ESET experts have discovered the FatalRAT malware, which targets Chinese-speaking users: the threat is distributed through fake websites of popular applications and advertised through Google Ads.
Let me remind you that we also wrote about Attackers Can Use GitHub Codespaces to Host and Deliver Malware, and you may also be interested in our article: Dangerous Virus & Malware Threats in 2023.
The researchers say that FatalRAT has been active since at least the summer of 2021 and is capable of intercepting keystrokes, changing the victim’s screen resolution, downloading and running files, executing arbitrary shell commands, and stealing or deleting data stored in browsers.
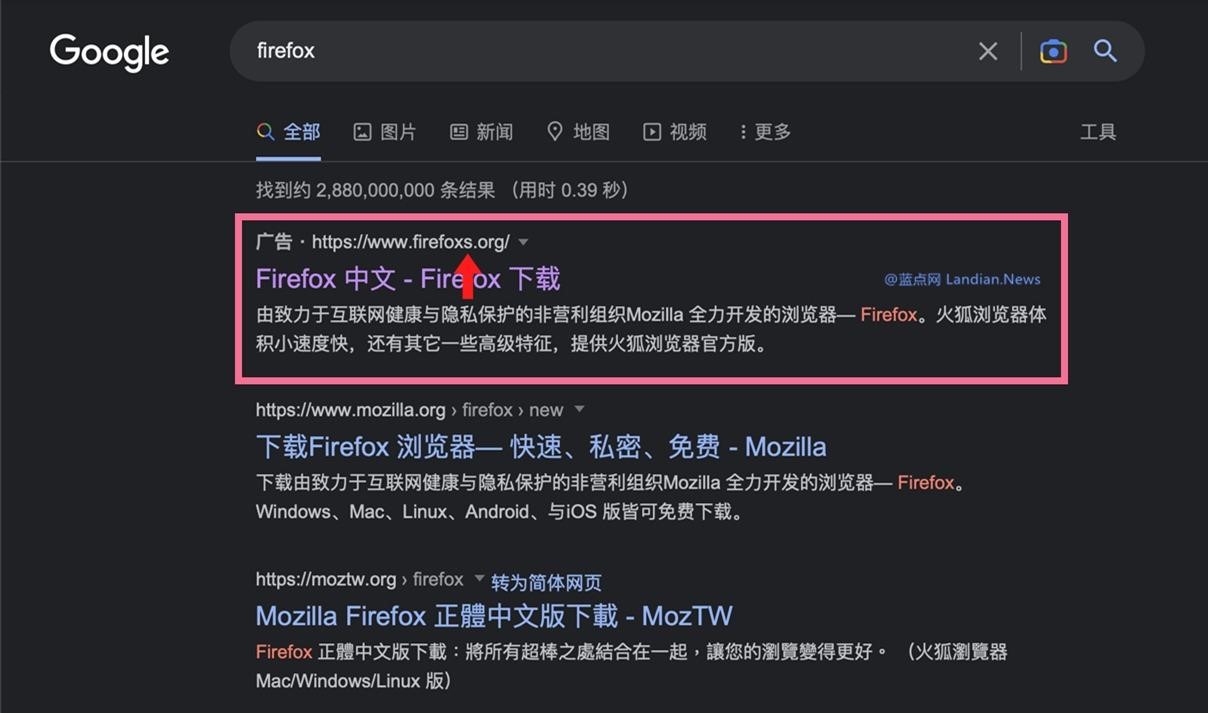
Malware advertising
So far, the malware distribution campaign has not been linked to any known hacker group, and the ultimate goals of the attackers are also unclear. For example, hackers can steal victim information (such as credentials) for sale on darknet forums or for later use in other malicious campaigns.
According to experts, most of the attacks were observed between August 2022 and January 2023 and targeted users in Taiwan, China and Hong Kong.
A small number of infections have also been reported in Malaysia, Japan, Thailand, Singapore, Indonesia, Myanmar and the Philippines.
Basically, hackers distribute their malware through fake websites of popular applications, masquerading as Google Chrome, Mozilla Firefox, Telegram, WhatsApp, LINE, Signal, Skype, Electrum, Sogou Pinyin Method, Youdao and WPS Office. Some sites offer fake versions of applications in Chinese, when in fact these applications are not available at all in China (eg Telegram).
