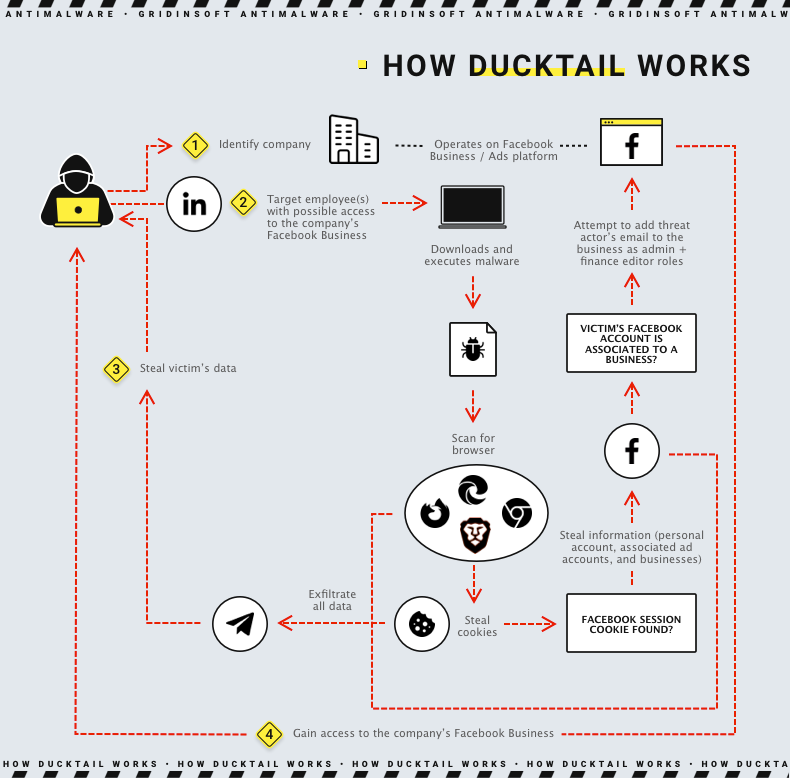
Researchers discovered Ducktail Malware, which targets individuals and organizations on the Facebook Business/Ads platform. The malware steals browser cookies and uses authenticated Facebook sessions to access the victim’s account. As a result, the scammers gain access to Facebook Business through the victim’s account, which has sufficient access to do so. It is a particularly interesting behavior, as most stealer malware aims at cryptocurrency-related data, or even all data types at once.
What is Ducktail Malware?
Ducktail is malware built on .NET Core that predominantly targets individuals and employees who may have access to a Facebook Business account. The Ducktail campaign is believed to have been active since 2018. However, the author became actively involved in developing and distributing malware related to the DUCKTAIL operation in the second half of 2021. The chain of evidence suggests that the attacker’s motives are driven by financial considerations and that the cybercriminal behind the campaign hails from Vietnam.
As mentioned at the outset, the primary targets of this stealer were individuals who hold senior positions in clothing, footwear, and cosmetics companies, as well as employees involved in digital marketing, digital media, and human resources. However, the author is believed to have recently updated the malware, expanding its capabilities. The new version of Ducktail is written in PHP. Now it targets users with any level of access to Facebook Business accounts.
How does it work?
The Ducktail malware is specifically designed to extract browser cookies and use social media sessions. In this way, the attacker obtains sensitive information from the victim’s social media accounts and over Social Media Business accounts respectively. The scammers then use the access to place advertisements for financial gain. We will now look at this process in more detail.
Delivery
To infect a target device, attackers use time-tested social engineering. I have repeatedly mentioned that the weakest link in any defense is the human factor, so this tactic will always be relevant. First, scammers place a malicious file on popular cloud storage. They typically use Google Drive, OneDrive, Mega, MediaFire, Discord, Trello, iCloud, and Dropbox. Next, they trick the victim into downloading and opening the malicious file. To do this, hackers contact the victim via social networks, and send a link to the archive. To make it look more legitimate, they pick a name like “Project Information And Salary Details At AVALON ORGANICS.zip”. Consequently, no suspicion is raised by the victim.
