Malware VS Ransomware: What’s the Difference?
To deal with any problem successfully you should first have a clear understanding of what you are dealing with. Nowadays the cyber threat landscape has expanded enormously with online cyber…
TOP 7 Types of Password Attacks
What is a Password Attack? In the beginning, you probably already understood from the name what these attacks are and what they are aimed at. It is resistance against someone…
Critical Vulnerability in UNISOC Devices Patched
UNISOC-chip Android Phones are Vulnerable to Remote Modem-Targeting Attacks In May 2022, the UNISOC company was informed by Check Point Research specialists about a critical vulnerability present in UNISOC chipset…
Information Security Specialists Discovered a 0-day Vulnerability in Windows Search
A new 0-day Windows Search vulnerability could be used to automatically open a search box and launch remote malware, which is easily done by simply opening a Word document. Bleeping…
Clipminer – a Million Dollar Clipboard Hijacking Coinminer
Clipminer Malware A bizarrely efficient botnet cryptocurrency miner has been revealed by Symantec security experts. Besides its classic mining function, it has a feature of clipboard hijacking, thence comes the…
CMD-Based Ransomware YourCyanide With Info-Stealing Functions
New Threat: YourCyanide Ransomware CMD-based ransomware YourCyanide, currently under development, has been found and analyzed recently by the Trend Micro group of malware researchers. The malware in question does not…
Chinese Hackers Attack Fresh 0-day Follina Vulnerability
Experts have warned that Chinese hackers are already actively exploiting a 0-day vulnerability in Microsoft Office known as Follina to remotely execute malicious code on vulnerable systems. Let me remind…
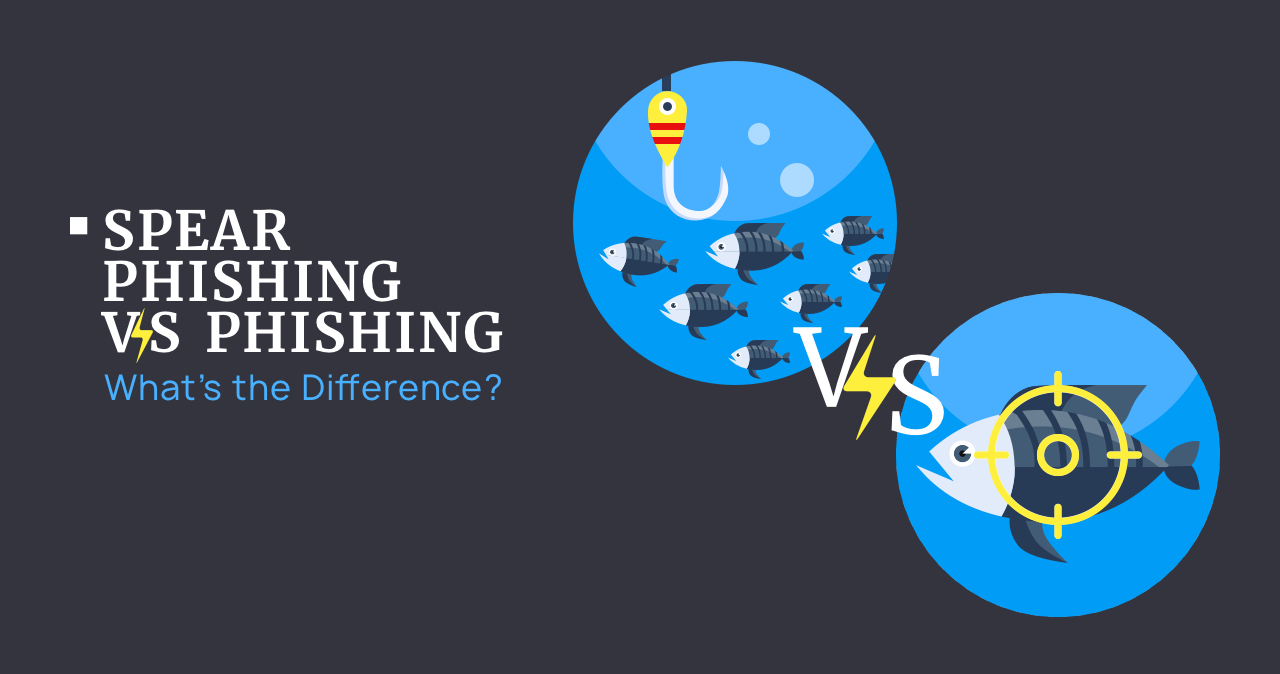
What is Spear Phishing? Definition with Examples
Spear phishing is a type of phishing attack that targets specific individuals or organizations typically through malicious emails. For example, cybercriminals can pretend to be a trusted person or organization…
Europol and Intelligence Agencies of 11 Countries Destroyed the FluBot Trojan Infrastructure
Europol announced that law enforcement officers, as a result of an international operation, destroyed one of the fastest-spreading malware - the FluBot Trojan. Let me remind you that we also…
Three Online Scammers Arrested in Nigeria in an Interpol’s Operation
North Africa, Southeast Asia, and Middle East oil and gas companies became cyberfraud victims. Interpol arrested three citizens of Nigeria in the country's capital city Lagos as a part of…
29 Moonbirds Stolen via Link Click from a Proof Collective Member
29 Moonbirds, NFTs amounting to around 750 ETC (approximately $1,5M) in value, were stolen from an unmentioned Proof Collective member as a result of a scam, according to the May…
Attackers Are Already Exploiting the Fresh 0-day Follina Bug in Microsoft Office
Security researchers recently discovered a zero-day vulnerability in Microsoft Office dubbed Follina. The bug can be exploited through the normal opening of a Word document, using it to execute malicious…