What is the Deadliest Virus in History?
On November 11, 1983, the first virus was written, which ushered in a new era of dangerous programs for computers. An American student at the University of Southern California, Fred Cohen, wrote a program that demonstrated the ability to infect a computer at a virus reproduction rate of 5 minutes to 1 hour.
The first non-lab virus, called “Brain,” capable of infecting only floppy disks, appeared in January 1986 and was of Pakistani origin. And the first antivirus program was developed in 1988. The following year, Cohen wrote a paper in which he anticipated the dangers of viruses spreading through computer networks and talked about the possibility of creating antivirus programs. Let us remember which viruses were the most destructive in the short history of computer networks.
MyDoom virus
The first version of the worm, MyDoom, appeared on January 26, 2004, and was distributed via e-mail and peer-to-peer networks. The program was written in C++. It created a backdoor (a flaw in the algorithm deliberately put there by the programmer) in the victim’s operating system and triggered a denial of service (DDoS) mechanism. Within a very short time the worm had invaded the Internet, and in 2004 about 16 – 25% of all e-mails were infected with MyDoom. The worm’s host file weighs only a few tens of kilobytes and contains the following line: “sync-1.01; andy; I’m just doing my job, nothing personal, sorry.” When infected, the worm modifies the operating system, blocking access to sites of antivirus companies, news feeds, and various sections of the Microsoft portal. It attacked DDoS in February of the same year.
In 2011, McAfee recognized MyDoom as the most “expensive” malware in history: losses associated with infection by the virus due to major spam campaigns ultimately amounted to $38 billion. Researchers note that MyDoom is entirely self-sufficient and autonomous. The worm can spread forever if people keep opening email attachments.
CryptoLocker
Ransomware appeared in September 2013. The virus was spread via email. Once the user opened the email, a program attached to it automatically launched and encrypted all the files on the PC. To restore access to the files, the victim had to pay a not-insignificant sum in bitcoins. After paying, the user should have received a private key to restore access to the files. However, people did not know that once infected, the files are lost forever. To avoid getting infected with the CryptoLocker virus, you should:
- First, constantly update your antivirus software.
- Ignore suspicious emails with attachments; do not click on random unrecognized links.
- Finally, backup your files regularly.
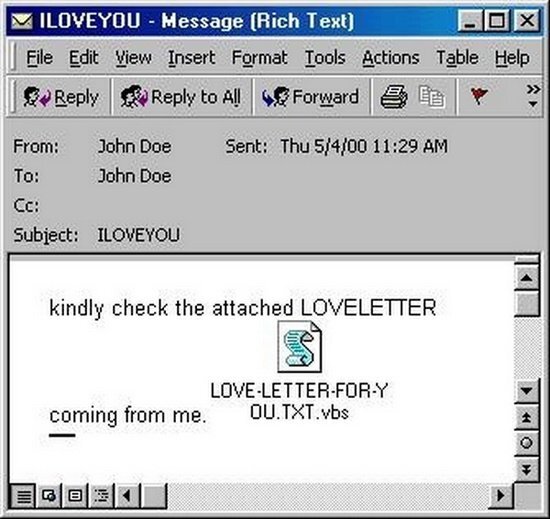
ILOVEYOU virus
After the victim opened the attachment, the virus sent a copy of itself to all contacts in the Windows address book and the address specified as the sender’s address. It also made some malicious changes to the user’s system. The virus was sent out to mailboxes from the Philippines on May 4-5, 2000; the subject line contained the “ILoveYou,” and the script “LOVE-LETTER-FOR-YOU.TXT.vbs” was attached to the letter. The “.vbs” extension was hidden by default, which made unsuspecting users think it was a simple text file. In total, the virus affected more than 3 million computers worldwide. The estimated damage the worm caused to the global economy is estimated at $10 – 15 billion, for which it entered the Guinness Book of World Records as the most destructive computer virus in the world.
Morris Worm
The Morris worm is considered the virus that started it all. The first computer worm’s widespread use in the real world was much more destructive and spread faster than expected. In 1988, a virus-infected a network of 60,000 computers (about 10% of the UNIX machines of the time), preventing them from functioning correctly. The worm did not destroy the files, but it was throwing punches. Vital military and university functions were severely slowed down. Emails were delayed for days. The damage from the Morris worm was estimated at $96.5 million.
The creator of the virus, Robert Morris, had kept the program code well hidden, and it was unlikely that anyone could prove his involvement. He used a loophole in the Internet email system and a bug in the “finger” program that identified network users. It was also designed to remain hidden. But his father, a computer expert for the National Security Agency, felt it was better for his son to confess to everything. At trial, Robert Morris faced up to five years in prison and a $250,000 fine. However, considering extenuating circumstances, the court sentenced him to a $10,000 fine and 400 hours of community service.
