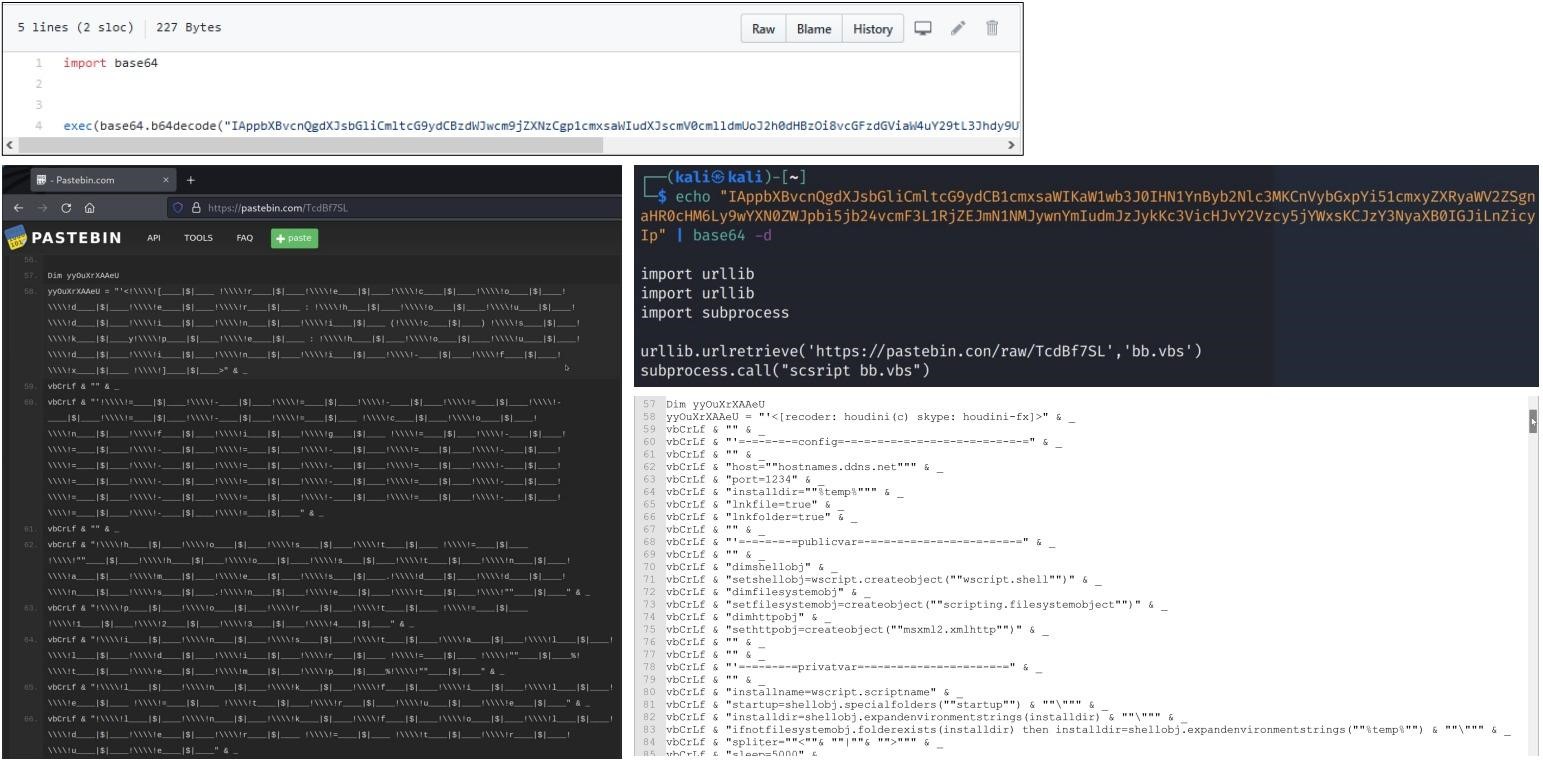
For example, in one example, the fake PoC for CVE-2019-0708, commonly known as BlueKeep, contained an obfuscated base64 Python script that extracted VBScript from Pastebin. This script was Houdini RAT, an old JavaScript Trojan that supports remote command execution through the Windows command line.
In another case, researchers discovered a fake exploit that was an infostealer that collects system information, IP address, and user agent from an infected system. Since this PoC was previously created as an experiment by another researcher, the experts considered that its discovery was confirmation that their approach was working.
Experts concluded that you should not blindly trust GitHub repositories, because the content is not moderated here. According to the authors of the report, all testers should take the following steps before working with exploits:
- carefully read the code that you plan to run on your network or the client’s network;
- if the code is seriously obfuscated and takes too long to analyze manually, you should place it in an isolated environment (for example, a virtual machine) and check the network for suspicious traffic;
- use open-source analysis tools like VirusTotal to check binary files.
The researchers write that they have notified GitHub of all malicious repositories, but it will take some time to check and remove them, so for now, many of them are still available to everyone.




