With increased remote work, IT teams use remote access tools to manage company devices and ensure smooth operations. Remote desktop connections are highly attractive to hackers, with an average of over 37,000 attempts from multiple IP addresses daily. These attacks are typically automated, but once the hackers gain access credentials, they manually search for critical or sensitive files. One such tool is Remote Desktop Protocol (RDP), a Microsoft protocol that allows administrators to access desktop computers. However, because it gives full control to the user. It can also be a point of vulnerability for potential security threats. This is what caused its extensive usage for target emulation, or in other words, RDP honeypot creation.
What is Remote Desktop Protocol (RDP)?
Remote Desktop Protocol (RDP) – a technical standard that enables remote use of desktop computers. Among the protocols available for remote desktop software, RDP, Independent Computing Architecture (ICA), and virtual network computing (VNC) are the most commonly used. Microsoft initially released RDP, which is compatible with most Windows operating systems. But can also be used with Mac operating systems.
What is a Honeypot?
Honeypot – is a system set up at the endpoint to monitor incoming connections and application activities. It mimics the original endpoint to detect potential malicious activities and enable security systems and experts to take countermeasures. Examples of honeypots include internal servers, network computers, and website servers that can attract cyber criminals.
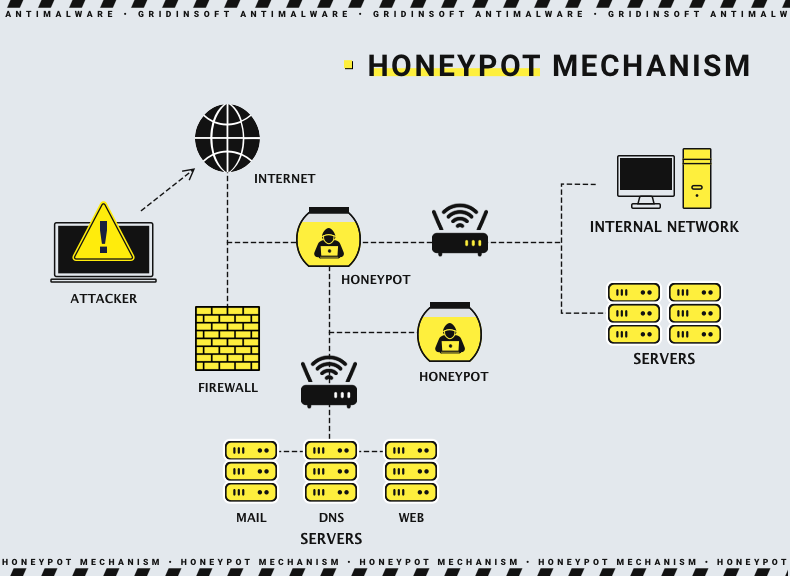
The purpose of a honeypot is to divert and distract attackers away from actual critical systems while providing valuable insights into their behavior, techniques, and motives. Organizations can enhance their security by examining the tactics, techniques, and procedures (TTPs) used by attackers. It helps them recognize potential threats. As you may suppose by the name, RDP honeypot is one that resemples a normal connection through the remote desktop protocol.
Hackers’ Attacks on RDP Honeypot
Through an experiment using high-interaction honeypots with an RDP connection accessible from the public web, GoSecure, a threat hunting and response company with headquarters in the U.S. and Canada, they have discovered that attackers operate within a daily schedule, much like working office hours. Over three months, the researchers recorded nearly 3.5 million login attempts to their RDP honeypot system, highlighting the relentless nature of these attackers.
What do the experts say?
Cybersecurity researchers inform that the honeypots are directly linked to a research program to expose criminals’ strategies that could help prevent them in the future. Between July 1 and September 30, 2022, the honeypot attacked 3,427,611 times from over 1,500 IP addresses. The researchers named the system to entice attackers so criminals would think it was part of the bank’s network.
The attempts to compromise the system were predictable, involving brute-force attacks that relied on multiple dictionaries. The most commonly used username was "Administrator", along with variations such as shortened versions, different languages, or letter cases. In roughly 60,000 instances, the perpetrator conducted preliminary research before attempting to discover the correct login information and tested usernames that did not belong in the given set.
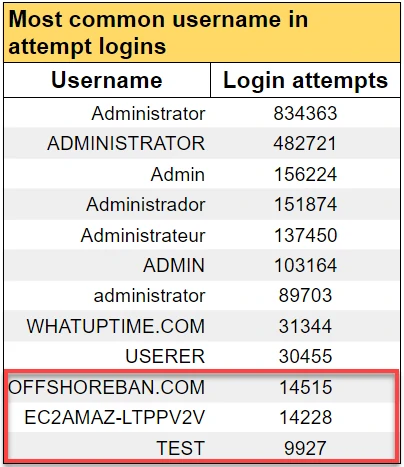
In the image above, researchers found three unique usernames associated with the honeypot system – the names of the RDP certificate, the host, and the hosting provider. These usernames appeared among the top 12 attempted login names, indicating that some hackers were not unthinkingly testing login credentials but were gathering information about the victim beforehand.
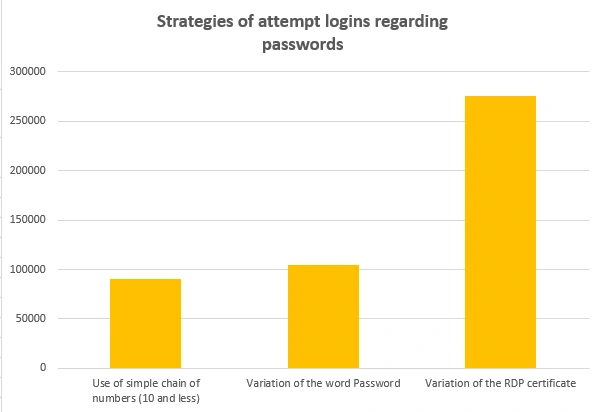
The researchers also discovered that the system had collected password hashes and was able to decrypt weaker ones. Their findings revealed that the most common strategy used by the hackers was to create variations of the RDP certificate, followed by variations of the word "password" and simple strings of up to ten digits.
Interesting RDP Honeypot statistics
It’s worth noting that the RDP certificate name was only used in RDP honeypot attack attempts from IP addresses in China (98%) and Russia (2%). However, this doesn’t necessarily imply that the attackers are from these countries but that they utilize infrastructure in these regions. Another observation is that a significant number of attackers (15%) employed thousands of passwords in combination with just five usernames.
What then?
All this information gives quite a view of what is happening in a modern threat landscape. Despite the numerous other ways to infect the system, hackers still prefer RDP. The technology is easy to exploit, so even unskilled attackers will perform the attack fine. Brute force utilities and the databases with credentials are easily accessible. And such popularity is a straightforward reason to ensure your RDP connections are safe.
There are several ways to mitigate known RDP vulnerabilities, and the easiest among them is to close the vulnerable port of this networking protocol. Though there could be more convenient and flexible solutions – consider reading our research on securing RDP protocol.




