Your antivirus just flagged Trojan:Win32/Vigorf.A and you’re wondering what’s going on. Your computer might be running slow. The CPU fan won’t stop spinning. You see strange processes eating up system resources.
This guide will help you remove this threat completely. Follow these step-by-step instructions to eliminate Trojan:Win32/Vigorf.A from your Windows 11 system. We’ll start with methods you can try right now.
| Detection Name | Trojan:Win32/Vigorf.A |
| Threat Type | Dropper/Loader Malware (Generic Detection) |
| Primary Function | Downloads and installs additional malware payloads |
| Target Systems | Windows 7, 8, 10, 11 (32-bit and 64-bit) |
| Common Sources | Malicious email attachments (.zip, .exe), fake software downloads, compromised websites, USB drives |
| False Positive Rate | High – Frequently flags legitimate software (Ableton, R2R cracks, media tools) |
| Typical File Locations | %TEMP%, %APPDATA%, C:\Windows\Temp\, Program Files folders |
| Network Activity | Connects to C&C servers, downloads additional payloads, data exfiltration |
| System Impact | High CPU usage, slow performance, registry modifications, startup entries |
| Secondary Payloads | Ransomware, cryptocurrency miners, information stealers, banking trojans |
| Detection Difficulty | Medium – Uses obfuscation and polymorphic techniques |
| Removal Complexity | High – Multiple components, registry persistence, potential system file infection |
Trojan:Win32/Vigorf.A is Microsoft Defender’s detection for dropper malware. It downloads other threats to your computer. But here’s the catch – many legitimate programs trigger this detection too. Cracked software, music production tools, and even some Dell utilities can cause false positives.
Is This a False Positive?
Before we start removal, let’s figure out if you’re dealing with a real threat. Many Vigorf.A detections are false positives. Here’s how to tell:
Signs It’s Probably a False Positive
- Just installed new software: Did the detection appear right after installing Ableton Live, R2R cracks, or media tools?
- Recognize the file path: Is the detected file in a program folder you know?
- No actual symptoms: Computer runs normally, no suspicious network activity
- Only one scanner detects it: Upload to VirusTotal – if only 1-2 scanners flag it, likely false positive
Signs It’s Real Malware
- Appeared randomly: No recent software installations
- System acting weird: Slow performance, high CPU usage, strange network activity
- Unknown file locations: Files in temp folders or random system directories
- Multiple scanners detect it: Several antivirus programs flag the same file
Common false positive triggers include cracked games, music production software, and activation tools. When detections come from these sources, you’re probably dealing with a false positive rather than real malware.
Manual Removal Steps
Once you’ve confirmed this is genuine malware, here’s how to remove it manually. These steps work for actual Vigorf.A infections.
Step 1: Boot into Safe Mode
Safe Mode prevents malware from running while you clean your system. This makes removal much easier.
- Press Windows + R keys together
- Type msconfig and press Enter
- Click the Boot tab
- Check Safe boot and select Minimal
- Click OK and restart your computer
Step 2: Stop Malicious Processes
Vigorf.A runs background processes to maintain its presence. We need to stop these first.
- Press Ctrl + Shift + Esc to open Task Manager
- Look for suspicious processes with random names or high CPU usage
- Right-click suspicious processes and select End task
- Note the file locations for later deletion
Common malicious process names include random characters, misspelled system processes, or executables in temp folders. Similar to other trojan infections, these processes often consume significant system resources.
Step 3: Delete Malicious Files
Now we’ll remove the actual malware files. Check these common locations:
- Navigate to C:\Users\[Username]\AppData\Local\Temp\
- Look for recently created files with suspicious names
- Delete any files that match the detection path from Windows Defender
- Check C:\Windows\Temp\ for additional malicious files
- Empty the Recycle Bin when finished
Be careful not to delete legitimate system files. When in doubt, research the filename online before deletion.
Step 4: Clean Registry Entries
Vigorf.A creates registry entries to start automatically. We need to remove these to prevent reinfection.
- Press Windows + R and type regedit
- Navigate to HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Look for suspicious entries pointing to deleted files
- Right-click and delete any malicious entries
- Also check HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
Like many advanced trojans, Vigorf.A uses registry modifications to maintain persistence on infected systems.
