Web browsers are invaluable tools for users and make up a huge portion of the daily time we spend in the digital world. Unfortunately, they hold many personal files and information, making them a desirable target for cybercriminals. Threat actors could attempt to access a person’s computer or other computers in the network using attacks within the web browsers. This article will tell you about what threats you can face on the Internet and how to browse the Web securely under different circumstances.
Top browser threats
There are different threats with different purposes. Some are explicitly aimed at the browser, others at something else. Here is a list of common threats:
The exploitation of vulnerabilities in any extensions, plugins, and browsers you install. Crooks often use this tactic to obtain confidential data or to distribute additional malware. These threats are presented under the guise of phishing emails or visits to sites that a hacker controls. Another tactic may be the XSS attack, which sometimes belongs not only to the websites’ flaws, but also on browser vulnerabilities.
Malicious plugins: People use plugins to improve the convenience of Internet browsing. These plugins have privileged access to the browser. Thus, malicious plugins under the guise of legitimate ones can be distributed to download additional malware or to steal user data. Some of them act as a coin miner trojans – malware that exploits the hardware of the computer to mine cryptocurrencies.
DNS poisoning: DNS is a computer system that retrieves information about domains that it converts into IP addresses so that browsers display the site users want to visit. But attacks on DNS kb records on DNS servers may allow hackers to redirect the browser to malicious domains like phishing sites.
Session hijacking: If attackers can steal session IDs (when they are not encrypted), they could log into the same websites and apps that the user did, pretending to be the user. They could then steal sensitive information and even financial details. Websites and app servers give out session IDs when users log in.
Man-in-the-middle/browser attack: Intruders can send a user to a phishing site via a page with a request for authorization in the web browser. If hackers control the router through which the victim is connected to the network, it will be much easier to do so.
Web app exploitation: Malicious code can attack apps on your computer rather than the browser, but the browser is used to run the code. Such attack is also actual for the apps that use the browser tab rendering inside of the app window to display the user interface.
How to browse the Web securely?

Seeing the list of threats you can see above, you may start thinking that it is impossible to browse the Web securely. To reduce the risks of confidential data loss and malicious content distribution, users can take the following steps:
1. Don’t share your personal information
The first thing to note about network security is preserving your data from third parties. Users should understand with who they are sharing their bank details, passwords, insurance numbers, and more. The theft of confidential data is not the primary purpose of fraudsters, but if you get it, intruders can compromise you or sell this information to third parties. In either case, users risk losing the integrity of their privacy.
2. Keep your browser and plugins updated
Remove all old plugins to reduce the risk of exploiting vulnerabilities. All browser and plugin updates are designed to increase the level of protection against new system intrusion methods.
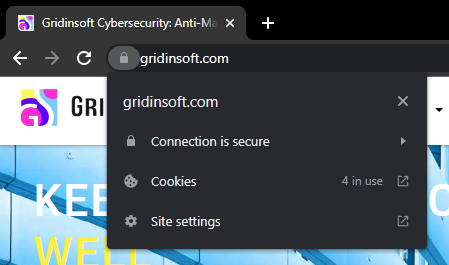
3. Only visit HTTPS sites
Pay attention to the top of your web browser whenever you visit a website. His address bar should read “HTTPS”. Also, note the lock symbol at the beginning of the browser address bar; it shows that the connection is protected. In the dialogue window that appears after clicking on that lock, you’ll see the information about the certificate issuer and date of expiration.
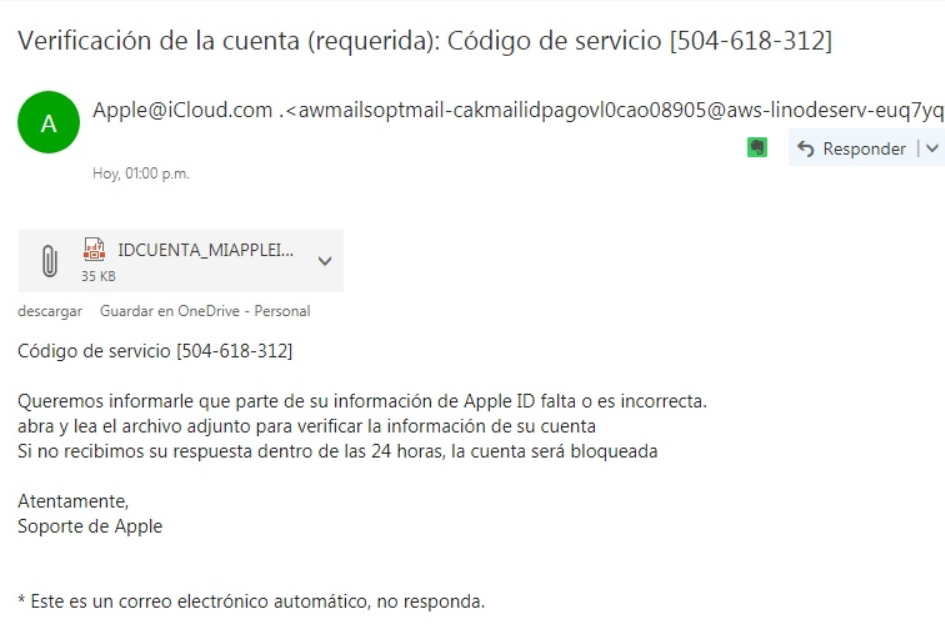
4. Be “phishing aware”
Be careful what opens in your email. For example, do not click on links and attached forms in an email whose sender you do not know. These links may carry malicious content, and the forms will attempt to retrieve all your personal information. Phishing appeared long ago and becomes more and more sophisticated over time.
5. Think before downloading
Before downloading the application or program, verify the authenticity of the site from which you want to download it. If you doubt the site’s authenticity because of its illiteracy or for some other reason, then go to the sources familiar to you and download from there all that you need.
6. Create and use complex passwords
Complex and reliable passwords are another way to protect yourself from unwanted pests. Create a password with at least 12 characters and use lower case and upper case letters; you can also include different types of surfaces. Average-difficulty passwords are easier to crack. This is because they can be in the password dictionary that the attacker uses for brute force attacks.
7. Use antivirus and antimalware software
Using a reliable security solution is another good additional layer of protection for your data and your entire system. GridinSoft Anti-Malware will be a good help for you when using different browsers. It is designed to scan your system and online activities continuously. This protection will alert you to a potential threat if it detects a malicious site or a doubtful program. GridinSoft Anti-Malware is also designed to remove all malware from your PC.





