Movidown is an Unwanted Application that initially mimics a utility for controlling fan speed. However, beneath this shell, it has the capabilities of a dropper malware, which it right away uses to deploy browser hijackers. This functionality, together with the deep access to the system, creates potential risks for much more severe malware to get into the system.
Movidown Overview
Movidown is a potentially unwanted program (PUA) that markets itself as a utility for controlling fan speeds. But when something gets 54/74 detections on VirusTotal, you know there’s more to the story. In reality, this utility has a darker side – it primarily functions as a loader for browser hijackers and adware. Movidown typically gets into the computer without the user’s explicit consent, often through deceptive methods like installers with hidden add-ons, misleading ads, or links on dubious websites.
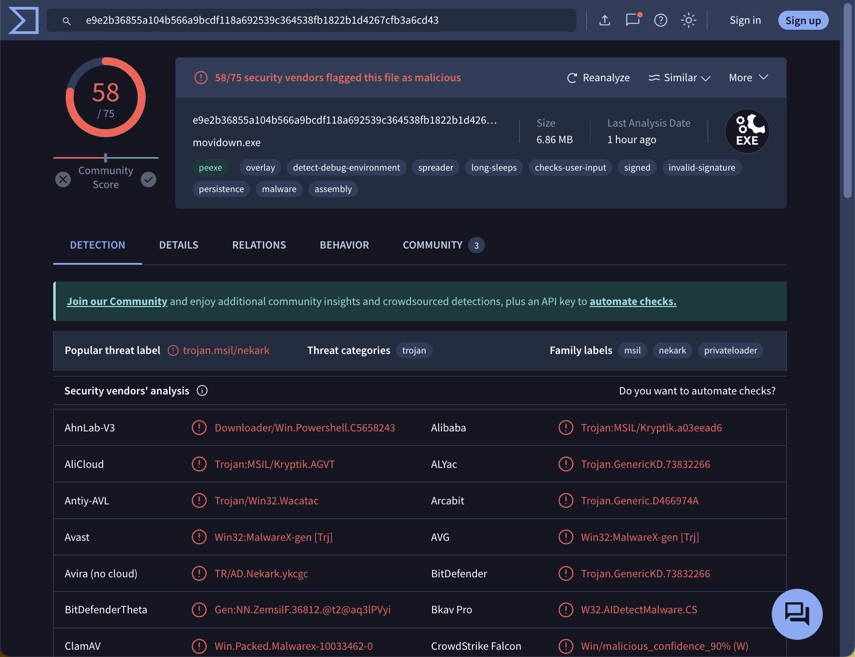
Once installed, Movidown does more than adjust fan speeds as advertised. It collects basic system information (fingerprinting) and alters browser settings. While it isn’t a virus in the traditional sense, it may and will disrupt the browsing experience and create phishing risks. Among other things, it can lead to frequent redirects to dangerous or malicious sites, and even phishing pages. They, in turn, may attempt to steal personal information or trick the user into downloading actual malware.
Technical Analysis
Let’s have a closer look on how Movidown behaves on a compromised system to better understand its nature. As mentioned earlier, it is a utility for controlling fan speeds, so some of its actions within the system might seem logical. For instance, the first thing it does after launching is check the system’s hardware for signs of a virtual environment. Malicious programs often do this check, though it is also normal for hardware management utilities. Movidown checks the following system locations:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Time Zones\Pacific Standard Time
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System\GpSvcDebugLevel
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\ProgramFilesDir
This isn’t an exhaustive list, but such checks can serve both legitimate and malicious purposes. The utility’s need for low-level access to hardware justifies these actions. Though further checks are more concerning, as the utility checks Microsoft Defender settings.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\
C:\Program Files (x86)\Windows Defender\MpClient.dll
C:\Program Files (x86)\Windows Defender\MpOAV.dll
C:\Program Files (x86)\Windows Defender\MsMpLics.dll
Payload Delivery
Unlike a typical dropper malware, this unwanted app follows a slightly different scenario. Normally, a dropper connects to a command server, fetches the current configuration, and then downloads the payload. Movidown virus, in turn, does so immediately upon activation. It appears to have a configuration file embedded into the structure, so all the malicious actions happen without additional steps. It loads a couple of randomly-named files to different folders, including C:\ProgramData – a directory that is hidden by default.
C:\ProgramData\jewkkwnf\jewkkwnf.exe
%SAMPLEPATH%\66b9e7f54cf7b_pro.exe
In this case, ExtreamFanV6.exe is the utility itself, while jewkkwnf.exe is the unwanted software, which functions as a browser hijacker with adware components. Although it’s not fully-fledged malware, technically, Movidown can deliver any type of malicious software.
Establishing Persistence
The next step involves the unwanted software establishing persistence for itself and the payload it have downloaded. For that purpose, it adds itself to the startup processes using Task Scheduler. It also places copies of its files to several directories across the disk.
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\ExtreamFanV6
schtasks /create /f /RU "
schtasks /create /f /RU "
C:\Users\user\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\PowerExpertNNT.lnk
The first registry key adds the utility to startup, while the second and third tasks ensure the payload is activated every time the system starts and every hour, with the highest privileges. It’s important to note that while the utility is capable of reading keyboard input, this functionality isn’t inherently malicious — it’s necessary for the operation of “hotkeys”.
C2 Connection
During execution, Movidown communicates with several command servers and tries to get what appears to be certificates. While being a legitimate purpose, this may also be the way to provide deployed malware with a certificate, so it will stay under the radar of security software.
TCP 204.79.197.203:443
TCP 77.105.164.24:50505
TCP 23.59.198.43:443
GET http://crt.sectigo.com/SectigoPublicCodeSigningCAR36.crt 200
GET http://crt.sectigo.com/SectigoPublicCodeSigningRootR46.p7c 200
It’s also worth noting that this unwanted app contacts a server at 77.105.164.24, which is based in Russia. Software itself and any information about it on the Web says nothing about it, so it is worth keeping in mind.
How to Remove Movidown
Removing the Movidown utility itself is straightforward—you can uninstall it using the standard Windows “Installed apps” menu. However, the unwanted software it installs alongside itself can be more challenging to remove. I recommend using GridinSoft Anti-Malware, as this solution will allow you to remove Movidown in just a few clicks. It will also provide long-term protection against any kind of malicious software, and also from network threats. ВеTo remove this unwanted software, follow the instructions below:

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.