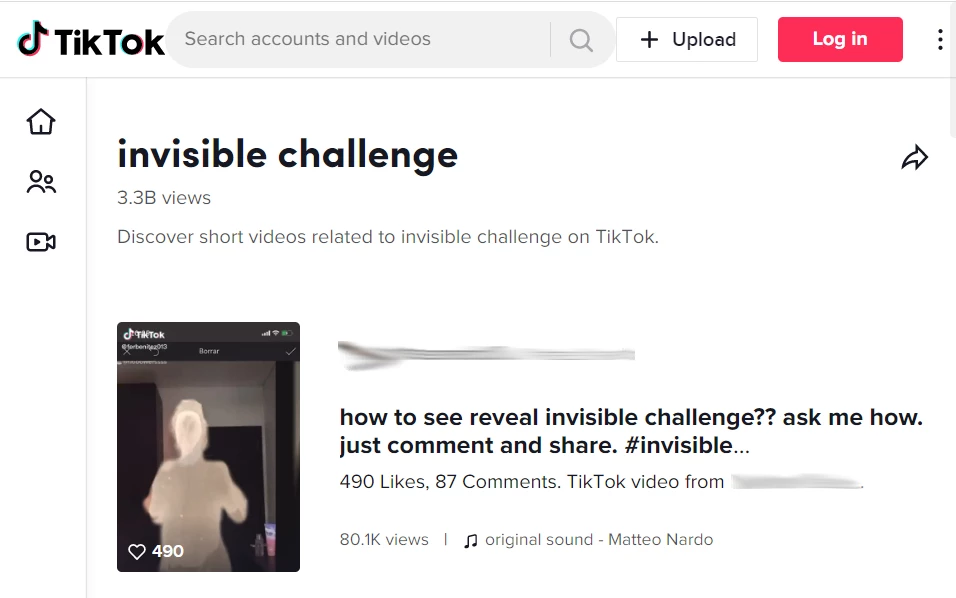
TikTok Invisible Challenge Is Used to Spread Malware
TikTok Invisible Challenge became yet another host for threat actors. Crooks found a way to spread the WASP information stealer as a specific utility to revert the in-app filter. Users…
Ragnar Locker Ransomware Accidentally Attacked Belgian Police
The operators of the ransomware Ragnar Locker published on their “leak site” the data stolen from the police unit of the Belgian province of Antwerp. The problem is that the…
WhatsApp Hacked, Almost 500 Million Users Exposed
On November 28, 2022, information regarding a new WhatsApp breach appeared. The hacker offers a database with stolen data for sale since November 16. The offered pack contains the data…
Online Dating Scams: How to Avoid Romance Scam
Online dating scammers get you to believe that their fake romances are real. They use deceptive tactics to make their scams hard to detect. The overall fraud got the name…
“Password” Topped the List of the Most Common Passwords in 2022
The NordPass password manager team has prepared annual statistics by analysing the most commonly used and weakest passwords of 2022. Let me remind you that we also wrote that Password…
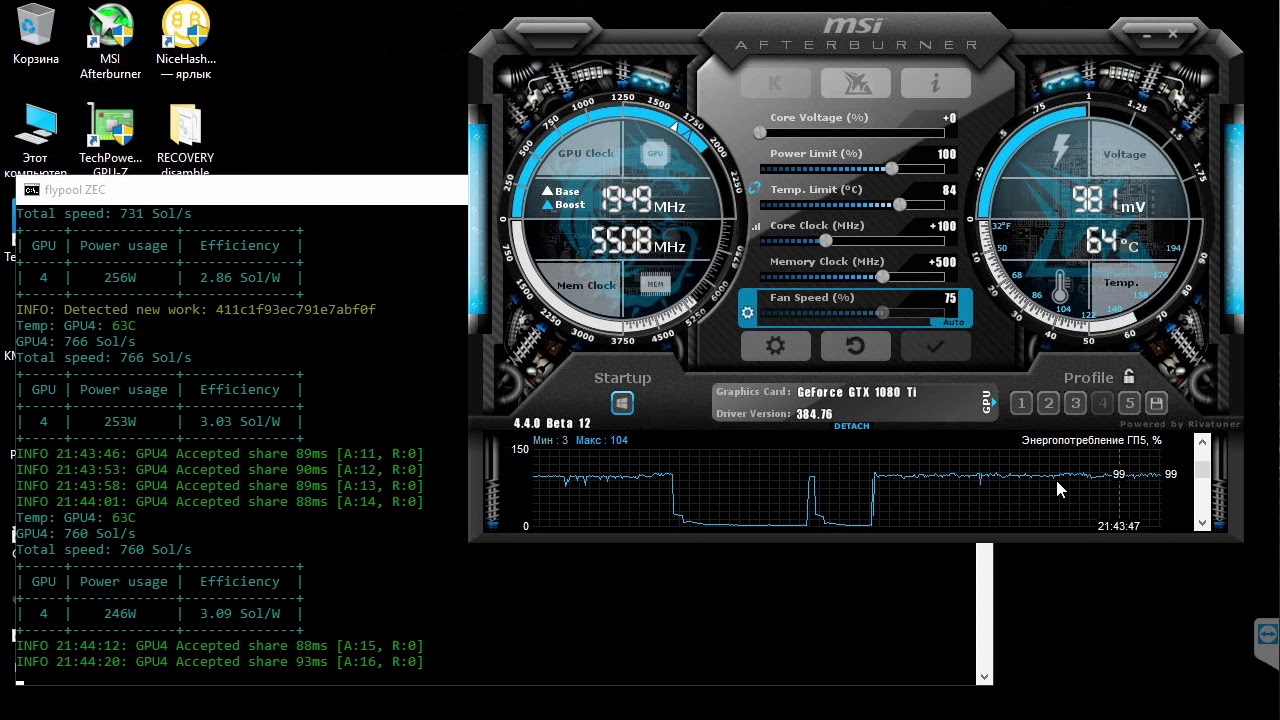
Fake MSI Afterburner Infects Users’ Machines with Miners and Stealers
According to cybersecurity specialists from Cyble, attackers distribute miners and the RedLine infostealer using download sites for the fake MSI Afterburner utility. Over the past three months, more than 50…
Chrome Extension ViperSoftX Steals Passwords and Cryptocurrency
A Windows malware designed to steal cryptocurrency and clipboard contents installs a malicious VenomSoftX Chrome extension on users' machines. The extension works like a RAT (Remote Access Trojan), stealing victims'…
Apple ID Scams: Identify and Prevent Apple Phishing Email
Apple users are believed to be protected from all sorts of fraud and hacking. That’s because Apple designs its technologies with all required privacy and security requirements. But alas, fraudsters…
Black Friday Scams: Ways to Detect & Avoid Shopping Frauds
As the main shopping event of the year approaches, Black Friday shopping scams have into view. Con actors from all over the world try to create the most convincing fraud,…
Exploit for Vulnerabilities ProxyNotShell Appeared on the Network
Experts warned that an exploit for two high-profile vulnerabilities in Microsoft Exchange, which are collectively called ProxyNotShell, has appeared in the public domain. Vulnerabilities have been used by hackers before,…
Security Experts Secretly Helped Zeppelin Ransomware Victims for Two Years
Since 2020, some information security specialists have helped victims, as individuals and companies affected by the Zeppelin ransomware. The fact is that a number of vulnerabilities were found in the…
Unit221b Secretly Helped Victims of Zeppelin Ransomware for 2 Years
Security professionals at Unit221b found vulnerabilities in the Zeppelin ransomware encryption mechanism. Experts managed to use them to create a working decryptor that they have been using since 2020 to…