The US suspends its cooperation with Russia on ransomware criminals amidst the brutal war the Russian government wages against Ukraine, State Department spokesperson told Sputnik. “The Russian government is engaged in a brutal and unjustified war against Ukraine, so our channel on criminal ransomware actors is not active,” the spokesperson said. On Thursday White House… Continue reading The US won’t cooperate with Russia on ransomware anymore
Author: Stephanie Adlam
I write about how to make your Internet browsing comfortable and safe. The modern digital world is worth being a part of, and I want to show you how to do it properly.
RaidForums shutdown as the result of Operation Tourniquet
The chain of international law enforcement agencies – Europol, FBI, NCA and others – seized the world’s largest hacker forum – RaidForums. That seems to be part of an anti-cybercrime campaign that started from the Hydra Shop shutdown. On April 12, 2022, the National Crime Agency (shorty NCA) reported on their official website about the… Continue reading RaidForums shutdown as the result of Operation Tourniquet
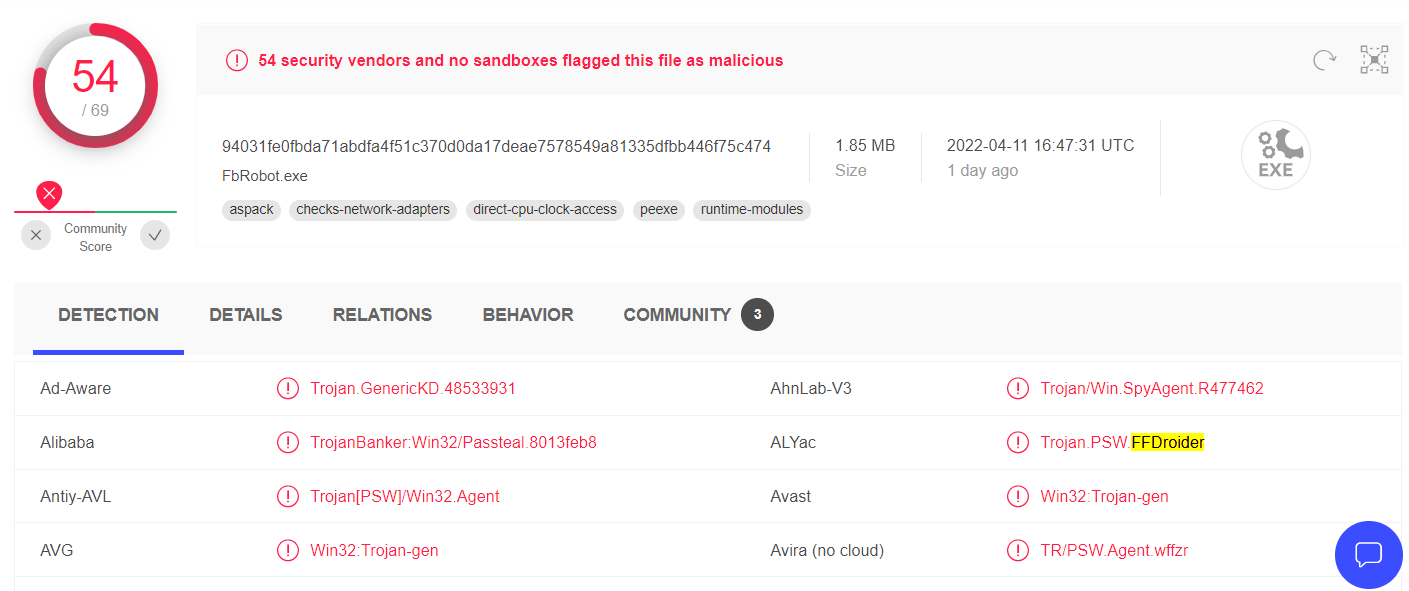
FFDroider Stealer – the new hazard to your social networks
FFDroider is an example of a modern stealer malware that aims at sensitive data in web browsers. The overall amount of new stealers that appeared in the first quarter of 2022 says a lot about the new malware trends. FFDroider Stealer is the second malware of this type that popped out last month. The BlackGuard… Continue reading FFDroider Stealer – the new hazard to your social networks
Meta Infostealer Malware Spread via Spam
Meta, a newly crafted information-stealing malware, is distributed via a vast spam spree. The mechanism of the stealer injection within this campaign is already well-known. However, Meta is now a mainstream tool among hackers. Therefore, further attacks featuring this software but with different scenarios are inevitable. This article explains how the current malspam scheme works.… Continue reading Meta Infostealer Malware Spread via Spam
Hydra Market Shut Down by the German Authorities
The United States, together with its European allies, has managed to get Hydra market shut down. Servers of this shop, a Russian-language darknet platform, were reported on Tuesday, April 5, 2022, to be seized by German authorities. The marketplace used to be a place to mainly trade illegal drugs and documents, mix cryptocurrency, and exchange… Continue reading Hydra Market Shut Down by the German Authorities
Pornographic virus alert from Microsoft
Microsoft shows you the banner which states that your PC is infected with a “Pornographic virus”? It seems that someone wants to involve you in a popular online tech support scam, called “Pornographic virus alert from Microsoft”. But how can they do it with a single banner? That article will show you the whole mechanism… Continue reading Pornographic virus alert from Microsoft
How to Clean Up And Speed Up Your Computer?
We used to think about computers as insensitive robots that could run without any problems for days, weeks, or even months. However, even machines that consist only of electronic circuits and wires need to be cleaned. The problem is much more complicated than you may think – each type of cleaning is preferable for a… Continue reading How to Clean Up And Speed Up Your Computer?
The Facebook Pixel Hunt
Mozilla, a browser maker, these days introduced its collaboration with a non-earnings newsroom Markup. The collective efforts of companies could be directed toward studies into a selected subject of the net that regularly stays disregarded through customers, researchers and policymakers. This time beneath the scrupulous eyes of experts and newshounds the predominant social platform Facebook… Continue reading The Facebook Pixel Hunt
What Is VulkanRT? Does It a Virus?
As a user, you may have concerns when you notice an unknown folder and a program icon in the Windows Start Menu, both named VulkanRT. What is this program? Whence it came? Is VulkanRT a virus? Should I remove it? If these questions flash in your mind, you’ve come to the right place. In this… Continue reading What Is VulkanRT? Does It a Virus?
Volvo Cars under Snatch attack
In its press release, Volvo Cars, a Swedish multinational luxury vehicle manufacturer based in Torslanda, Gothenburg, reported unlawful third party access to its records. Upon discovery of the violation, the company notified the relevant authorities and took steps to prevent further access to its property. Immediately shares of Volvo Cars fell 3.2% at 3:55 p.m.… Continue reading Volvo Cars under Snatch attack