PUABundler:Win32/DriverPack is potentially unwanted software that claims to install or update drivers. In fact, it floods the system with unwanted software and changes browser settings without the user’s consent. In this post, I will explain the dangers behind this unwanted app and show the ways to remove it from the system.
PUABundler:Win32/DriverPack Overview
PUABundler:Win32/DriverPack is a detection from Microsoft Defender, associated with the eponymous DriverPack Solution program. Initially, it was a program developed by a Russian author for automatic driver installation on Windows XP. However, since Windows began carrying all the necessary drivers in the installation, driver updaters have become useless. Moreover, the fact that a program operates with drivers creates significant security threats and thus should undergo diligent checks.
And that is where DriverPack shows its dark nature. Over time, it started installing additional software during its own installation – so-called software bundling. Today, DriverPack is synonymous with a bunch of unwanted and sometimes malicious software that can easily brick a freshly installed Windows. This is evidenced by many users on the Internet who have decided to take the easy way out and use DriverPack to install drivers. After using this program, at best, users get a bunch of garbage in the system. At worst, certain devices or system components may malfunction or fail.
Why is PUABundler:Win32/DriverPack Dangerous?
To understand why using DriverPack is dangerous, it’s important to understand its operation. The first version of DriverPack was a standalone installer that installed drivers on devices that don’t have ones. But these days, this program tries to update existing drivers on the system – an edgy approach, if you ask me. The problem is that the program sources newer drivers from questionable places. This may result in aforementioned failures across the system, but, what is worse – it is a direct malware risk.
Another issue is the unwanted software bundled with PUABundler:Win32/DriverPack. Regardless of the user choice, DriverPack installs its services, injects advertisements all across the system, and modifies browser homepages in all browsers. For the latter, instead of the standard search and homepage, DriverPack sets Internet-start.net (see the scan report) as the default homepage and search engine. Although the official website claims to cooperate with antivirus vendors, users tend to see a different picture.
User Experience
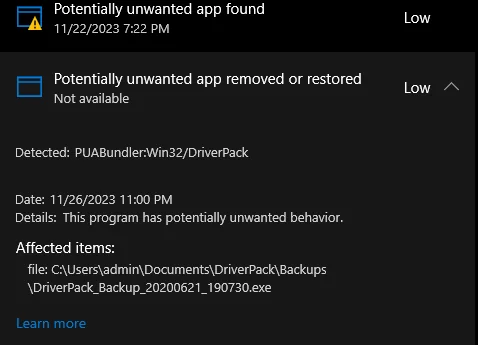
I decided to simulate a clean OS setup and driver installation using DriverPack (sample analysis report) in fully automatic mode. This allowed me to get a complete opinion on what PUABundler DriverPack is. There are several red flags that appear even before the installation, but more are to come.
The first warning sign is the claim about false positives from certain antiviruses on the main page. Although this may be the case, false positives are normally a temporare occasion. You should not expect a legit program being detected as unwanted or malicious on a continuous basis, otherwise it is not an occasional situation and a real detection. And the claim on the website suggests that the latter is true. During the launch and operation of the installer itself, Microsoft Defender really flagged PUA presence in the system.
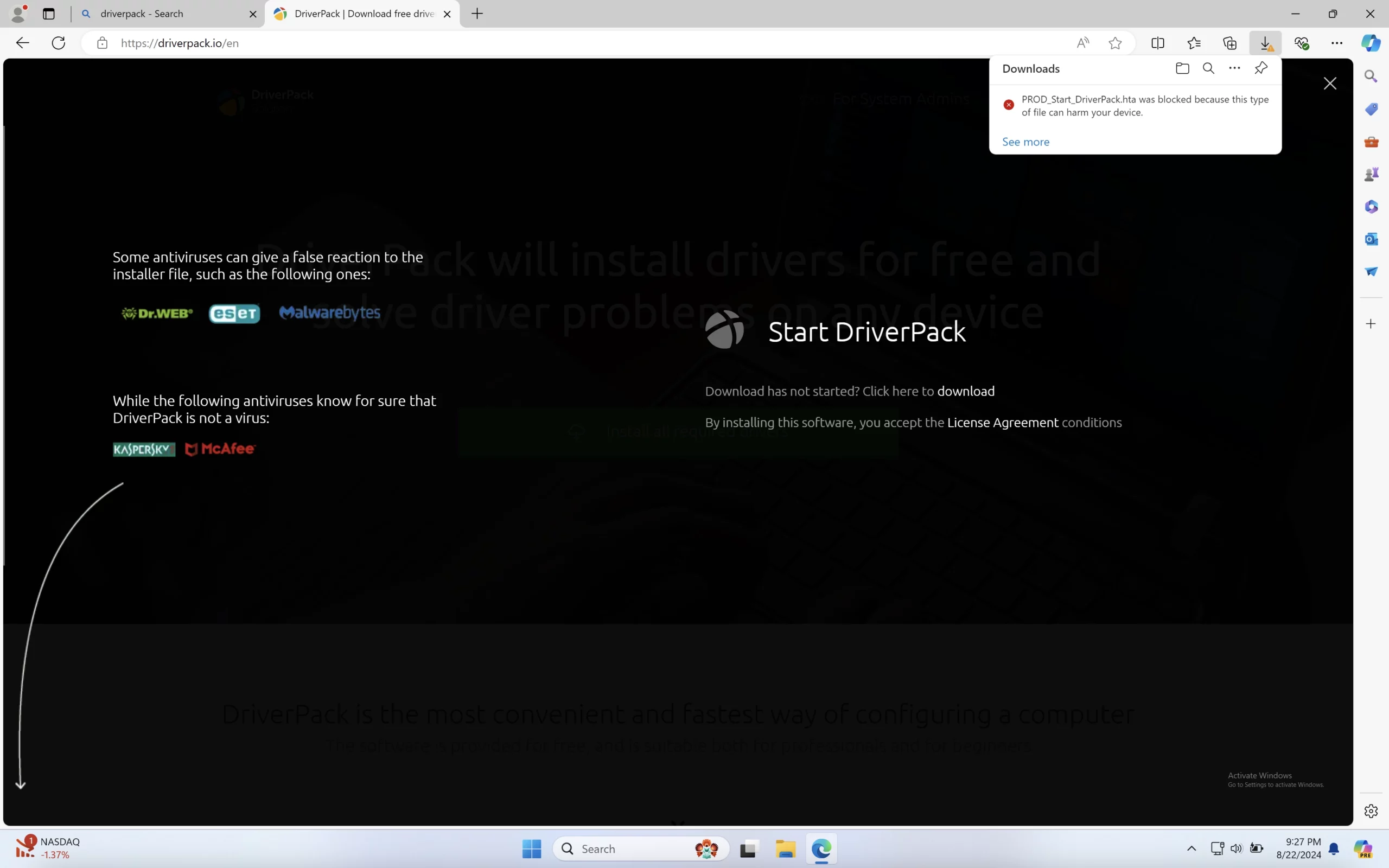
And, sure enough, the described changes to the web browser popped up. PUABundler:Win32/DriverPack modified the homepage and the default search engine. The latter, in turn, shows questionable search results, which is a rather straightforward phishing risk: by manipulating the results, fraudsters behind the search engine can push malicious results to the top. The unwanted program does all this to generate revenue through ads and user redirects, not for the convenience of users. And these ads are the reason why some of the DriverPack samples are tagged as adware.