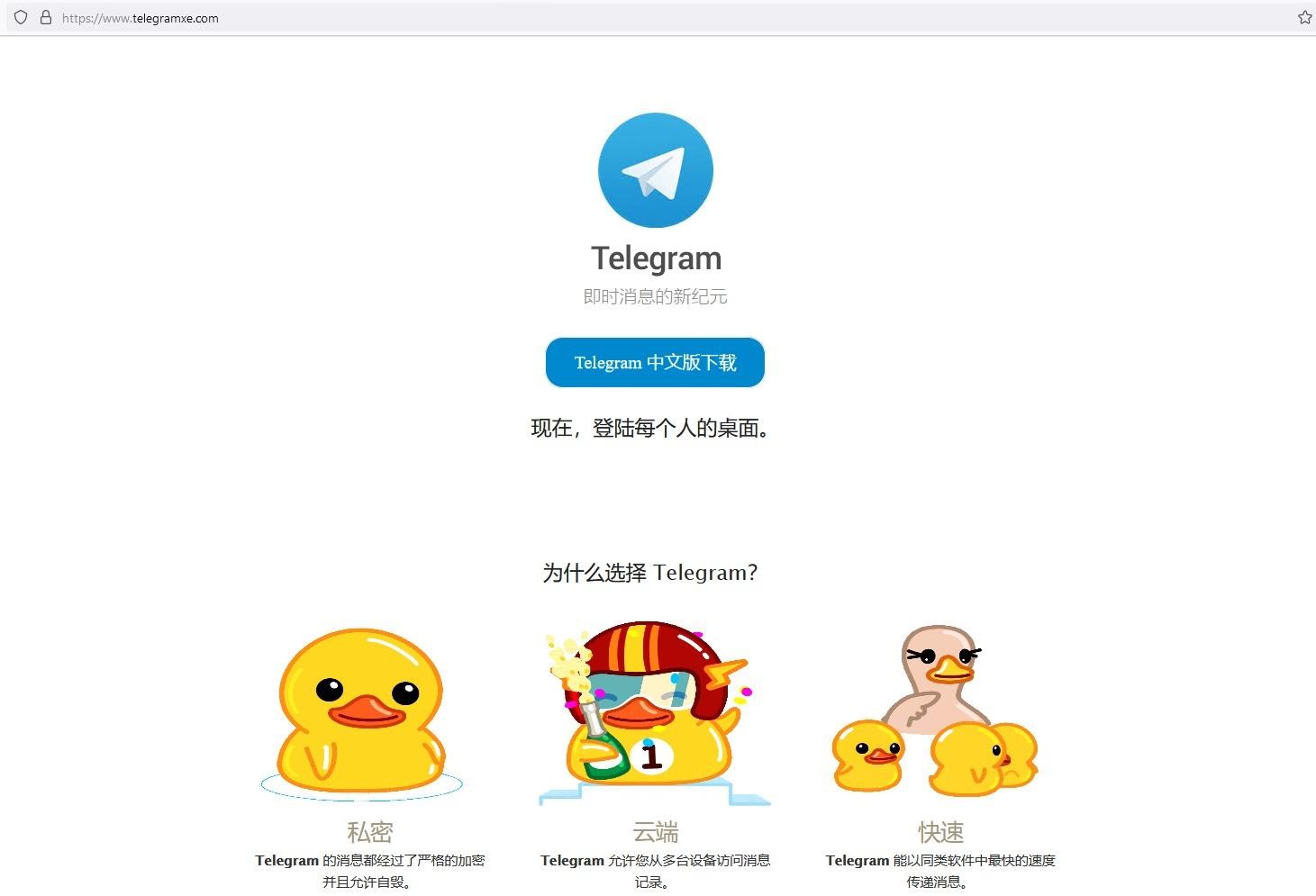
Fake site
To lure users to malicious sites, hackers promote these sites in Google search results through Google Ads, while trying to make fake domain sites look like real ones. These malicious ads have now been removed.
The ESET report notes that Trojanized installers downloaded from fake sites delivered the real application to the victim’s device to avoid detection, as well as the files needed to run FatalRAT. The installers themselves were digitally signed .MSI files created with the Windows installer.
According to the researchers, this campaign was aimed at the widest possible range of users and could affect anyone.
Let me remind you that the media wrote that Google Scammer Pleads Guilty in $123 Million Theft.