Step 5: Check Scheduled Tasks
Some variants create scheduled tasks to restart themselves. Let’s remove these:
- Press Windows + R and type taskschd.msc
- Look through the task list for recently created tasks
- Delete any tasks that reference the malicious files you removed
- Pay attention to tasks with random names or suspicious triggers
Step 6: Reset Network Settings
Some Vigorf.A variants modify network settings. Let’s reset these:
- Open Command Prompt as administrator
- Run these commands one by one:
netsh winsock reset
netsh int ip reset
ipconfig /flushdns
- Restart your computer after running these commands
Step 7: Exit Safe Mode
Once you’ve completed all removal steps:
- Press Windows + R and type msconfig
- Uncheck Safe boot in the Boot tab
- Click OK and restart normally
Manual removal can miss hidden components that sophisticated malware like Wacatac variants often leave behind. If symptoms persist, automatic removal is recommended.
Automatic Removal with GridinSoft Anti-Malware
Manual removal can be complex and time-consuming. For a faster, more reliable solution, GridinSoft Anti-Malware offers automatic detection and removal of Vigorf.A trojans. Professional anti-malware software can find hidden components and registry changes that you might miss.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

Browser Cleanup
If Vigorf.A infected your system, it might have installed browser-based threats too. These steps will clean your browsers completely.
Remove Malicious Browser Extensions
Trojan droppers often install browser extensions to steal data or redirect searches. Remove any suspicious extensions:
Google Chrome
- Launch the Chrome browser.
- Click on the icon "Configure and Manage Google Chrome" ⇢ Additional Tools ⇢ Extensions.
- Click "Remove" next to the extension.
If you have an extension button on the browser toolbar, right-click it and select Remove from Chrome.
Mozilla Firefox
- Click the menu button, select Add-ons and Themes, and then click Extensions.
- Scroll through the extensions.
- Click on the … (three dots) icon for the extension you want to delete and select Delete.
Microsoft Edge
- Launch the Microsoft Edge browser.
- Click the three dots (…) menu in the top right corner.
- Select Extensions.
- Find the extension you want to remove and click Remove.
- Click Remove again to confirm.
Alternatively, you can type edge://extensions/ in the address bar to access the extensions page directly.
Opera
- Launch the Opera browser.
- Click the Opera menu button in the top left corner.
- Select Extensions ⇢ Manage extensions.
- Find the extension you want to remove and click the X button next to it.
- Click Remove to confirm.
Alternatively, you can type opera://extensions/ in the address bar to access the extensions page directly.
Reset Your Browser
If you suspect browser-based infections, reset your browser completely. This removes all modifications while keeping your bookmarks and passwords safe:
Google Chrome
- Tap on the three verticals … in the top right corner and Choose Settings.
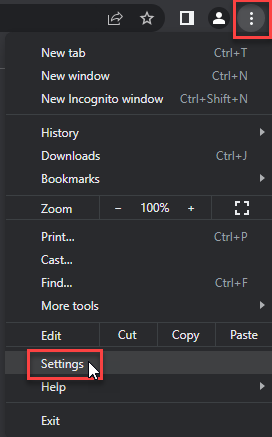
- Choose Reset and Clean up and Restore settings to their original defaults.
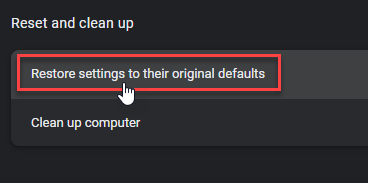
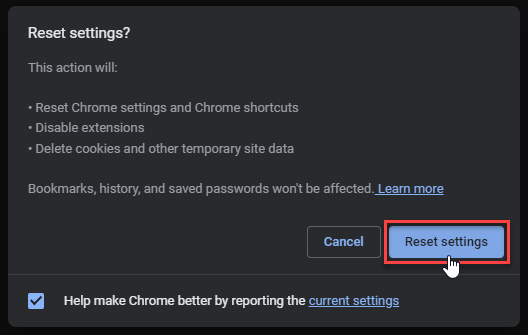
- Tap Reset settings.
Mozilla Firefox
- In the upper right corner tap the three-line icon and Choose Help.
- Choose More Troubleshooting Information.
- Choose Refresh Firefox… then Refresh Firefox.
Microsoft Edge
- Tap the three verticals.
- Choose Settings.
- Tap Reset Settings, then Click Restore settings to their default values.
Opera
- Launch the Opera browser.
- Click the Opera menu button in the top left corner and select Settings.
- Scroll down to the Advanced section in the left sidebar and click Reset and clean up.
- Click Restore settings to their original defaults.
- Click Reset settings to confirm.
Alternatively, you can type opera://settings/reset in the address bar to access reset options directly.
Browser infections are common with information stealing malware that often gets dropped by trojans like Vigorf.A.
