Qihoo 360 (360 Netlab) experts have warned about the emergence of an updated version of the Fodcha botnet, which embeds ransom demands directly into DDoS packets and has new infrastructure hiding functionality.
Let me remind you that the Fodcha botnet was discovered in the spring of this year, and even experts reported that the threat was growing rapidly and replenished with new bots, including routers, DRVs, and vulnerable servers.
Let me remind you that we also wrote that Google Stops Glupteba Botnet and Sues Two Russians, and also that TeamTNT mining botnet was infected over 50,000 systems in three months.
If in April of this year, Fodcha attacked about 100 targets daily, now, according to the researchers, the botnet has grown significantly, and the average number of targets per day has increased to 1000. The updated Fodcha peaked on October 11, 2022, attacking 1396 targets at once per day. Confirmed botnet attacks include:
- DDoS attack on a healthcare organization that lasted from June 7 to 8, 2022;
- DDoS attack on the communications infrastructure of an unnamed company in September 2022;
- A 1TB/s DDoS attack against a well-known cloud service provider on September 21, 2022.
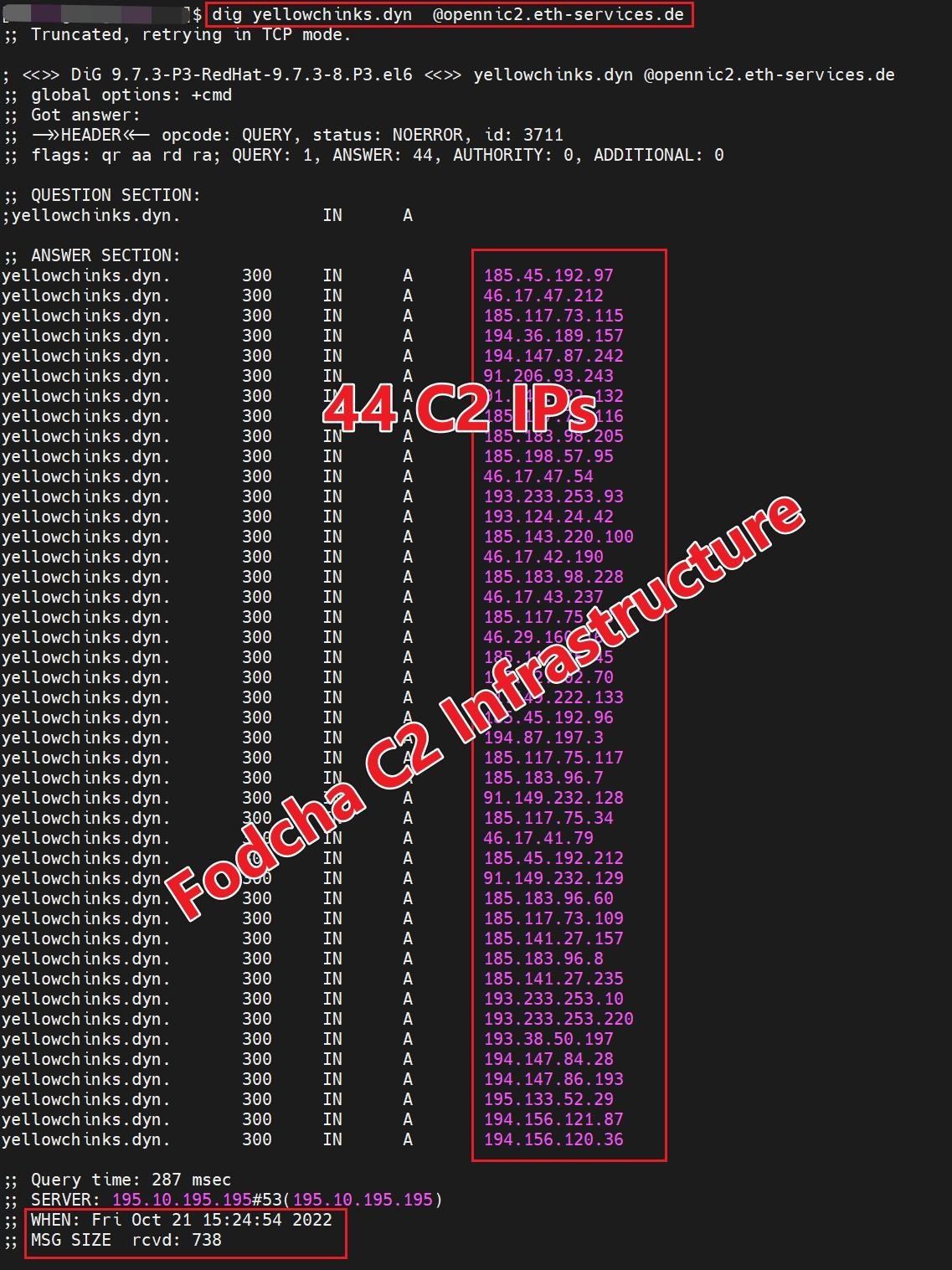
Currently, the botnet uses 42 C&C domains for the daily work of 60,000 active bots, which are capable of generating attacks with a capacity of up to 1 Tb / s.
