GitHub warns that a large-scale phishing campaign aimed at users began on September 16: scammers send emails with fake notifications on behalf of the Circle CI service, which is used for continuous development and deployment.
Let me remind you that we also said that GitHub will replace the term “master” with a more neutral one, and also that GitHub Developers Review Exploit Posting Policy Due to Scandal.
These fake messages inform recipients of changes to the privacy policy and terms of use, which ostensibly requires people to sign into their GitHub account and accept the changes.
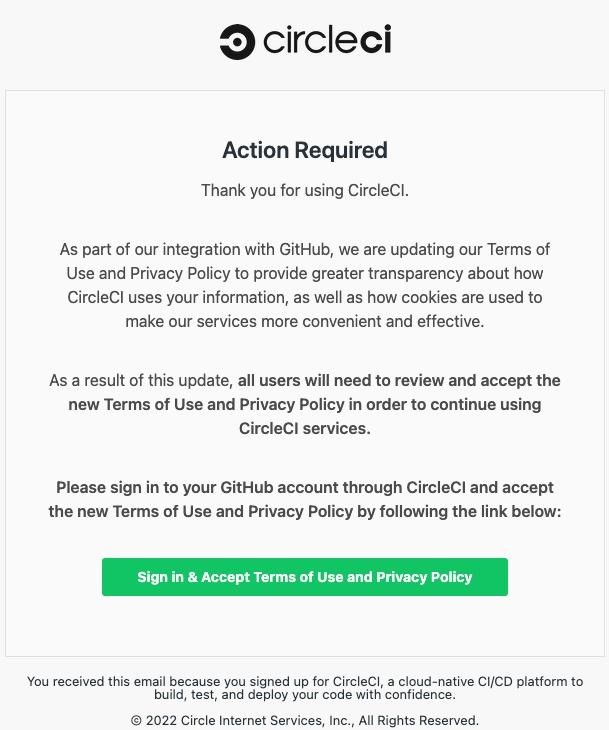
As you might guess, the goal of attackers is to steal credentials from GitHub and two-factor authentication codes that are transmitted to attackers through reverse proxies. Once credentials are obtained, attackers have been known to create personal access tokens (PATs), authorize OAuth applications, and sometimes add SSH keys to retain access to accounts even after password resets.
CircleCI representatives also warned users about fakes and tried to draw attention to this malicious campaign. CircleCI emphasizes that the service would never ask users to enter credentials to view changes to the privacy policy and terms of use.
The phishing domains used by the attackers are trying to mimic the real CircleCI domain (circleci.com). The following counterfeits have been confirmed so far:
- circle-ci[.]com
- emails-circleci[.]com
- circle-cl[.]com
- email-circleci[.]com
GitHub reports that there are data leaks from private repositories immediately after breaches, with attackers using VPNs and proxies to make it harder to trace. If the compromised account has high privileges, the hackers create new accounts in order to retain access to the target in the future.
It is reported that GitHub specialists have now suspended accounts for which suspicious activity has been identified. Affected users’ passwords have been reset and they should be notified of the incident.


![Signs of Identity Theft: How to Prevent It? 3 Signs of Identity Theft: How to Prevent Identity Theft [Short Guide 2022 ]](https://gridinsoft.com/blogs/wp-content/uploads/2022/09/istockphoto-1279316333-612x612-1-150x150.jpg)