How to Prevent Future Infections
Prevention is always better than removal. Here’s how to keep Vigorf.A and similar threats away from your system:
Email Safety
Most Vigorf.A infections start with malicious email attachments. Be suspicious of:
- Unexpected attachments from unknown senders
- Urgent messages asking you to open files
- ZIP files containing executable files
- Invoices or documents from companies you don’t recognize
These tactics are similar to those used in professional hacker email scams that have become increasingly sophisticated.
Download Safety
Only download software from official sources. Avoid:
- Cracked software and keygens (common false positive sources)
- Software from file-sharing sites
- Programs advertised through pop-up ads
- Free versions of paid software from unofficial sites
System Security
Keep your system secure with these practices:
- Keep Windows updated: Install security patches promptly
- Use real-time protection: Don’t disable Windows Defender unless necessary
- Regular backups: Keep important files backed up externally
- User Account Control: Don’t disable UAC warnings
Consider using additional protection against fake virus alerts and other social engineering attacks that often distribute trojans.
Handling False Positives
When you’ve confirmed your Vigorf.A detection is a false positive, here’s how to handle it safely:
For Legitimate Software
- Quarantine the file instead of deleting it
- Verify the software is from a trusted source
- Submit the file to Microsoft for analysis
- Create an exclusion in Windows Defender if confirmed safe
Adding Exclusions Safely
Only add exclusions for files you absolutely trust:
- Open Windows Security
- Go to Virus & threat protection
- Click Manage settings under Virus & threat protection settings
- Click Add or remove exclusions
- Add the specific file or folder path
Be extremely cautious with exclusions. They can leave your system vulnerable if you exclude actual malware. When dealing with heuristic detections, false positives are more common but still require careful verification.
System Recovery
If Vigorf.A caused significant damage to your system, you might need additional recovery steps:
System File Check
Run this command to repair corrupted system files:
sfc /scannow
System Restore
If you have a restore point from before the infection:
- Type rstrui in the Start menu
- Select a restore point from before the infection
- Follow the wizard to restore your system
System restore can help recover from damage caused by various trojan variants that modify system settings.
Frequently Asked Questions
What is Trojan:Win32/Vigorf.A and why is it dangerous?
Vigorf.A is a dropper trojan that downloads and installs other malware on your computer. It can install ransomware, cryptocurrency miners, or information stealers. However, many detections are false positives from legitimate software.
How did Vigorf.A get on my computer?
Real infections usually come from malicious email attachments, fake software downloads, or compromised websites. False positives appear when legitimate software like cracked games or audio tools trigger Microsoft Defender’s generic detection.
Can I remove Vigorf.A manually?
Yes, you can remove genuine infections manually by following our step-by-step guide above. However, automatic removal tools are more thorough and can find hidden components that manual removal might miss.
Is it safe to delete files detected as Vigorf.A?
Only delete files if you’re certain they’re malicious. If the detection points to legitimate software you intentionally installed, it’s likely a false positive. Quarantine first, then investigate before permanent deletion.
How can I prevent Vigorf.A infections?
Avoid opening suspicious email attachments, only download software from official sources, keep Windows updated, and maintain active antivirus protection. Be especially careful with cracked software and free downloads from unofficial sites.
What if manual removal doesn’t work?
If manual removal fails, the infection might have deep system integration or multiple components. Use professional anti-malware software like GridinSoft Anti-Malware for comprehensive detection and removal of all malicious components.
Why does legitimate software trigger Vigorf.A detection?
Microsoft Defender uses behavioral analysis to detect threats. Legitimate software that modifies files, injects code, or bypasses system protections can appear suspicious to the scanner, triggering false positive detections.
Should I disable Windows Defender to avoid false positives?
Never disable your antivirus completely. Instead, add specific exclusions for verified legitimate software. Disabling protection leaves your system vulnerable to real threats that could cause serious damage.
Final Thoughts
Trojan:Win32/Vigorf.A detections can be confusing. Many are false positives from legitimate software. But when it’s real malware, it’s serious business that requires immediate action.
The key is knowing the difference. If you just installed software and got this detection, it’s probably safe. If it appeared randomly with system problems, treat it as real malware.
Manual removal works for most cases. But professional tools make the job easier and more thorough. Don’t take chances with your computer’s security.
Remember these important points:
- Investigate before you delete anything
- Use multiple scanners for verification
- Keep your system updated and protected
- Back up important files regularly
Stay vigilant against similar threats like Yomal variants and social engineering attacks that often distribute trojan malware.
Vigorf.A Detection
- Trojan.U.Vigorf.bot: e5483bc99c7671654de3e4b2355a2709a4d86ef506b4e9baa119edc5df70d8e2