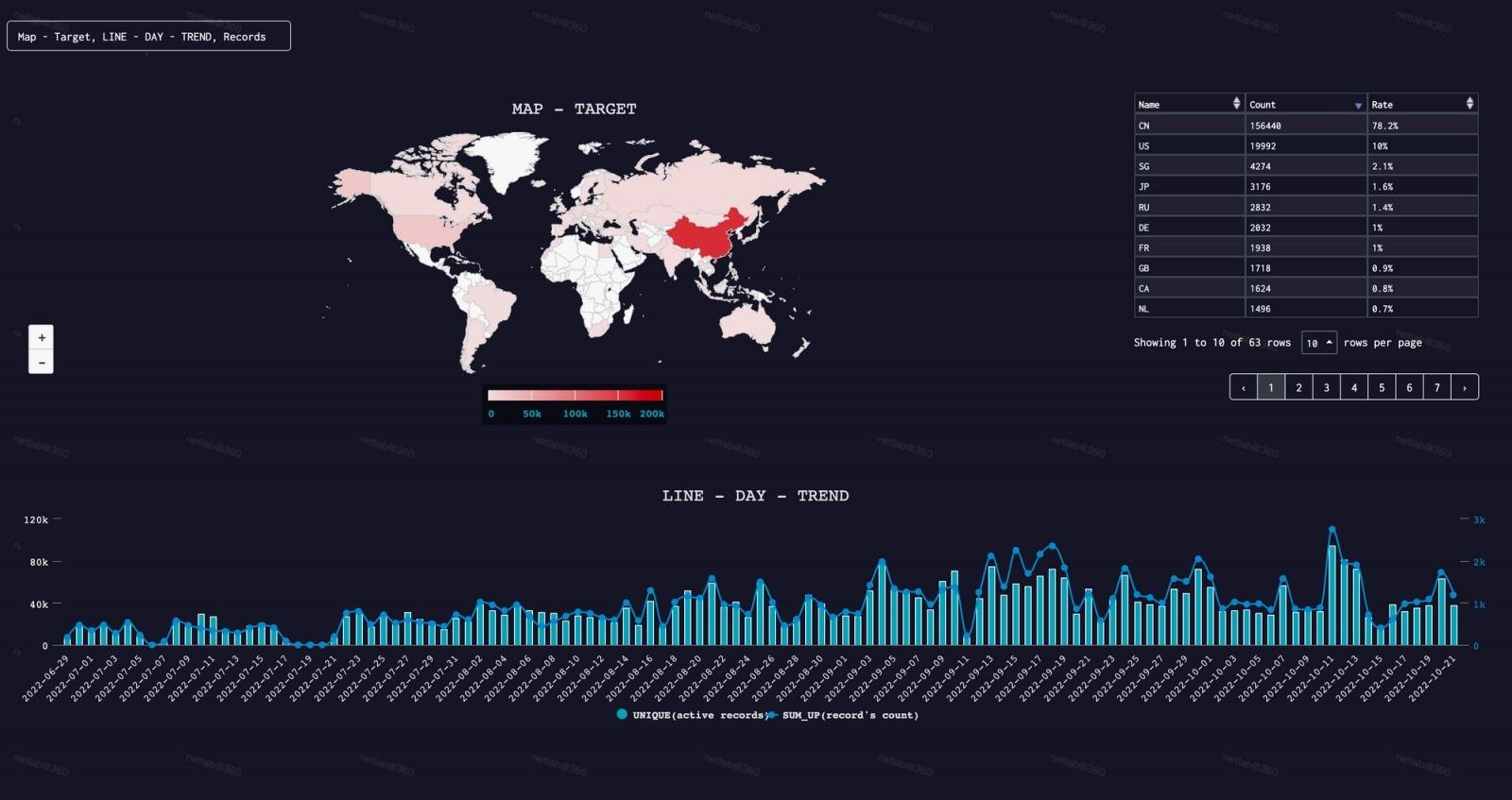
Most of Fodcha’s targets are located in China and the US. Still, the botnet can be safely called international, as it has infected systems in Europe, Australia, Japan, Russia, Brazil, and Canada.