Melissa virus
“An $80 Million Cyber Crime in 1999” – FBI Mellisa was distributed under the guise of a plain text document, which, when opened, was passed on to the victim’s first 50 email contacts. The document contained information that could interest users: passwords for access to pay sites or links to popular cartoon series. The program was not designed to steal money or information, but it caused quite a bit of damage. The virus hit more than 300 corporations and government agencies, including IT giant Microsoft, which shut down several times due to email overload. In addition, the malware generated enormous Internet traffic and slowed down already overloaded servers. Although it was localized within days, the damage had already been done. At a conservative estimate, about $80 million was spent to clean up and repair the damage caused by the program.
Zeus
Zeus/Zbot is a malicious package that uses the client/server model. It is used to create massive botnets. It was first detected in 2011. This application is a type of malware targeting the Microsoft Windows operating system. The two main methods of infection are spam messages and hidden downloads. The primary purpose of Zeus is to gain access to confidential details of a victim’s bank account and debit it. The virus can bypass the protection of centralized server systems and scan the user’s personal information. Users can’t even trace the channels their stolen data travels through. Also, in some cases, Zeus can download ransomware that encrypts files and demands money in exchange for unlocking them. Zeus has infected about 3 million computers in the U.S. and compromised significant organizations, including NASA and Bank of America.
Technically, Zeus is a Trojan, a malware masquerading as legitimate software. It uses keylogging and website tracking to steal passwords and financial data. For example, when a banking site is used, or a financial transaction is made, it can record keystrokes during authorization. Zeus initially only worked on Windows, but now some variants can compromise Android phones.
Code Red
The Code Red worm was first discovered by two eEye Digital Security employees, Mark Meiffret and Ryan Perme. They named the found malware after their favorite soda, Code Red Mountain Dew. Appearing in 2001, it targeted computers with the Microsoft IIS Web server installed. By infiltrating the computer, Code Red makes hundreds of copies of all the data. Eventually, it consumes so many resources that the system fails and crashes. A denial-of-service attack algorithm is then launched, and remote access to the infected server is granted via a backdoor.
The most famous Code Red cyber attack was the attack on the White House website. That same year, 2001, the red worm infected more than 250,000 computer systems. According to experts, it resulted in lost productivity and a whopping $2 billion damage.
Microsoft developed a “patch” designed to protect computers specifically against Code Red to keep government agencies and the general public safe from this malware.
Stuxnet
The Stuxnet worm appeared online in 2010 and initially targeted Iran’s nuclear facilities. The virus destroyed more than 1,000 centrifuges at Iran’s Natanz uranium enrichment facility, an affiliate of the large company Foolad Technic. Stuxnet spreads via USB sticks and Windows computers. The Stuxnet Trojan is based on a search for a specific model of the programmable logic controller (PLC) manufactured by Siemens. These small industrial control systems perform all sorts of automated processes, such as those in chemical plants, manufacturing plants, oil refineries, and nuclear power plants. Computers control these PLCs, which is the Stuxnet worm’s primary target. It has been reported that the worm has already infected more than 50,000 computers. The German company Siemens said 14 infected control systems were mainly in Germany.
Conficker
The Conficker worm was first attacked in early 2009. Within days it had infected ten million computers. The botnet formed by the infected computers was one of the largest in the world. Microsoft offered a reward of $250,000 for information that could help catch the author or authors of Conficker. Microsoft also agreed to partner with several organizations to take down the worm. This rapid spread of the worm is related to a network service. Using a vulnerability in it, the worm downloaded itself from the Internet.
Interestingly, the developers of the worm learned how to constantly change its servers, and something attackers had not managed to do before. Also, the worm spread itself via USB sticks, creating an executable autorun.inf file and a RECYCLED\{SID}\RANDOM_NAME.vmx file. On the infected system, the worm logged itself into services. It was stored as a DLL file with a random name consisting of Latin letters. The worm took advantage of a buffer overflow in a Windows operating system and executed a malicious code with a bogus RPC request. It also disabled some services, such as Windows Automatic Updates, Windows Security Center, Windows Defender, and Windows Error Reporting. It blocked access to the websites of several antivirus vendors.
As you can see, all of the viruses discussed above appeared at the beginning of the 21st century, when most modern cybersecurity technologies were in their infancy. Now the situation has fundamentally changed. Modern operating systems and advanced antivirus applications protect against most malware. However, we should not relax because even malware from this list is still roaming the net. On the other hand, rampant cybercrime leads to an ever-increasing need for protection specialists.