Technical Analysis
Let’s now examine the technical aspects of this unwanted software. I analyzed a copy downloaded from the official website. Notably, it has 53 out of 75 detections on VirusTotal, and the reason is obvious. During installation, PUABundler:Win32/DriverPack leverages the Mshta.exe process, typically used to execute HTML applications. It then loads an executable from AppData\Local\Temp into a temporary folder and executes the following command:
"C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\
"C:\Windows\SysWOW64\mshta.exe" "C:\Program Files (x86)\DriverPack\run.hta" {1E460BD7-F1C3-4B2E-88BF-4E770A288AF5}{1E460BD7-F1C3-4B2E-88BF-4E770A288AF5} --sfx "software.exe"
During installation, DriverPack checks the system’s software and hardware components by going through certain registry keys. This is a standard procedure for such programs, designed to locate drivers, so it is barely a bad sign. And even if we suppose a malicious intent, the worst thing this data may be used for is to distinguish this system from the others.
HKEY_LOCAL_MACHINE\Software
HKEY_LOCAL_MACHINE\System\Setup
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion
Suspicious network activity
First thing DriverPack modifies during execution is firewall settings – mostly to let its own executable files communicate with the remote servers. Still, the fact that the developer does not specify the source of the drivers, it is not a great thing to have such an all-encompassing access.
"C:\Windows\System32\cmd.exe" /c "netsh advfirewall firewall delete rule name="DriverPack aria2c.exe" || echo Done & call echo Done %^errorLevel% > "C:\Users\
netsh advfirewall firewall delete rule name="DriverPack aria2c.exe"
rundll32 kernel32,Sleep
"C:\Windows\System32\cmd.exe" /c "netsh advfirewall firewall add rule name="DriverPack aria2c.exe" dir=in action=allow program="C:\Program Files (x86)\DriverPack\tools\aria2c.exe" || echo Done & call echo Done %^errorLevel% > "C:\Users\
netsh advfirewall firewall add rule name="DriverPack aria2c.exe" dir=in action=allow program="C:\Program Files (x86)\DriverPack\tools\aria2c.exe"
Payload
PUABundler:Win32/DriverPack utilizes the aria2c.exe utility to download several strangely-named files. This is rather concerning, as such a filename leaves no clue on what is the purpose of it and what are the possible effects.
"C:\Windows\SysWOW64\mshta.exe" "C:\Program Files (x86)\DriverPack\run.hta" --sfx "c99687e9829de410b66ad7006b0604c3fddb4582050ce205c1d00ff9f309e6b8.exe"
C:\Program Files (x86)\DriverPack\run.hta --sfx "c99687e9829de410b66ad7006b0604c3fddb4582050ce205c1d00ff9f309e6b8.exe"
C:\Program Files (x86)\DriverPack\start.bat "c99687e9829de410b66ad7006b0604c3fddb4582050ce205c1d00ff9f309e6b8.exe"
This represents just a fraction of what DriverPack downloads. During installation, it downloads the bundled applications – several browsers, a strange copy of Avast antivirus, and the “widgets” for the DriverPack itself. As there is no way to disable the installation of these bundled apps, this is just another concerning element of that program.
C:\Program Files (x86)\DriverPack\Tools\driverpack-wget.exe
C:\Program Files (x86)\DriverPack\programs\AvastAntivirusA.exe
C:\Program Files (x86)\DriverPack\programs\downloader_elements.exe
C:\Program Files (x86)\DriverPack\programs\downloader_browser.exe
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\DriverPack\DriverPack.lnk
During execution, the shell displays a “virtual assistant” that occasionally speaks to the user. Nothing really malicious here, but it may be spooky to someone who did not expect a program installer to have sound effects. And overall, there are more than enough problems for the DriverPack to be considered a dangerous thing.
How To Remove DriverPack?
Manual removal of PUABundler:Win32/DriverPack is not really an option, so I recommend an automated removal with GridinSoft Anti-Malware. Follow the guide below to get your system cleaned of DriverPack PUA and all other malicious elements that may be present.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.