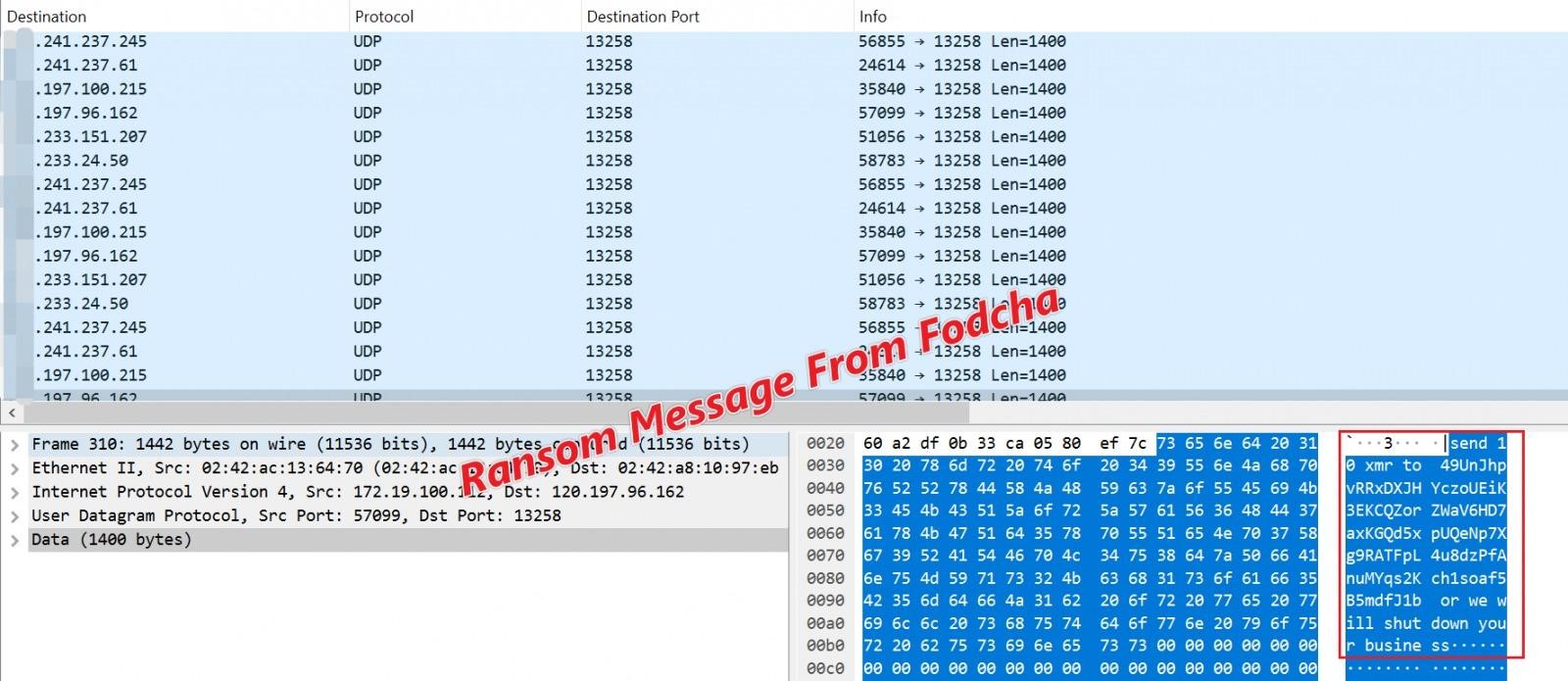
Analysts believe that Fodcha operators make money by renting out their botnets to other attackers who want to carry out DDoS attacks. Moreover, the new version of Fodcha is also engaged in extortion: to stop the attacks, demanding a ransom from the victims in the Monero cryptocurrency.
Fodcha demands a ransom starting from 10 XMR (Monero), about $1,500. Interestingly, the demands are embedded in the botnet’s DDoS packets, where the attackers warn that the attacks will continue until the payment is made.
The researcher’s report also notes that the botnet now uses encryption to communicate with the control server, making it difficult to analyze malware and the potential destruction of its infrastructure by information security specialists.