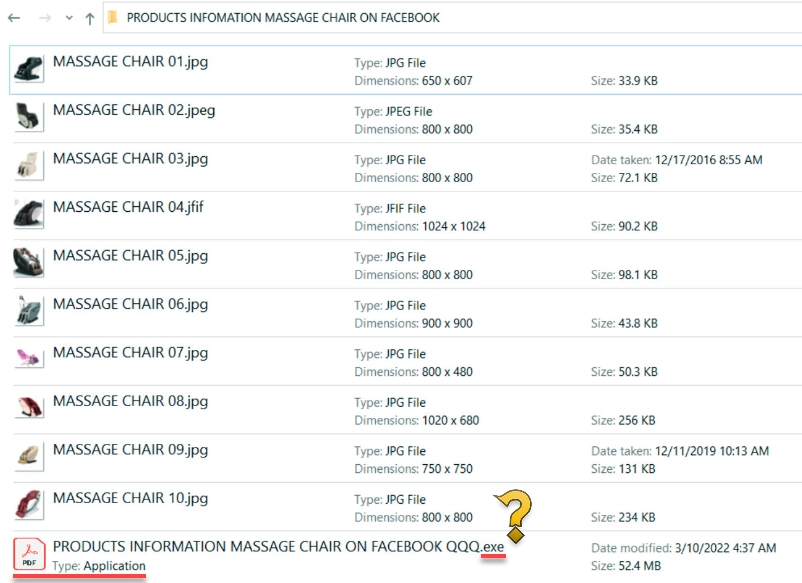
Inside the archive, there may be some thematic images (e.g., images of cosmetics, if it is a cosmetics company) and PDF or PDF document files. In reality, however, these are executable files disguised as documents, as can be seen by checking the file extension. These files are actual payloads – .NET assemblies that carry both executable sections and DLLs in it.
Info Stealing
Once launched, Ducktail scans web browsers, mainly Google Chrome, Mozilla Firefox, Microsoft Edge, and Brave Browser. The malware extracts all stored cookies as well as access tokens. It is also interested in information such as name, user ID, email address, and date of birth from the victim’s Facebook account. The malware scans registry data in HKLM\SOFTWARE\WOW6432Node\Clients\StartMenuInternet to get each installed browser’s name, path, and icon path.
Hacking process
Ducktail uses the victim’s social media session cookie and other security credentials obtained. This allows it to interact directly with other social media endpoints from the victim’s computer, extracting information from the victim’s social media account. In addition, the malware checks for two-factor authentication and, if positive, tries to obtain recovery codes. It can also steal access tokens, IP addresses, and user agents, data from commercial and advertising accounts connected to the victim’s personal account. This allows attackers to hijack these accounts and add their email addresses to gain admin and financial editor access.
While the former is self-explanatory, administrator rights give complete control over the Facebook Business account. Financial editor rights allow the change of credit card information and financial details of the business, such as transactions, bills, account charges, and payment methods. Because Ducktail accesses this information by sending requests from the victim’s computer, he impersonates a legitimate user and his session. This is achieved by masking its activity behind the victim’s IP address, cookie values, and system configuration. In addition to the data obtained, the malware attempts to get data from the Facebook Business page the following information:
- Payment initiated
- Payment required
- Verification Status
- Owner ad accounts
- Amount spent
- Currency details
- Account status
- Ads Payment cycle
- Funding source
- Payment method [ credit card, debit card, etc.]
- Paypal Payment method [email address]
- Owned pages.
Exfiltration
As C&C server, Ducktail uses Telegram messenger as a channel. Fraudsters use Telegram.Bot client library makes it easy to upload a file to a chat with a Telegram bot. Finally, the malware runs an infinite loop in the background, establishing a continuous exfiltration process.
How to protect yourself?
Ducktail is a narrowly targeted information thief that can have severe financial losses and identity theft. Its authors constantly make changes and improve delivery mechanisms and approaches to steal sensitive user information. However, the following tips can help you keep the chances of infection to a minimum:
- Only download applications from trusted sources. Please avoid URLs that may be used to spread malware, like Torrent or Warez.
- Use strong passwords and remember to update them regularly.
- Enable multi-factor authentication whenever possible.
- Use reliable antivirus and internet security software on all your devices, such as your PC, laptop, and workplace PC.
- Avoid opening links and email attachments unless you can verify their authenticity.
- Keep an eye on the network beacon to prevent data exfiltration by malware or TAs.
- Consider enabling Data Loss Prevention (DLP) solutions on your employees’ systems.
Ducktail IoCs
MD5:691ca596a4bc5f3e77494239fb614093
MD5:618072b66529c1a3d8826b2185048790
MD5:b4125e56a96e71086467f0938dd6a606
SHA1:20f53032749037caa91d4b15030c2f763e66c14e
SHA1:936139fc7f302e3895f6aea0052864a6cb130c59
SHA1:e692a626c6236332bd659abbd4b1479b860bf84a
SHA256:f024e7b619d3d6e5759e9375ad50798eb64d1d4601f22027f51289d32f6dc0ca
SHA256:2650e6160606af57bd0598c393042f60c65e453f91cde5ecc3d0040a4d91214d
SHA256:385600d3fa3b108249273ca5fe77ca4872dee7d26ce8b46fe955047f164888e7




You have a great way of breaking things down. Keep it up!