On July 11, 2023, Microsoft published an article about addressing the CVE-2023-36884 vulnerability. This breach allowed for remote code execution in Office and Windows HTML. Microsoft has acknowledged a targeted attack that exploits a vulnerability using specifically designed Microsoft Office documents. The attacker can gain control of a victim’s computer by creating a malicious Office document, but the victim must participate by opening it.
Microsoft discovered a phishing campaign conducted by a Threat Actor named Storm-0978. The targets were government and defense entities in Europe and North America. The Threat Actor used lures related to the Ukraine World Congress and exploited the vulnerability known as CVE-2023-36884.
Who is Storm-0978?
The cybercriminal group known as Storm-0978, based in Russia, is infamous for engaging in various illegal activities. These activities include conducting ransomware and extortion operations, targeted campaigns to collect credentials, developing and distributing the RomCom backdoor, and deploying the Underground Ransomware.
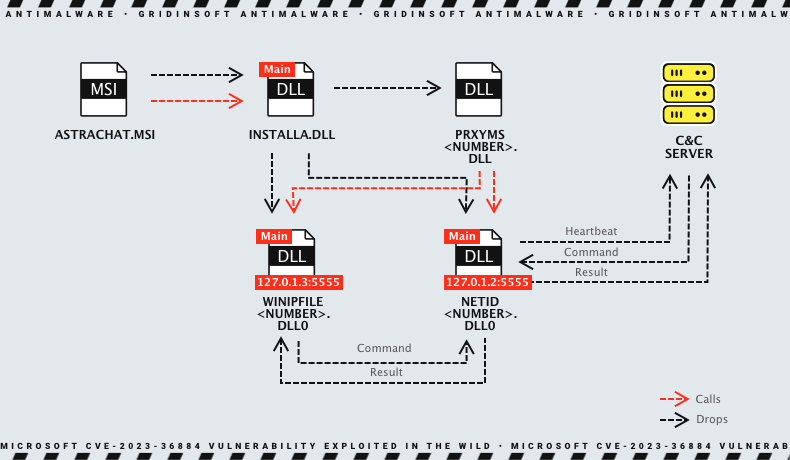
Underground ransomware is associated with Industrial Spy Ransomware, detected in the wild in May 2022. Microsoft identified a recent campaign in June 2023 that exploited CVE-2023-36884 to distribute a RomCom-like backdoor. This was done by a group known as Storm-0978, who use a phishing site masquerading as legitimate software to infect users. The impersonated products include Adobe products, SolarWinds Network Performance Monitor, SolarWinds Orion, Advanced IP Scanner, KeePass, and Signal. Users unwittingly download and execute files that result in the infection of the RomCom backdoor by visiting these phishing sites.
CVE-2023-36884 Exploitation
Storm-0978 conducted a phishing campaign in June 2023, using a fake OneDrive loader to deliver a backdoor similar to RomCom. The phishing emails targeted defense and government entities in Europe and North America, with lures related to the Ukrainian World Congress, and led to exploitation via CVE-2023-36884 vulnerability.
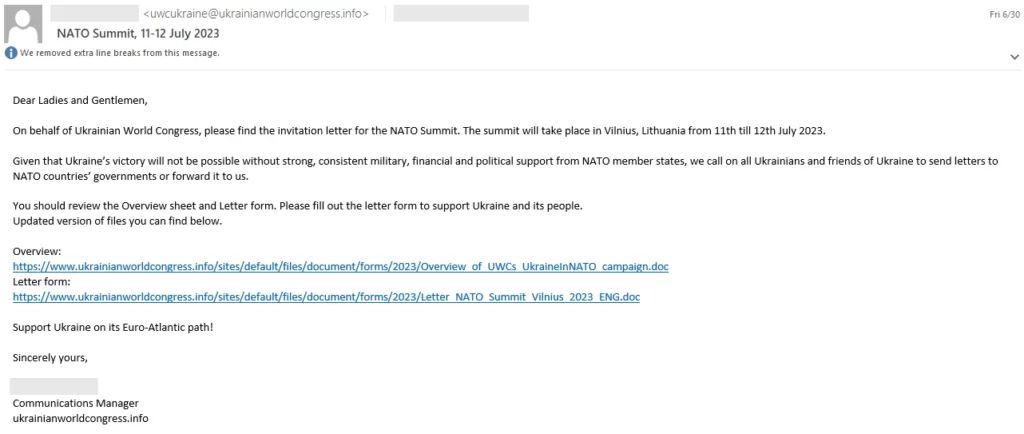
During a phishing attempt, Microsoft detected that Storm-0978 used an exploit to target CVE-2023-36884.
BlackBerry documented the attacks on guests for the upcoming NATO Summit on July 8, but the use of the zero-day in the attacks was unknown at the time.
The attackers used the RomCom variant for espionage, and Underground Ransomware was deployed for ransomware operations. The campaign indicates that Storm-0978 is a highly sophisticated group that seems to be also targeting multiple organizations in the future.
How do you avoid vulnerability?
Organizations should adopt all possible mitigation strategies until a patch is released. The vulnerability has been used in targeted attacks, and news of its existence will doubtlessly lead other attackers to attempt to replicate the exploit.
Microsoft offers performing the registry trick in order to prevent exploitation. In Regedit, go by the following path and find there FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION key.
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Internet Explorer\Main\FeatureControl\
There, create REG_DWORD values with data 1 with the names of exploitable applications:
- Excel.exe
- Graph.exe
- MSAccess.exe
- MSPub.exe
- Powerpnt.exe
- Visio.exe
- WinProj.exe
- WinWord.exe
- Wordpad.exe
Though, patching the breach in such a way is not always enough. Hackers know about the offered fix and can find a way to revert it or exploit the breach by circumventing any registry blocks. For that reason, I also recommend having proactive and reactive security measures.
- Activate cloud-delivered protection in your antivirus software to defend against constantly changing attacker methods. Cloud-based machine learning can detect and block most new and unknown threats.
- Back up your data and store those backups offline or on a separate network for added protection. Backups are the ransomware attacks’ kryptonite, as they can do nothing if you just recover everything back.
- Wherever possible and practical, enable automatic software updates on all connected devices, including your computer and mobile phone.
- To stay safe online, it’s crucial to always verify the authenticity of links and email attachments before opening them, especially if they’re from an untrusted source.
- Use CDR solutions. CDR, or Content Disarm and Reconstruction, is the name of a content management system that aims particularly at document security. It removes active content from the document, making it impossible to exploit.
Patch CVE-2023-36884
Microsoft still needs to release a patch for CVE-2023-36884. This section will be updated as more information becomes available. However, even after a patch is found, it pays to be cautious, watch your every move on the Internet, and always follow the Zero Trust rule.




