The Security Blog From Gridinsoft
Progress Flowmon Command Injection Flaw Discovered
Progress Flowmon, a popular network monitoring software solution, appears to be vulnerable to arbitrary command injection. Successful exploitation of the…
XZ Utils Backdoor Discovered, Threating Linux Servers
A backdoor in liblzma library, a part of XZ data compression tool was discovered by Andres Freund. The maintainer of…
UnitedHealth Hack Leaks 6 TB of User Data
UnitedHealth Group, one of the largest providers of health insurance and health care services in the United States, suffered a…
Microsoft SharePoint Vulnerability Exploited, Update Now
In late March 2024, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued the alert regarding the exploitation of a…
PyPI Malware Spreading Outbreak Exploits Typosquatting
PyPI, an index of Python packages, once again became a place for malware spreading. Threat actors registered hundreds of profiles…
Attackers Can Use .Zip and .Mov Domains for Phishing
Experts’ fears that attackers will use new .zip and .mov…
US Authorities Warn of Disaster-Related Scams
Following natural disasters and severe weather, there is a higher…
CAPTCHA in Discord Asks Users to Find Non-Existent Objects Created by AI
Users complain that the Discord CAPTCHA provided by hCaptcha forces…
GitLab Releases Patch to Critical Vulnerability
GitLab, one of the most famous code repositories in the…
GoDaddy Refund Phishing Emails Spread Infostealer
Hackers started using GoDaddy Refund Emails as a disguise to…
Philadelphia Inquirer is Struck by Cuba Ransomware
The Philadelphia Inquirer, Philadelphia’s largest newspaper by circulation and third-longest-running…
FIN7 Hack Group Resumed Activity, Linked to Clop Ransomware
Microsoft analysts report that last month the notorious hacker group…
ChatGPT Causes New Wave of Fleeceware
Artificial intelligence is one of the most significant advances in…
PyPI Malware Storm Forces to Suspend New Uploads
Python Package Index, a software repository for Python developers, recently…
3 Unpopular Malware Spreading Ways in 2023
The modern Internet space is like an endless ocean, where…
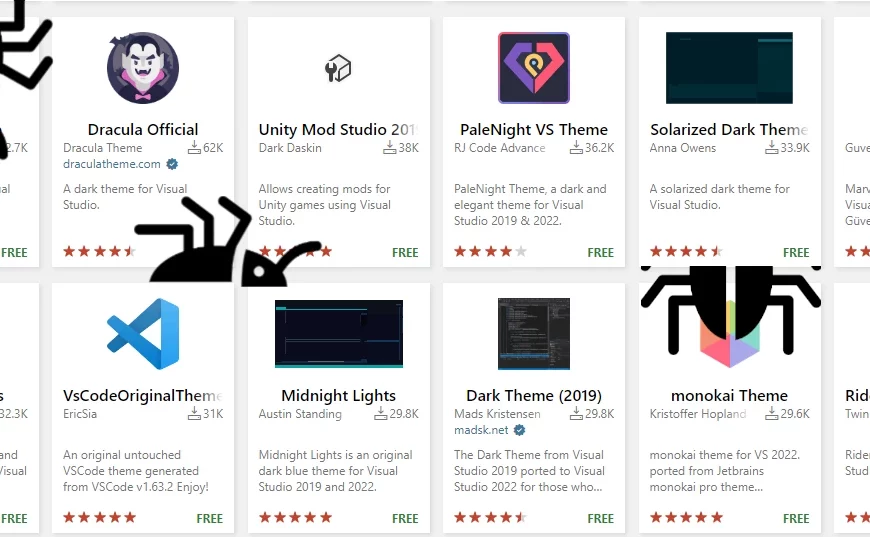
Visual Studio Code Malicious Plugins Steal Personal Data
Some plugins for Visual Studio Code, a popular code editing…
Trend Micro: Millions of Android Devices Contain Malware Right in the Firmware
Trend Micro analysts presented an interesting report at the Black…