Bloom.exe is a malicious miner that masquerades as a legitimate process. Its job is to use the victim’s device to mine cryptocurrency for con actors. The most visible sign of its presence, aside from the process in the Task Manager, is an enormously high CPU load that comes from it. This effectively renders your system unusable, causing stutters and even crashes.
Bloom.exe Miner Overview
Bloom.exe is a process created by coin miner malware. This class of malware exploits the hardware of the victim’s system to mine cryptocurrency. The name “Bloom.exe” serves only to make the malware look as legitimate process and confuse the user. Like malicious miners of this kind, it mines Monero or DarkCoin, with all profits going to the attacker.
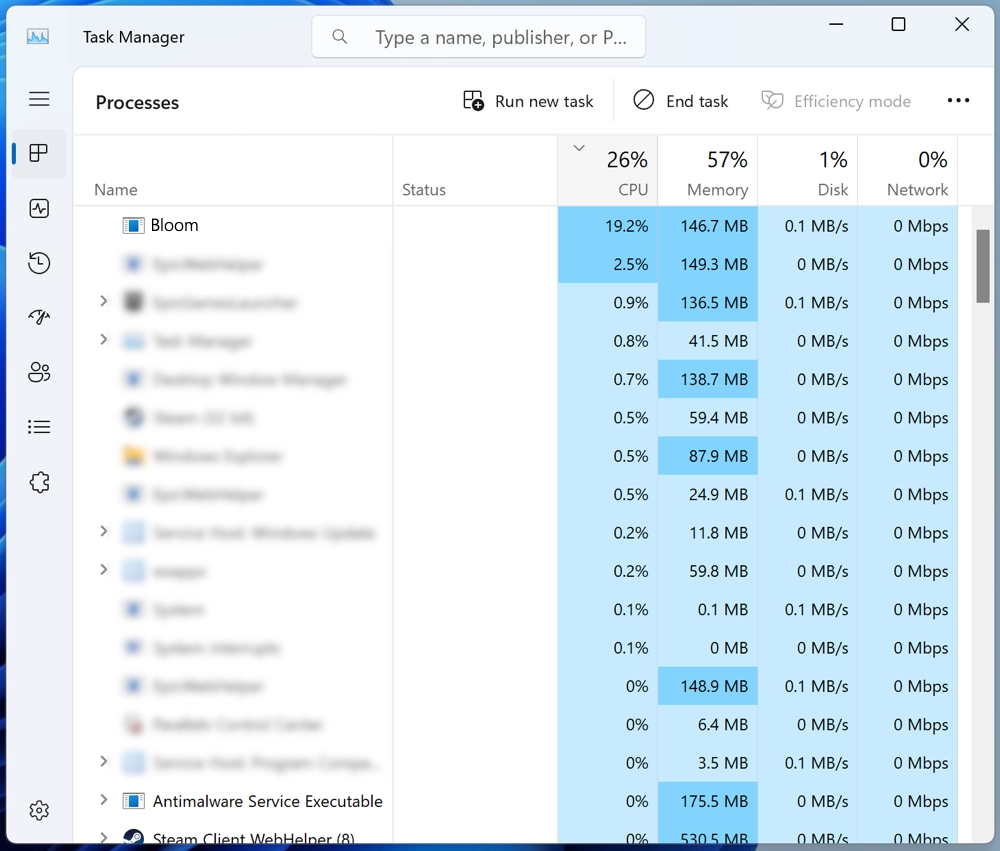
The Bloom.exe miner monitors system usage and adjusts its resource consumption accordingly. This makes its less noticeable, as it does not consume all available resources as other miners do. Additionally, Bloom.exe is able to use GPU resources, improving the effectiveness of the mining process, and making it harder to detect the malware activity (if you’re not gaming or don’t pay attention to fan noise levels).
Spreading Methods
As for distribution, Bloom.exe is similar to the other miners. It is mainly distributed under the guise of legitimate software. The second, but almost as popular method is drive-by downloads and illegal software, such as pirated games or cracked programs.
A less effective but no less popular method of distribution is malvertising. Con actors can hijack search results for some popular software, to let the users to their sites instead of genuine ones. And instead of getting the installer of a program, users download and run malware, with Bloom.exe miner being among them.
Technical Analysis
Let’s take a closer look at how this miner behaves. In fact, the majority of miner malware behaves rather similar, regardless of whether they are stand-alone or are based on XMRig or another well-known open-source project.
Traditionally, malware begins its life cycle by checking for a virtual environment, sandbox, or debugging tools. To do this, our sample checks the following registry keys:
HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\Safer\CodeIdentifiers
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Session Manager\AppCertDlls
These keys contain some system settings and Windows security policies. Besides doing these checks, this malware often has its code packed, encrypted and obfuscated. These “passive” protection measures make Bloom.exe a tough nut for basic antiviruses.
C2 Communication
The malware uses several addresses for communications, including TCP 204.79.197.203:443, which belongs to Microsoft. This is possibly because frauds use some of the cloud services MS offers to anyone. Despite they are easy to take down, it is also easy to create new ones. There are also several addresses that could potentially belong to the command server:
https://pdfcrowd.com/?ref=pdf
https://pdfcrowd.com/doc/api/?ref=pdf
https://gettodaveriviedt0.com/secur3-appleld-verlfy1/?16shop
Payload
After all the checks and communications, the malware drops a payload on the system. It also loads a large number of files into the %windir%\System32\ folder, among which are:
C:\Windows\System32\OHcvDRK.exe
C:\Windows\System32\ROKnunx.exe
C:\Windows\System32\TAtNGGl.exe
C:\Windows\System32\WQDfJPu.exe
These are only a small part of what malware brings to the system; the more time malware is active – the more of these fileswill appear. Inside of these files are either modules that allow for certain functionality, or mining configurations.
How to Remove Bloom.exe?
To effectively remove Bloom.exe, I recommend using GridinSoft Anti-Malware, as it will easily detect and stop any malicious program, including this miner. Contrary to manual removal, this program will find every single element of the malware, ensuring that it won’t come back.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.